"The first instance of unauthorized access by the threat actor was a successful RDP logon to the beachhead host, a publicly exposed RDP server. The logon was performed using valid credentials, and...
1/3

"The first instance of unauthorized access by the threat actor was a successful RDP logon to the beachhead host, a publicly exposed RDP server. The logon was performed using valid credentials, and...
1/3
All files involved in the initial access phase were signed with valid certificates.

All files involved in the initial access phase were signed with valid certificates.
The challenge is complete! A massive thank you to everyone who participated in our latest DFIR Challenge!
Big shoutout to the top finishers who untangled the whole thing:
🥇 Jason Phang Vern Onn
🥈 Marko Yavorskyi
🥉 Bohdan Hrondzal


The challenge is complete! A massive thank you to everyone who participated in our latest DFIR Challenge!
Big shoutout to the top finishers who untangled the whole thing:
🥇 Jason Phang Vern Onn
🥈 Marko Yavorskyi
🥉 Bohdan Hrondzal
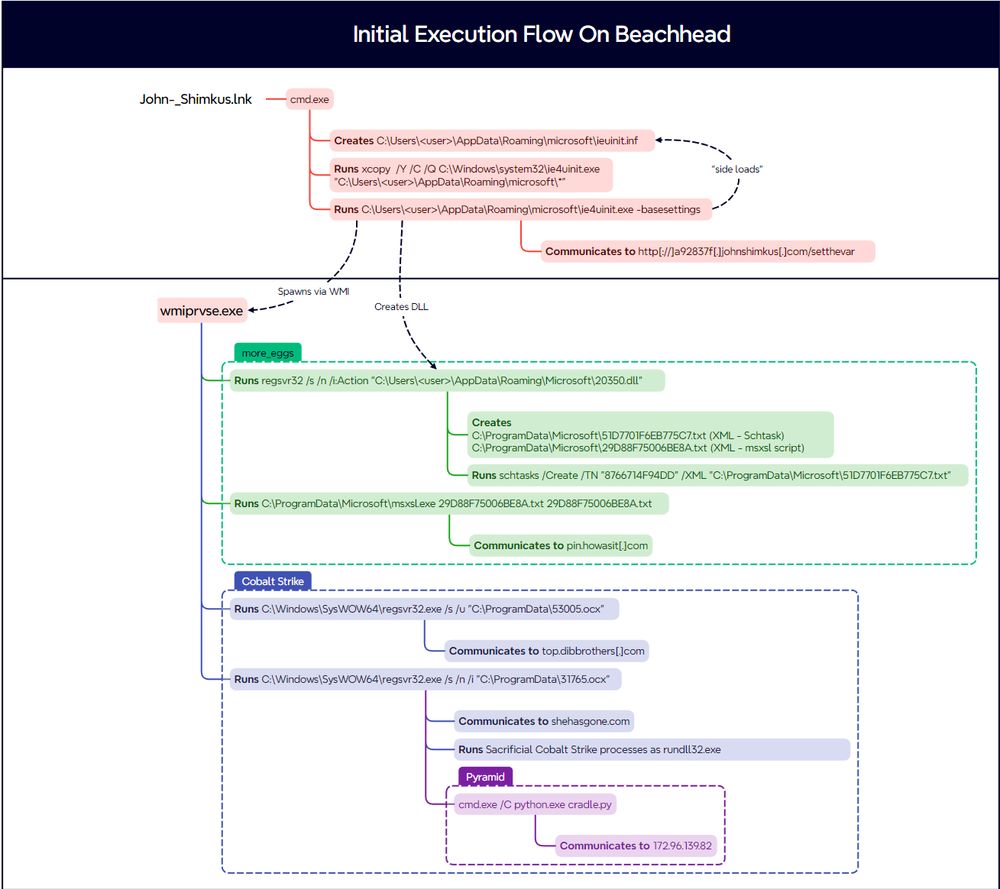
From a Single Click: How Lunar Spider Enabled a Near Two-Month Intrusion
Analysis/reporting completed by @RussianPanda, Christos Fotopoulos, Salem Salem, reviewed by @svch0st.
Audio: Available on Spotify, Apple, YouTube and more!
Report:⬇️

