
@EclecticIQ | Threat Hunter | Malware Analyst |. (All opinions expressed here are mine only). 🇹🇷🇳🇱
#cybersecurity
Europol took down servers for the Rhadamanthys infostealer, the VenomRAT, and the Elysium botnet

Europol took down servers for the Rhadamanthys infostealer, the VenomRAT, and the Elysium botnet

@likethecoins.bsky.social @campuscodi.risky.biz
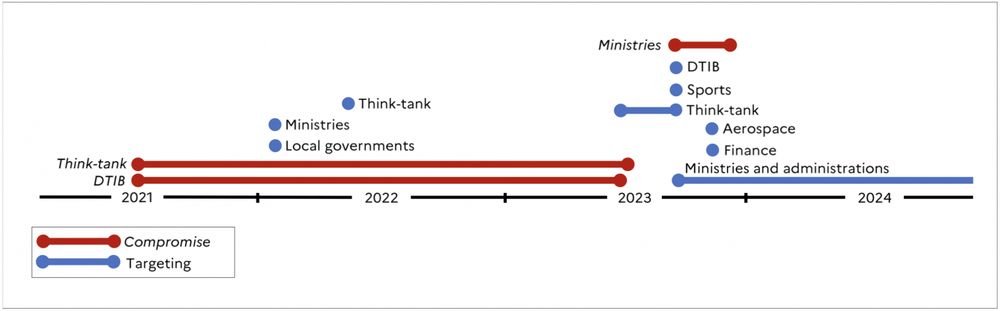
#CTI

@likethecoins.bsky.social @campuscodi.risky.biz
#CTI
Only NPM affected. I've sent an email off to @npmjs.bsky.social to see if I can get access again.
Sorry everyone, I should have paid more attention. Not like me; have had a stressful week. Will work to get this cleaned up.
Only NPM affected. I've sent an email off to @npmjs.bsky.social to see if I can get access again.
Sorry everyone, I should have paid more attention. Not like me; have had a stressful week. Will work to get this cleaned up.

