buff.ly/Crz8rDh

buff.ly/Crz8rDh
buff.ly/agWWCnp

buff.ly/agWWCnp
buff.ly/mpEzALh

buff.ly/mpEzALh
Part 1: buff.ly/mpEzALh
Part 2: buff.ly/agWWCnp
Part3: buff.ly/Crz8rDh
🎄 Last part following Monday! 🎄

Part 1: buff.ly/mpEzALh
Part 2: buff.ly/agWWCnp
Part3: buff.ly/Crz8rDh
🎄 Last part following Monday! 🎄
Sekoia #TDR analysed a recent #Calisto (aka #ColdRiver #Star Blizzard) spear-phishing campaign aimed at Reporters sans frontières and other #Ukraine-supporting organisations.
blog.sekoia.io/ngo-reporter...

Sekoia #TDR analysed a recent #Calisto (aka #ColdRiver #Star Blizzard) spear-phishing campaign aimed at Reporters sans frontières and other #Ukraine-supporting organisations.
blog.sekoia.io/ngo-reporter...

We also detailed the fraud scheme targeting hotel customers.

We also detailed the fraud scheme targeting hotel customers.
blog.sekoia.io/phishing-cam...

blog.sekoia.io/phishing-cam...
Our Sekoia #TDR report breaks down the full infection chain and stealthy WebSocket C2 communications .
Read more 👉 blog.sekoia.io/transparentt...

Our Sekoia #TDR report breaks down the full infection chain and stealthy WebSocket C2 communications .
Read more 👉 blog.sekoia.io/transparentt...
blog.sekoia.io/userauthenti...

blog.sekoia.io/userauthenti...
blog.sekoia.io/polaredge-ba...

blog.sekoia.io/polaredge-ba...
✉️ API exploitation: attackers leverage an exposed /cgi endpoint to push malicious SMS without authentication
🌐 Scale of exposure: over 18,000 routers accessible on the internet; 572 confirmed vulnerable

✉️ API exploitation: attackers leverage an exposed /cgi endpoint to push malicious SMS without authentication
🌐 Scale of exposure: over 18,000 routers accessible on the internet; 572 confirmed vulnerable
Our latest #CTI investigation from Sekoia #TDR team uncovers a novel #smishing vector abusing Milesight industrial cellular router APIs to send phishing #SMS at scale.
blog.sekoia.io/silent-smish...

Our latest #CTI investigation from Sekoia #TDR team uncovers a novel #smishing vector abusing Milesight industrial cellular router APIs to send phishing #SMS at scale.
blog.sekoia.io/silent-smish...
🎯 The campaign’s goal is to gather cyber intelligence on frontline combatants by targeting administrative and logistics personnel.

🎯 The campaign’s goal is to gather cyber intelligence on frontline combatants by targeting administrative and logistics personnel.
🕷️ Attackers deploy a custom backdoor dubbed BeardShell using a modified Covenant Grunt stager.

🕷️ Attackers deploy a custom backdoor dubbed BeardShell using a modified Covenant Grunt stager.
blog.sekoia.io/apt28-operat...

blog.sekoia.io/apt28-operat...
➡️ blog.sekoia.io/predators-fo...
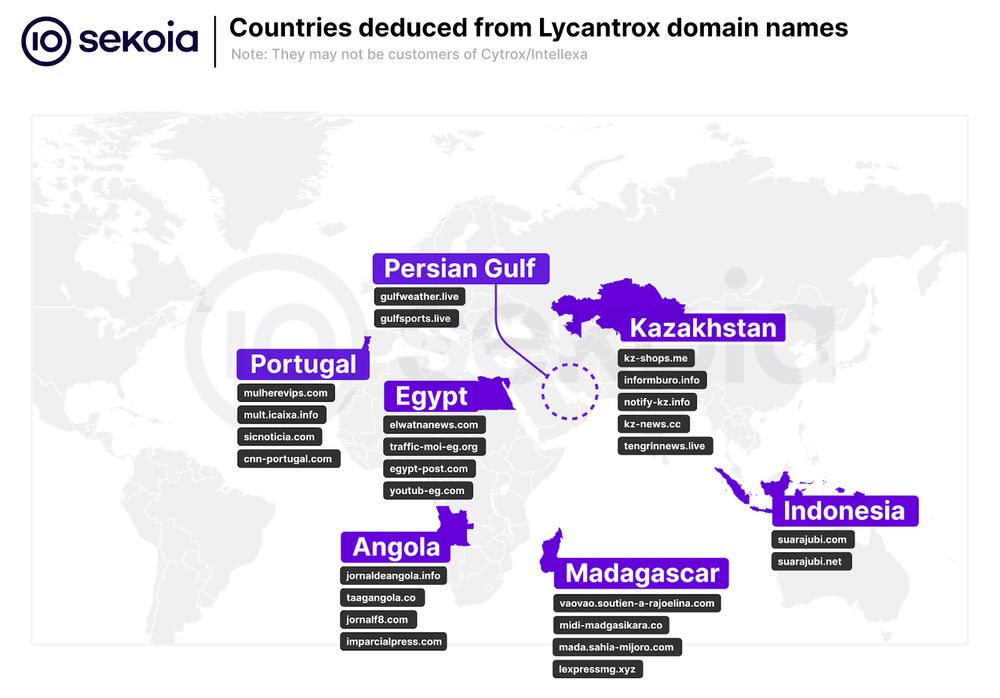
➡️ blog.sekoia.io/predators-fo...
Unlike before, they're not impersonating a real crypto company. Instead, they have built a completely #fake brand from scratch: https://waventic[.]com.
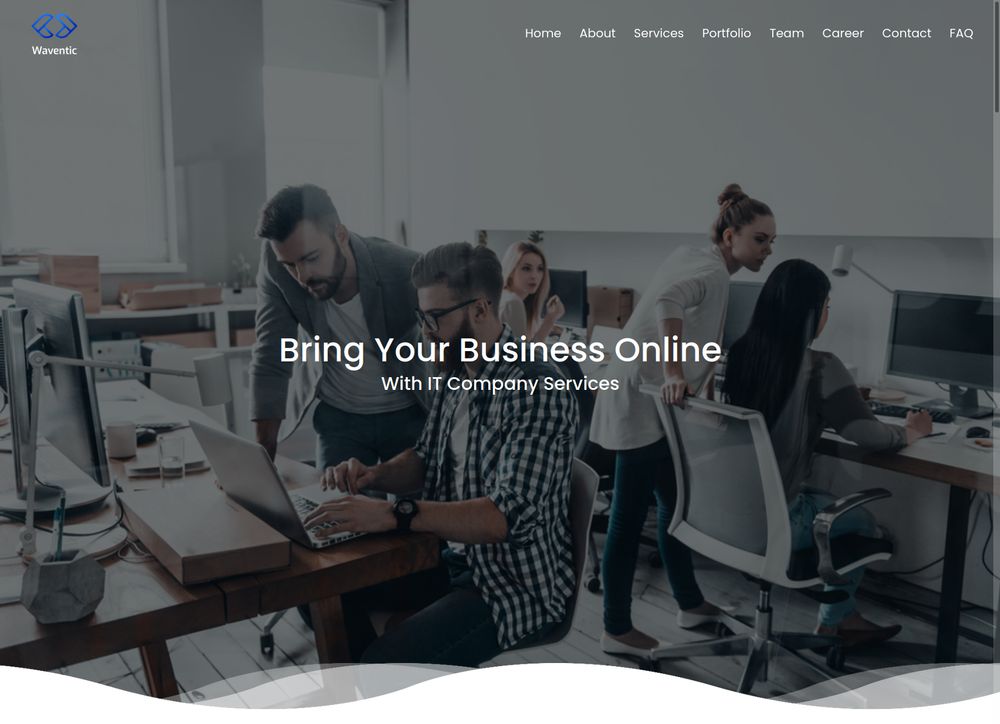
Unlike before, they're not impersonating a real crypto company. Instead, they have built a completely #fake brand from scratch: https://waventic[.]com.
Back in March, Sekoia #TDR team published a deep-dive report on a #Lazarus cluster we dubbed #ClickFake Interview, leveraging the #ClickFix technique in their #ContagiousInterview campaign.