From a Single Click: How Lunar Spider Enabled a Near Two-Month Intrusion
Analysis/reporting completed by @RussianPanda, Christos Fotopoulos, Salem Salem, reviewed by @svch0st.
Audio: Available on Spotify, Apple, YouTube and more!
Report:⬇️
Of note, the image 2.jpg that was alongside the payload in the .zip was not used by the malware. We assess that it was likely used to “pad” the..."
Of note, the image 2.jpg that was alongside the payload in the .zip was not used by the malware. We assess that it was likely used to “pad” the..."
The first binary, GT_NET.exe is associated with Grixba, a custom data-gathering tool used by the Play ransomware group. Its metadata was crafted to..."

The first binary, GT_NET.exe is associated with Grixba, a custom data-gathering tool used by the Play ransomware group. Its metadata was crafted to..."
The trojanized installer was a downloader, more publicly known as “d3f@ckloader”, and is..."

The trojanized installer was a downloader, more publicly known as “d3f@ckloader”, and is..."

Blurring the Lines: Intrusion Shows Connection With Three Major Ransomware Gangs
Analysis and reporting completed by @r3nzsec, @EncapsulateJ, @rkonicekr, & Adam Rowe
Audio: Available on Spotify, Apple, YouTube and more!
Report:⬇️

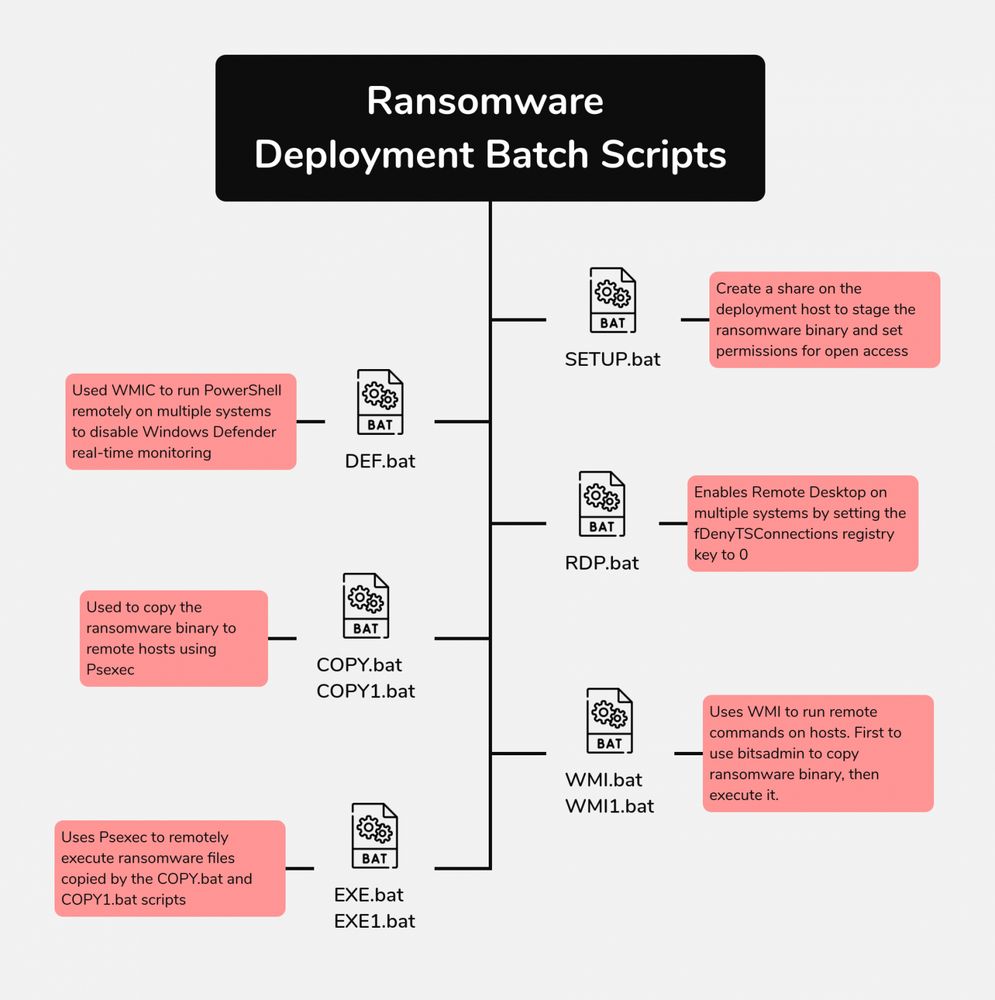
Blurring the Lines: Intrusion Shows Connection With Three Major Ransomware Gangs
Analysis and reporting completed by @r3nzsec, @EncapsulateJ, @rkonicekr, & Adam Rowe
Audio: Available on Spotify, Apple, YouTube and more!
Report:⬇️
This lab is based on a detailed intrusion from our private case repositories 👇
📥 Workstation Compromise ➡️ Persistent Access ➡️ Discovery➡️ Privilege Escalation ➡️ Lateral Movement ➡️ Data Exfil
Link 👇