The *chef's kiss* here is the name of the site: Panama Playlists 😆
panamaplaylists.com
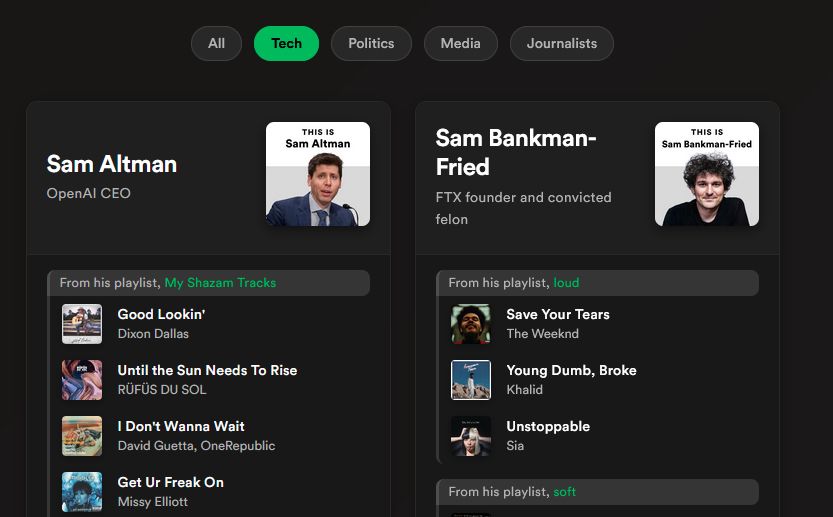
The *chef's kiss* here is the name of the site: Panama Playlists 😆
panamaplaylists.com
www.gov.uk/government/n...
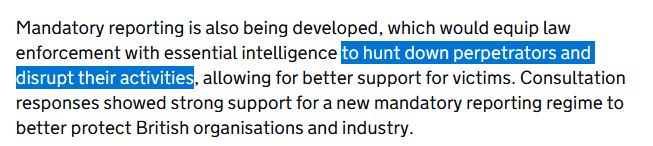
www.gov.uk/government/n...
margin.re/mobilizing-c...
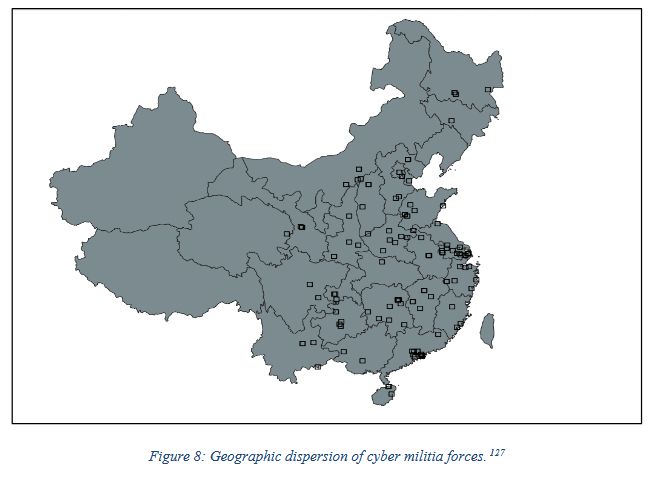
margin.re/mobilizing-c...
#Ivanti #GreyNoise #Cybersecurity #ZeroDays
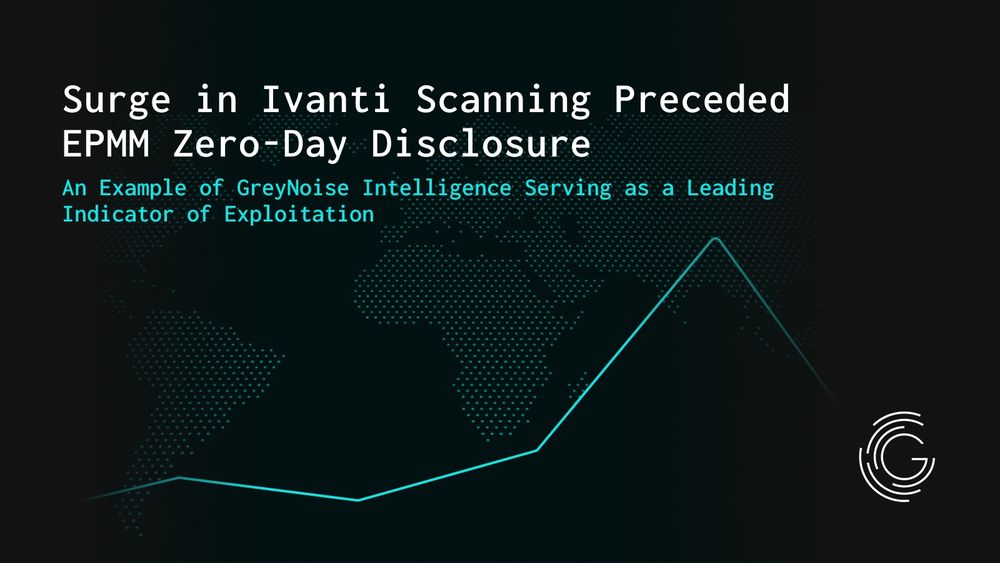
#Ivanti #GreyNoise #Cybersecurity #ZeroDays
via @jgreig.bsky.social & @therecordmedia.bsky.social

via @jgreig.bsky.social & @therecordmedia.bsky.social

www.aivd.nl/documenten/p...
Microsoft calls it Void Blizzard. Their report is here: www.microsoft.com/en-us/securi...

www.aivd.nl/documenten/p...
Microsoft calls it Void Blizzard. Their report is here: www.microsoft.com/en-us/securi...

www.metacurity.com/russias-apt2...

www.metacurity.com/russias-apt2...
www.europol.europa.eu/media-press/...
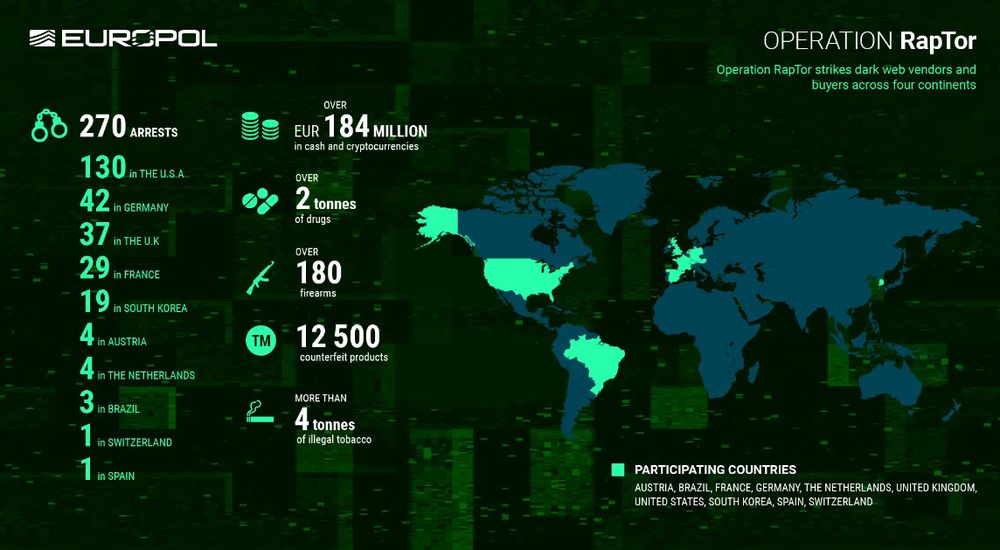
www.europol.europa.eu/media-press/...
This is a known Chinese APT group that seems to be specialized in Ivanti and other Western enterprise products... they have a long list of past zero-days in their name
blog.eclecticiq.com/china-nexus-...