Back in March, Sekoia #TDR team published a deep-dive report on a #Lazarus cluster we dubbed #ClickFake Interview, leveraging the #ClickFix technique in their #ContagiousInterview campaign.
All technical details are available on our community GitHub: buff.ly/v5Y6amN

All technical details are available on our community GitHub: buff.ly/v5Y6amN
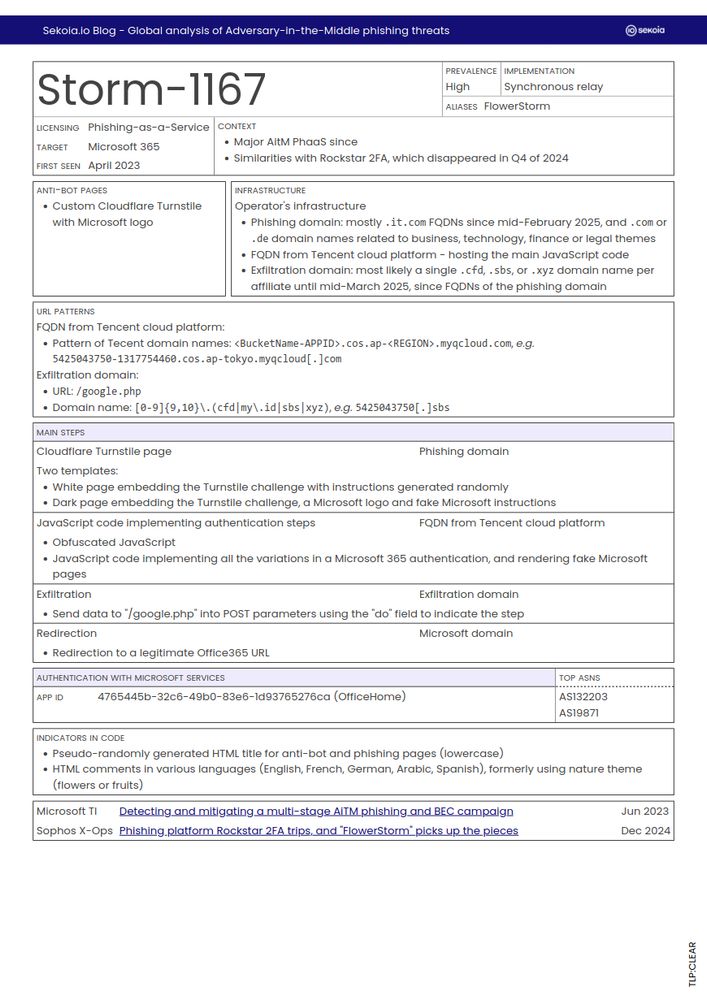
Additionally, the article includes summary sheets covering 11 AitM phishing kits.

Additionally, the article includes summary sheets covering 11 AitM phishing kits.
In our new blogpost, we provide an overview of the key techniques, tactics and social engineering schemes that cybercriminals use in AitM phishing attacks.

In our new blogpost, we provide an overview of the key techniques, tactics and social engineering schemes that cybercriminals use in AitM phishing attacks.