
🏳️🌈he/him🏳️🌈

They would have to automate the AMI rollout which, assuming folks aren't using pet EC2s, is not *that* complex. It's not easy but it's not "13% of EC2 spend" levels of complex either
They would have to automate the AMI rollout which, assuming folks aren't using pet EC2s, is not *that* complex. It's not easy but it's not "13% of EC2 spend" levels of complex either
This was also (one of the reasons) I was driven away from social media / dramatically reduced my public web presence too. The tech community is wildly toxic but the open-source fanatics are... a particular level of abhorrent
This was also (one of the reasons) I was driven away from social media / dramatically reduced my public web presence too. The tech community is wildly toxic but the open-source fanatics are... a particular level of abhorrent
That's surprisingly rare so... yeah, it'll remain a super-high-performing thing that few people talk about :(
That's surprisingly rare so... yeah, it'll remain a super-high-performing thing that few people talk about :(
One exception: on-boarding slowed a bit :lolsob: It was so hard getting new devs in and having them get used to "no, seriously, if checks are green we ship whatever to prod and it's fine! We have intense checks!"
One exception: on-boarding slowed a bit :lolsob: It was so hard getting new devs in and having them get used to "no, seriously, if checks are green we ship whatever to prod and it's fine! We have intense checks!"
I worked with a bunch of teams that did post-PR code reviews (if the code is under a feature flag => PR is automatically approved, merged, and deployed to prod) but the setup required was non-trivial 😞
Everybody (including compliance) was super-happy with it tho!
I worked with a bunch of teams that did post-PR code reviews (if the code is under a feature flag => PR is automatically approved, merged, and deployed to prod) but the setup required was non-trivial 😞
Everybody (including compliance) was super-happy with it tho!
AWS received feedback and they took super-prompt action to address it — awesome job AWS!
AWS received feedback and they took super-prompt action to address it — awesome job AWS!
There's even a preview for re:Invent 2024!
There's even a preview for re:Invent 2024!
Totally unexpected and not at all clear, right?
Don't you think this deserved a warning in the docs/announcement?
14/14
Totally unexpected and not at all clear, right?
Don't you think this deserved a warning in the docs/announcement?
14/14
See Internet Explorer, Apple, Google, Chrome, and all the new cases on this topic 🫠
13/14
See Internet Explorer, Apple, Google, Chrome, and all the new cases on this topic 🫠
13/14
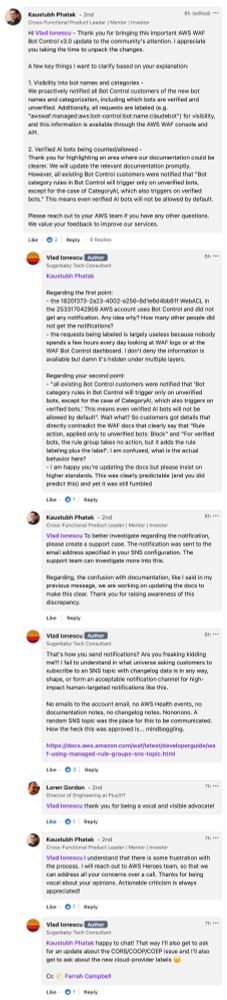
If AWS WAF Bot Control doesn't know how to check the bot is indeed who it's saying it is, that means that it could be an attacker pretending to be a bot, so it is blocked by default.
12/14
If AWS WAF Bot Control doesn't know how to check the bot is indeed who it's saying it is, that means that it could be an attacker pretending to be a bot, so it is blocked by default.
12/14
AWS WAF Bot Control is able to guarantee this is indeed the bot it's saying it is, so the request is neither blocked nor allowed.
11/14
AWS WAF Bot Control is able to guarantee this is indeed the bot it's saying it is, so the request is neither blocked nor allowed.
11/14