This is a known Chinese APT group that seems to be specialized in Ivanti and other Western enterprise products... they have a long list of past zero-days in their name
blog.eclecticiq.com/china-nexus-...
Here is the full report:
blog.eclecticiq.com/china-nexus-...
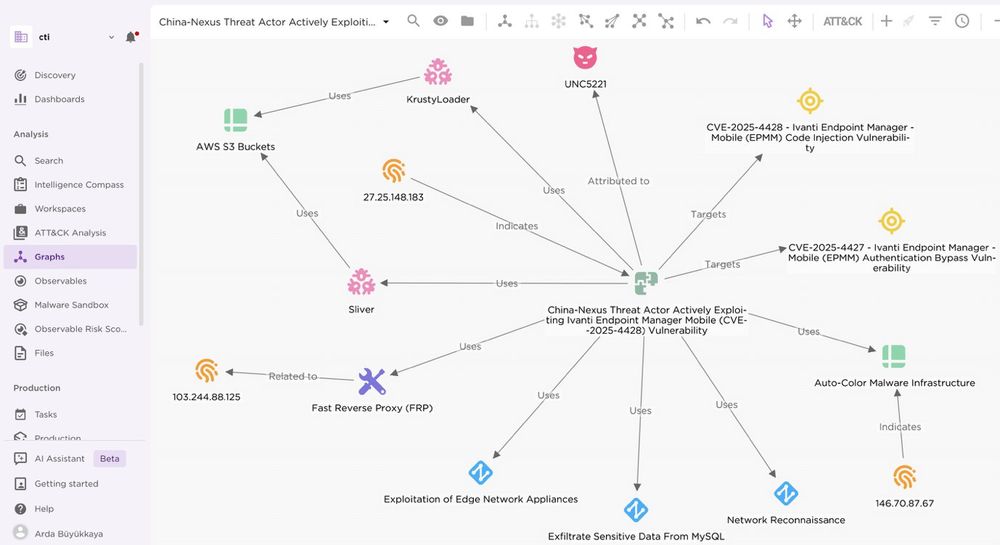
Here is the full report:
blog.eclecticiq.com/china-nexus-...
-APT28 targets email servers with XSS attacks
-Good report on DPRK cyber and IT worker schemes
-Russia uses USAID shutdown in info-op targeting Moldova
-RU disinfo group Storm-1516 is behind the Macron coke memes

-APT28 targets email servers with XSS attacks
-Good report on DPRK cyber and IT worker schemes
-Russia uses USAID shutdown in info-op targeting Moldova
-RU disinfo group Storm-1516 is behind the Macron coke memes
@hatr.bsky.social

