
Over the last year, stealing cookies on Windows devices has changed significantly for Chromium browsers like Chrome and Edge. Andrew Gomez dives into these changes, how threat actors adapt, & new detection opportunities. ghst.ly/45S1ZgW

Over the last year, stealing cookies on Windows devices has changed significantly for Chromium browsers like Chrome and Edge. Andrew Gomez dives into these changes, how threat actors adapt, & new detection opportunities. ghst.ly/45S1ZgW
github.com/N1ckDunn/SOS...
github.com/N1ckDunn/SOS...
But let’s keep all dependencies on US IT alive. What could possibly go wrong?
www.techzine.eu/news/privacy...

But let’s keep all dependencies on US IT alive. What could possibly go wrong?
www.techzine.eu/news/privacy...

You should probably be aware that someone has compromised your organization and has attempted to notify you.
They wrote to your I.T. department, but it was ignored. You should (probably) fix it.

You should probably be aware that someone has compromised your organization and has attempted to notify you.
They wrote to your I.T. department, but it was ignored. You should (probably) fix it.
The 0day impacts an organization which provides managed services for Danone, SeaGate, Unity, Shopify, Paramount Pictures, HubSpot, Amazon, PWC, Yamaha, L'Oreal
The exploit was reported, but the vendor ignored it.
Chat, do we drop a 0day on a Friday?
The 0day impacts an organization which provides managed services for Danone, SeaGate, Unity, Shopify, Paramount Pictures, HubSpot, Amazon, PWC, Yamaha, L'Oreal
The exploit was reported, but the vendor ignored it.
Chat, do we drop a 0day on a Friday?
A few more stories like this and I recon not a single hacker from outside of the US wants to go to DefCon.
He was held with 100 people including many Canadians.
Posters celebrating equity had DEI scribbled out in marker.

A few more stories like this and I recon not a single hacker from outside of the US wants to go to DefCon.
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31

Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31

learn.microsoft.com/en-us/opensp...

learn.microsoft.com/en-us/opensp...
Raphael is right on many things, especially for the bad press he got from people just blatantly shouting things without knowing the actual facts and details.
But most important: Rafi, its great to have your voice back in the community!
What I didn't say: I feel compelled, even though I DON'T want the bullshit, to try and fix it.
What does all of this mean?
Raphael is right on many things, especially for the bad press he got from people just blatantly shouting things without knowing the actual facts and details.
But most important: Rafi, its great to have your voice back in the community!
The countdown to BSidesABQ is on.

The countdown to BSidesABQ is on.
Check out our latest blog post from @unsignedsh0rt.bsky.social to learn more. ghst.ly/4buoISp
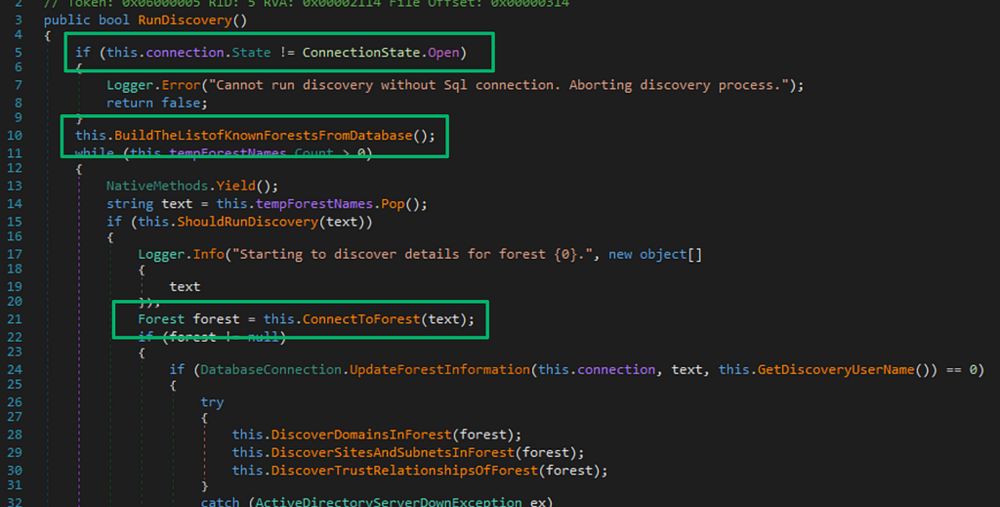
Check out our latest blog post from @unsignedsh0rt.bsky.social to learn more. ghst.ly/4buoISp
Check it out 👇
casvancooten.com/posts/2025/0...

Check it out 👇
casvancooten.com/posts/2025/0...
Read about the latest @outflank.bsky.social research on using Secure Enclaves in Windows for offensive ops — plus fresh insights for red teamers.
Check out Part 1 of our blog series here: www.outflank.nl/blog/2025/02...

