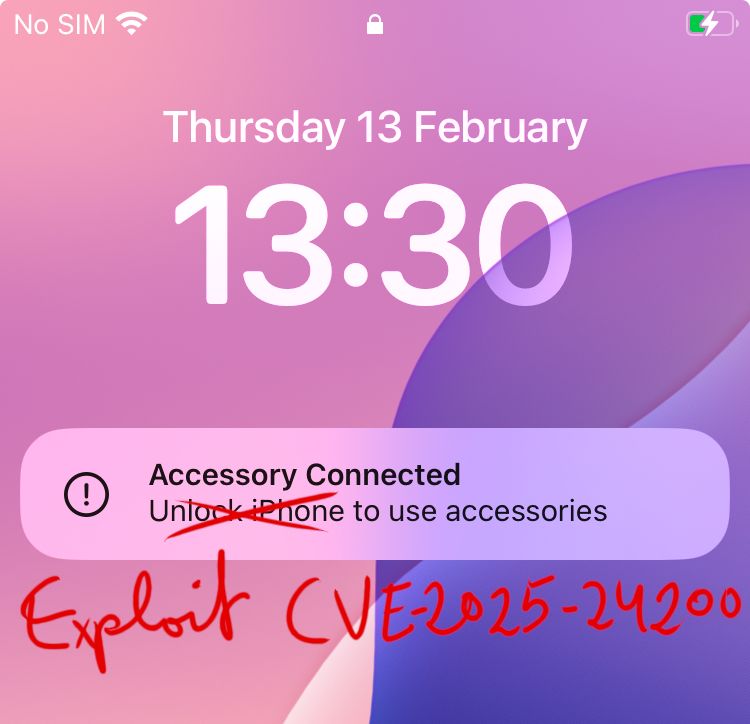
Hacking into Apple's new USB-C Controller: media.ccc.de/v/38c3-ace-u...
Hacking into Apple's new USB-C Controller: media.ccc.de/v/38c3-ace-u...
www.mobile-hacker.com/2024/12/02/c...
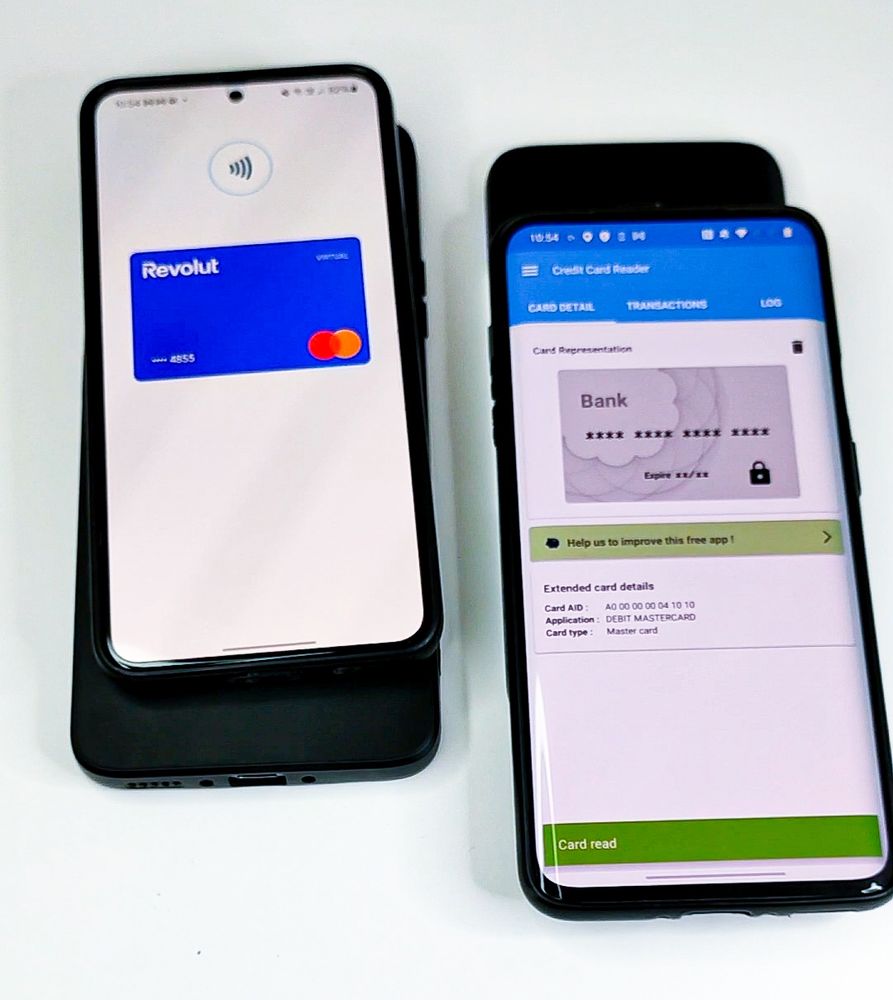
www.mobile-hacker.com/2024/12/02/c...
Particularly if you are testing a 72 hour time out - each new go is 72 more hours! Thanks to Nick Dubois for his testing of the iOS inactivity feature that causes iOS devices to reboot.
www.hexordia.com/blog/ios18-r...

We have a good idea of what's happening here based on the detailed info we obtained about MSAB's XRY exploit tool. We reported those exploits to Google in January 2024 with multiple proposals on how to stop it. April 2024 is when the first 2 shipped.
We have a good idea of what's happening here based on the detailed info we obtained about MSAB's XRY exploit tool. We reported those exploits to Google in January 2024 with multiple proposals on how to stop it. April 2024 is when the first 2 shipped.
I reverse engineered the kernel extension and the secure enclave processor, where this feature is implemented.
naehrdine.blogspot.com/2024/11/reve...

I reverse engineered the kernel extension and the secure enclave processor, where this feature is implemented.
naehrdine.blogspot.com/2024/11/reve...
source.android.com/docs/securit... source.android.com/docs/securit...
These are assigned CVE-2024-29745 / CVE-2024-29748.
source.android.com/docs/securit... source.android.com/docs/securit...
These are assigned CVE-2024-29745 / CVE-2024-29748.