This lab is based on a detailed intrusion from our private case repositories 👇
📥 Workstation Compromise ➡️ Persistent Access ➡️ Discovery➡️ Privilege Escalation ➡️ Lateral Movement ➡️ Data Exfil
Link 👇
We dive into our latest public report with Randy Pargman, Jake Ouellette, Kostas T., and Mangatas Tondang.
Stay tuned for deep insights, behind-the-scenes analysis, and expert commentary from the front lines of DFIR. 🔍
We dive into our latest public report with Randy Pargman, Jake Ouellette, Kostas T., and Mangatas Tondang.
Stay tuned for deep insights, behind-the-scenes analysis, and expert commentary from the front lines of DFIR. 🔍
Big congrats to our winners!
🥇 @Friffnz — 5100 pts
🥈 snail — 4840 pts
🥉 forynsics — 4800 pts
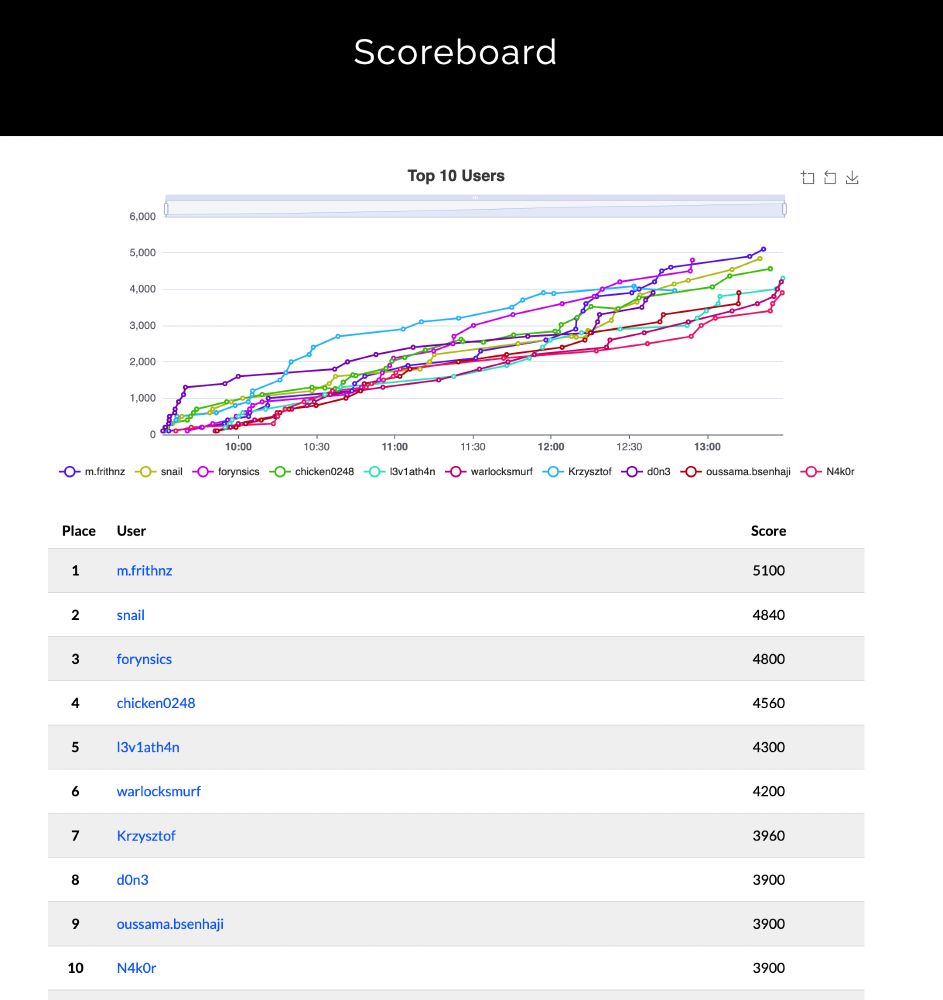