Read about the latest @outflank.bsky.social research on using Secure Enclaves in Windows for offensive ops — plus fresh insights for red teamers.
Check out Part 1 of our blog series here: www.outflank.nl/blog/2025/02...
In his latest blog post, Dan Mayer intros his new PR to SlackPirate that lets you loot Slack again out of the box, a BOF to get you all the data you need to do it, & how to bee the most active slacker in your group chat. 🐝 ghst.ly/4hgwMIt

In his latest blog post, Dan Mayer intros his new PR to SlackPirate that lets you loot Slack again out of the box, a BOF to get you all the data you need to do it, & how to bee the most active slacker in your group chat. 🐝 ghst.ly/4hgwMIt
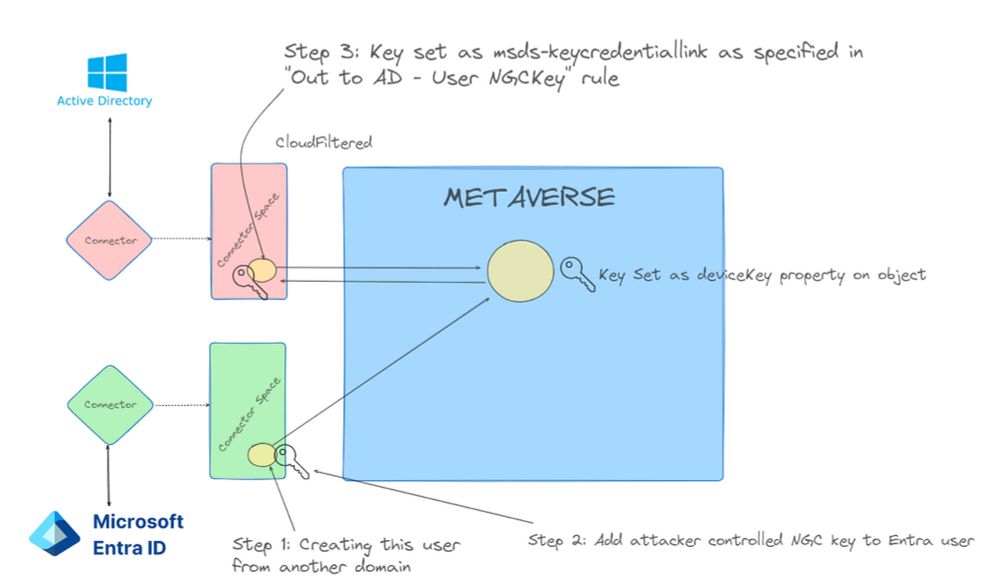

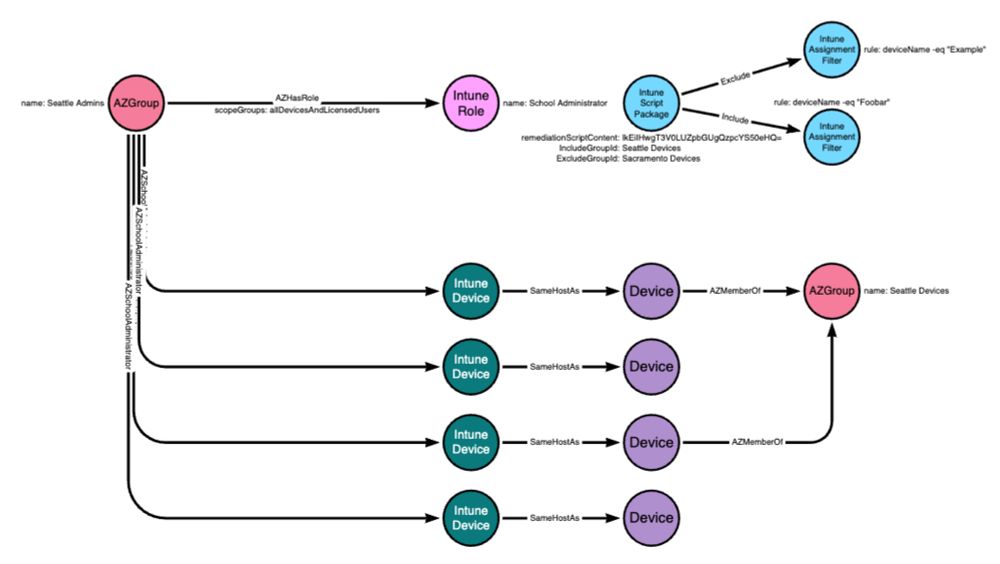
jsecurity101.medium.com/behind-the-m...
jsecurity101.medium.com/behind-the-m...