@hatr.bsky.social
Details: www.virusbulletin.com/conference/v...
See you there! #vbconference #VB2025
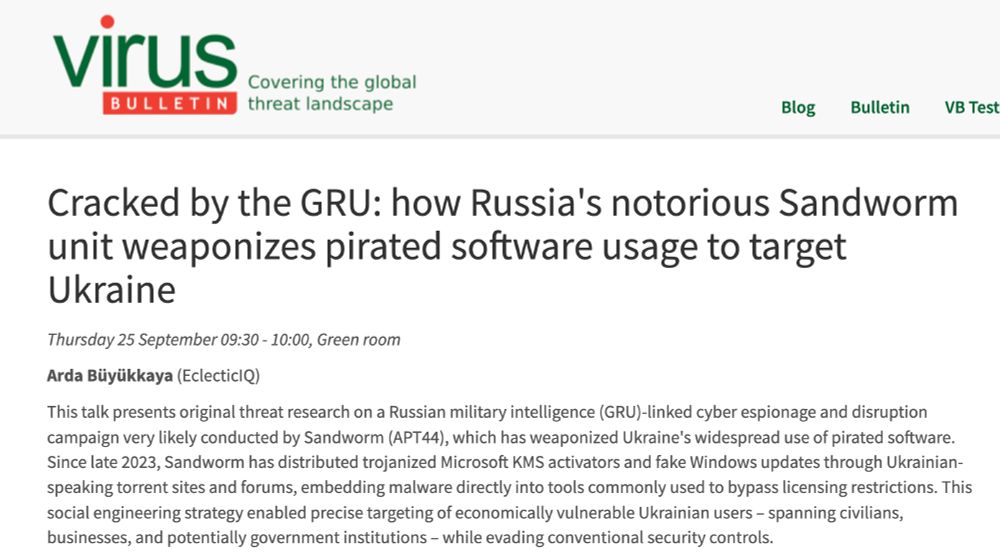
Details: www.virusbulletin.com/conference/v...
See you there! #vbconference #VB2025
www.nextgov.com/cybersecurit...

www.nextgov.com/cybersecurit...
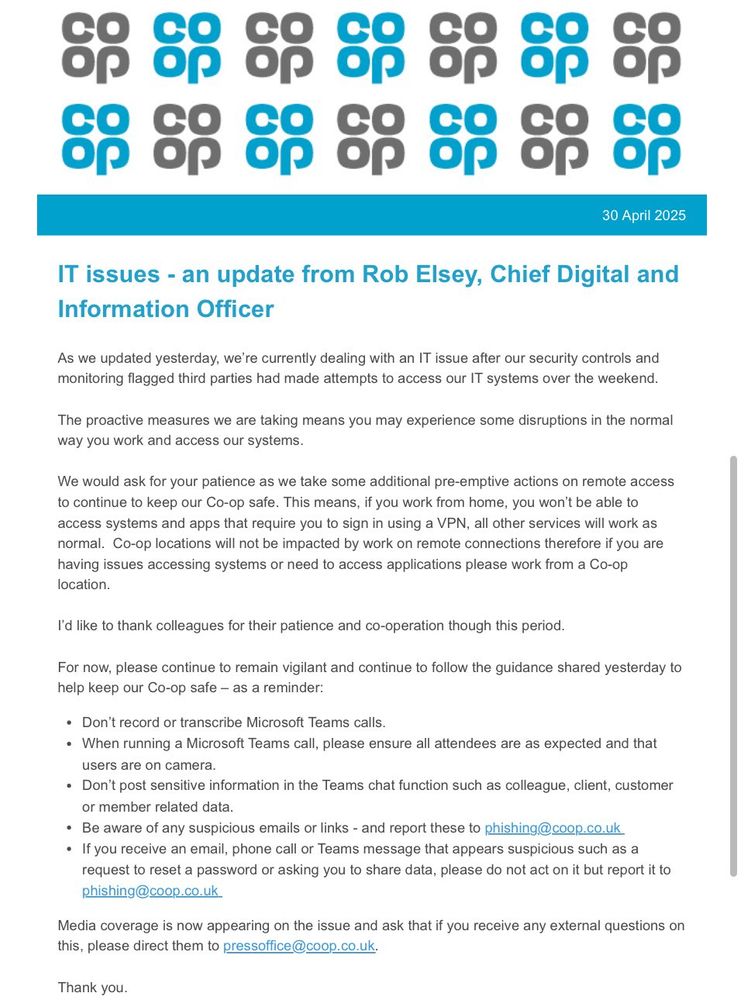
Newsletter: news.risky.biz/risky-bullet...
-French government grows a spine and calls out Russia's hacks
-Marks & Spencer sends staff home after ransomware attack
-China accuses US of hacking cryptography provider
-AirBorne vulnerabilities impact Apple's AirPlay
Newsletter: news.risky.biz/risky-bullet...
-French government grows a spine and calls out Russia's hacks
-Marks & Spencer sends staff home after ransomware attack
-China accuses US of hacking cryptography provider
-AirBorne vulnerabilities impact Apple's AirPlay
www.metacurity.com/france-accus...

www.metacurity.com/france-accus...