Big congrats to our winners!
🥇 @Friffnz — 5100 pts
🥈 snail — 4840 pts
🥉 forynsics — 4800 pts
The logic would rotate through the various servers until an online host was found.
1/3
#dfir #CyberSecurity #cyberthreatintelligence #cti #interlock #ransomware
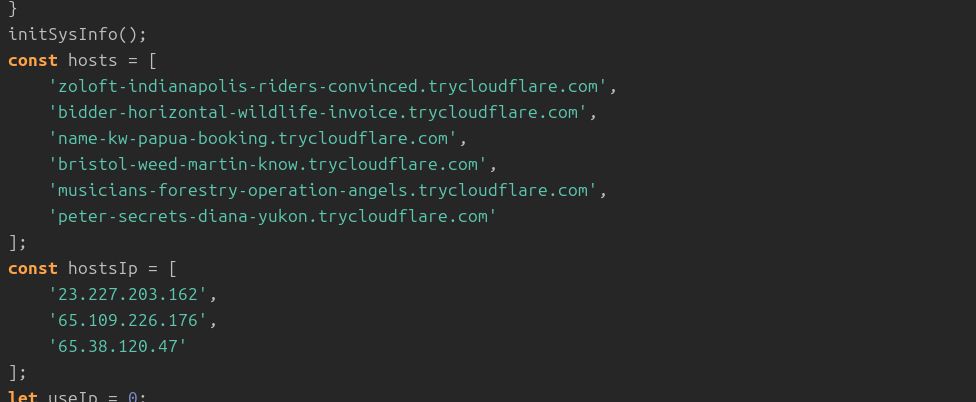
The logic would rotate through the various servers until an online host was found.
1/3
#dfir #CyberSecurity #cyberthreatintelligence #cti #interlock #ransomware
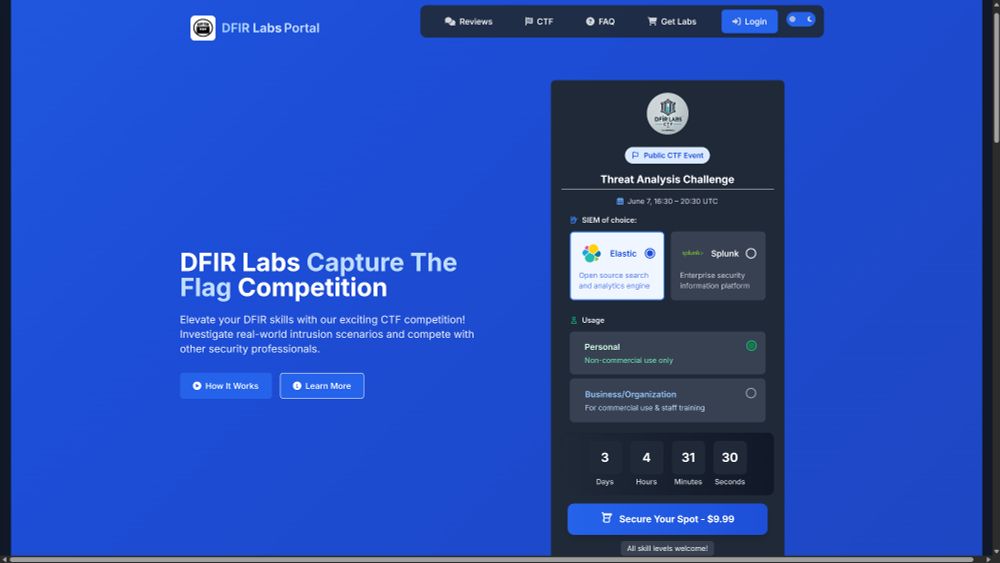
⏰ June 7 | 1630–2030 UTC
🔗 Register Now → dfirlabs.thedfirreport.com/ctf
🚀 DFIR Labs CTF is back!
💥 Only $9.99 to join
💥 Choose Elastic or Splunk
💥 Access a brand-new, unreleased case
💥 Top 5 get invited to join The DFIR Report team!
⏰ June 7 | 1630–2030 UTC
🔗 Register Now → dfirlabs.thedfirreport.com/ctf
