
🌏 " वसुधैव कुटुम्बकम् " - " The World Is One Family " 🌍
Connect Securely 🔐 --> threema.id/XENJFKT6
2/2

2/2
3/4

3/4
2/4

2/4
The labels on several packages, however, carried “EXP: 10/2024”, prompting widespread accusations that Pakistan had shipped expired products.

The labels on several packages, however, carried “EXP: 10/2024”, prompting widespread accusations that Pakistan had shipped expired products.

If the SIM was removed/inactive, the app must stop working.
Web–like services must log out every 6 hours, if the SIM isn’t verified
Apps have 90 days to follow these rules.

If the SIM was removed/inactive, the app must stop working.
Web–like services must log out every 6 hours, if the SIM isn’t verified
Apps have 90 days to follow these rules.
1/8

1/8
They used Yandex Cloud, OneDrive, and even social media to steal data without raising alarms.
Some attacks ran on holidays when no one was watching.

They used Yandex Cloud, OneDrive, and even social media to steal data without raising alarms.
Some attacks ran on holidays when no one was watching.
1/5

1/5
🇮🇷 The Actors: Iran-linked groups like Imperial Kitten (IRGC affiliated) and MuddyWater (MOIS affiliated).
2/7

🇮🇷 The Actors: Iran-linked groups like Imperial Kitten (IRGC affiliated) and MuddyWater (MOIS affiliated).
2/7
Amazon security experts confirm a terrifying new reality: Nation-state hackers are now directly coordinating cyber reconnaissance with physical military strikes. They call this "Cyber-Enabled Kinetic Targeting."
1/7
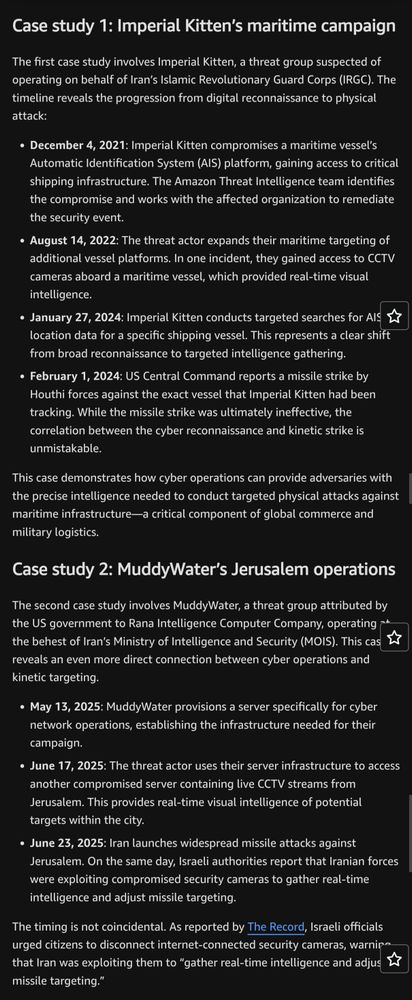
Amazon security experts confirm a terrifying new reality: Nation-state hackers are now directly coordinating cyber reconnaissance with physical military strikes. They call this "Cyber-Enabled Kinetic Targeting."
1/7
So they are normalising #WorkspaceSnooping - so your employer will now be able to read your RCS chats in Google Messages despite encryption.
1/2

So they are normalising #WorkspaceSnooping - so your employer will now be able to read your RCS chats in Google Messages despite encryption.
1/2
Read 🔗 go.aps.org/3WZl7FI

Read 🔗 go.aps.org/3WZl7FI
4/4

4/4
3/4

3/4
10/10

10/10
9/10

9/10
5/10

5/10
3/8

3/8
Social engineering is the key here...
1/2

Social engineering is the key here...
1/2
1/6

1/6

5/5


5/5
4/5


4/5