🚀 DFIR Labs CTF is back!
💥 Only $9.99 to join
💥 Choose Elastic or Splunk
💥 Access a brand-new, unreleased case
💥 Top 5 get invited to join The DFIR Report team!
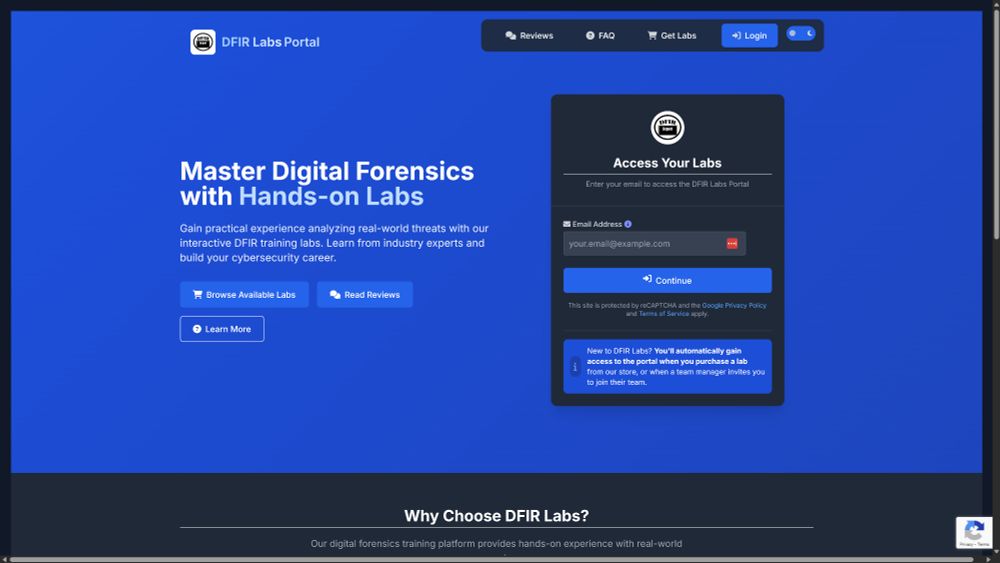
Big things are happening at DFIR Labs! We've been hard at work implementing a wave of exciting changes and improvements, all designed to enhance your experience!
➡️ Check it out now! dfirlabs.thedfirreport.com
Big things are happening at DFIR Labs! We've been hard at work implementing a wave of exciting changes and improvements, all designed to enhance your experience!
➡️ Check it out now! dfirlabs.thedfirreport.com
Check out real user testimonials on gaining critical, hands-on experience & see why they recommend our platform:
👇
thedfirreport.com/services/dfi...

Check out real user testimonials on gaining critical, hands-on experience & see why they recommend our platform:
👇
thedfirreport.com/services/dfi...
We're looking for volunteer analysts to join the team!
Ready to join the team? ➡️https://github.com/The-DFIR-Report/DFIR-Artifacts

We're looking for volunteer analysts to join the team!
Ready to join the team? ➡️https://github.com/The-DFIR-Report/DFIR-Artifacts
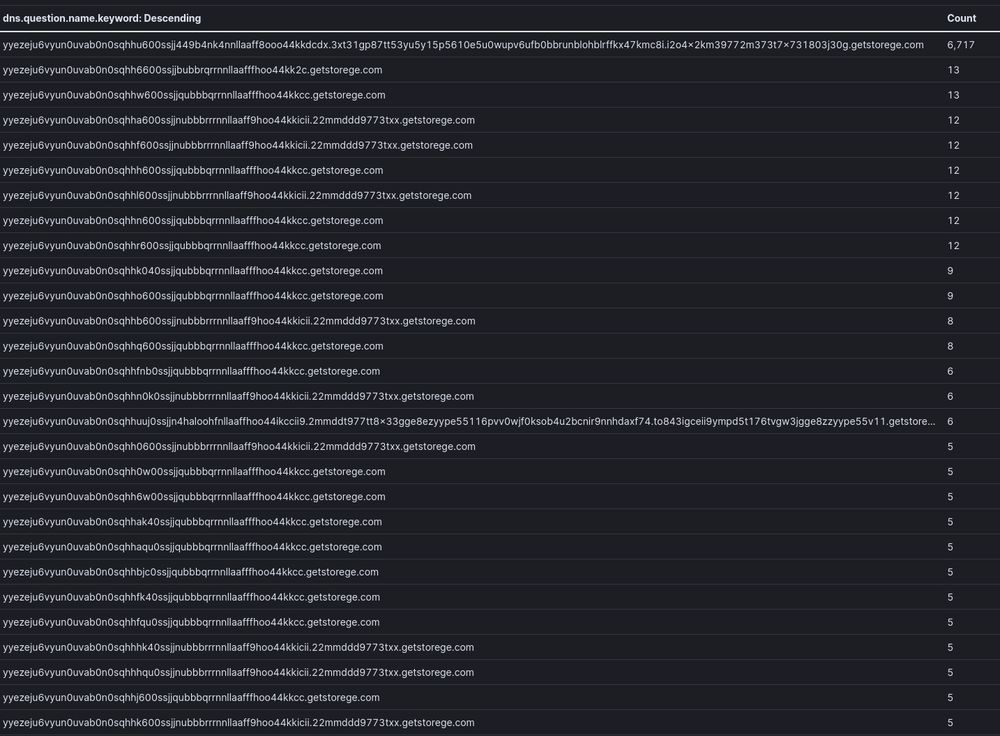
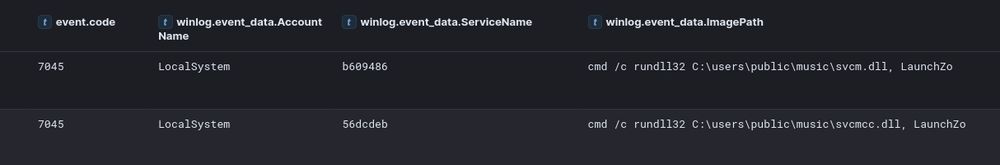
This can be identified by the "type: 16" in the Sysmon logs seen above. Below is a sample list that, while not exhaustive, provides a clear example of the traffic patterns:”
1/2
This can be identified by the "type: 16" in the Sysmon logs seen above. Below is a sample list that, while not exhaustive, provides a clear example of the traffic patterns:”
1/2
thedfirreport.com/services/dfi...
Congratulations to the winners so far for making it to the CTF Winners table! If you’ve placed in a past event, your name’s up there!

thedfirreport.com/services/dfi...
Congratulations to the winners so far for making it to the CTF Winners table! If you’ve placed in a past event, your name’s up there!
➡️TTR 7.5 hours
➡️Koadic and Empire for C2
➡️7+ Credential Access techniques
➡️ADRecon, APS, quser, arp, and nltest for Discovery
➡️RDP and PsExec for Lateral Movement
➡️Files exfiltrated
➡️PYSA ransomware for Impact
Report link ⬇️

➡️TTR 7.5 hours
➡️Koadic and Empire for C2
➡️7+ Credential Access techniques
➡️ADRecon, APS, quser, arp, and nltest for Discovery
➡️RDP and PsExec for Lateral Movement
➡️Files exfiltrated
➡️PYSA ransomware for Impact
Report link ⬇️
🥇1st Place: d1d1d1 @DreSecX
🥈2nd Place: mohan @imohanasundaram
🥉3rd Place: m.frithnz @Friffnz
We hope everyone enjoyed playing in our #DFIRLabsCTF!

🥇1st Place: d1d1d1 @DreSecX
🥈2nd Place: mohan @imohanasundaram
🥉3rd Place: m.frithnz @Friffnz
We hope everyone enjoyed playing in our #DFIRLabsCTF!
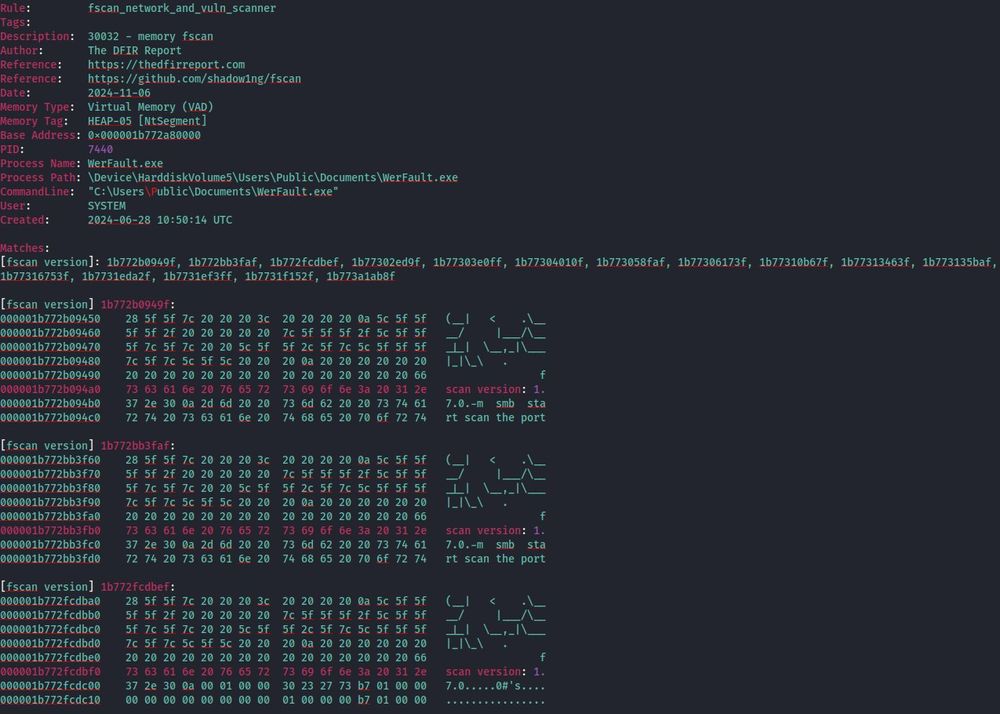
The commands and argument order point to the use of the scanning tool fscan."
2/3
The commands and argument order point to the use of the scanning tool fscan."
2/3
Targeted services included SSH, RDP, MySQL, MSSQL, FTP, and SMB."
1/3
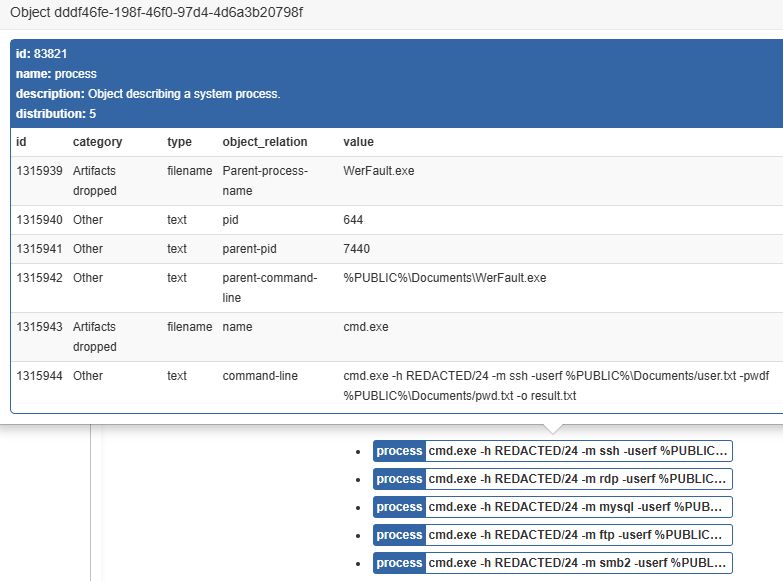
Targeted services included SSH, RDP, MySQL, MSSQL, FTP, and SMB."
1/3
🌟New report out Monday, January 27th by @r3nzsec, @MyDFIR & @MittenSec!
🌟New report out Monday, January 27th by @r3nzsec, @MyDFIR & @MittenSec!

