
The stolen funds were transferred to five instant exchanges and deposited to Tornado Cash.

The stolen funds were transferred to five instant exchanges and deposited to Tornado Cash.
#crypto #bloomberg #scatteredspider #cryptodotcom

#crypto #bloomberg #scatteredspider #cryptodotcom
#crypto #cryptonews #rcmp #tradeogre

#crypto #cryptonews #rcmp #tradeogre
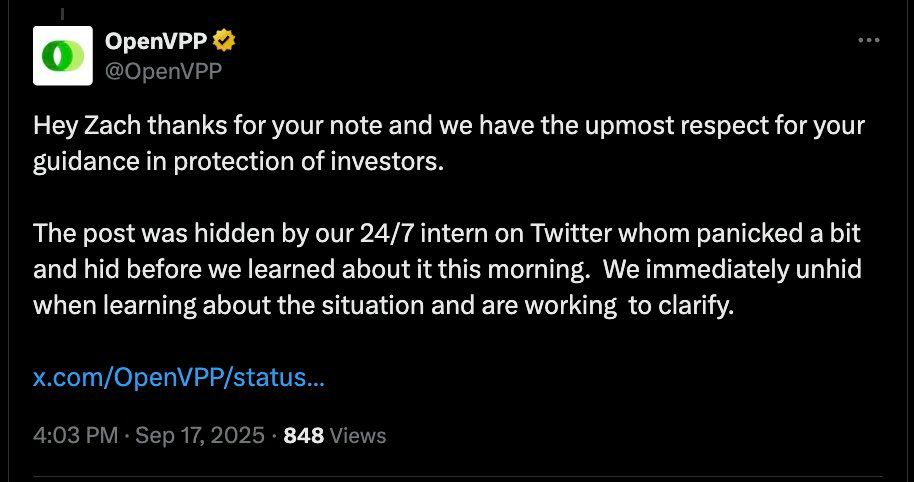
I reviewed the accounts promoting OpenVPP and it’s the usual influencer suspects.

I reviewed the accounts promoting OpenVPP and it’s the usual influencer suspects.
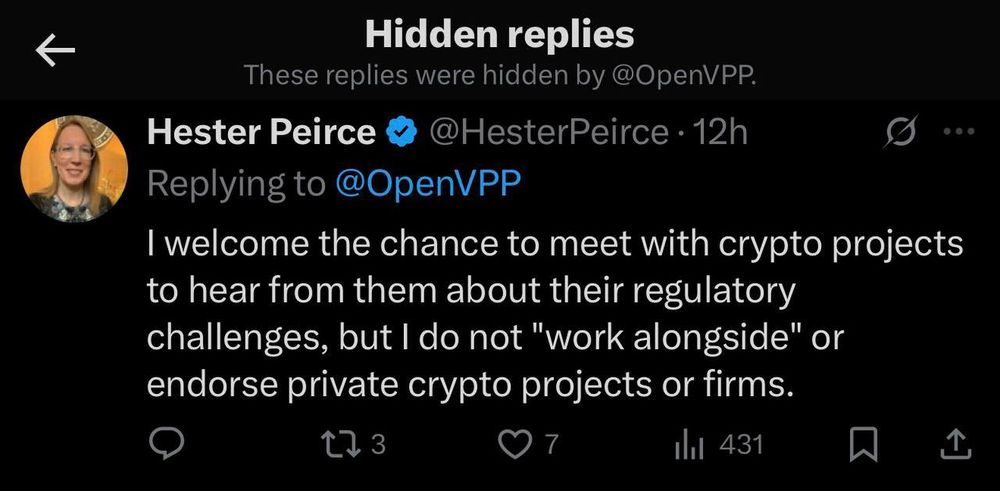
12 hrs ago Hester Pierce replied saying she does not work alongside or endorse private crypto projects.

12 hrs ago Hester Pierce replied saying she does not work alongside or endorse private crypto projects.
Ironically JP and his products have benefited significantly financially from the laundering of DPRK exploits/hacks such as Bybit in the past.

Ironically JP and his products have benefited significantly financially from the laundering of DPRK exploits/hacks such as Bybit in the past.
The attacker swapped USDC for ETH and immediately deposited the funds to Tornado.
Theft address
0xf0a6c5b65a81f0e8ddb2d14e2edcf7d10c928020
#crypto #usdc #ethereum #scamawareness

The attacker swapped USDC for ETH and immediately deposited the funds to Tornado.
Theft address
0xf0a6c5b65a81f0e8ddb2d14e2edcf7d10c928020
#crypto #usdc #ethereum #scamawareness

From 160+ accounts who accepted the deal I only saw <5 accounts actually disclose the promotional posts as an advertisement.
#crypto



From 160+ accounts who accepted the deal I only saw <5 accounts actually disclose the promotional posts as an advertisement.
#crypto
Theft txn hash
da598f2a941ee3c249a3c11e5e171e186a08900012f6aad26e6d11b8e8816457
Theft address
bc1qyxyk4qgyrkx4rjwsuevug04wahdk6uf95mqlej
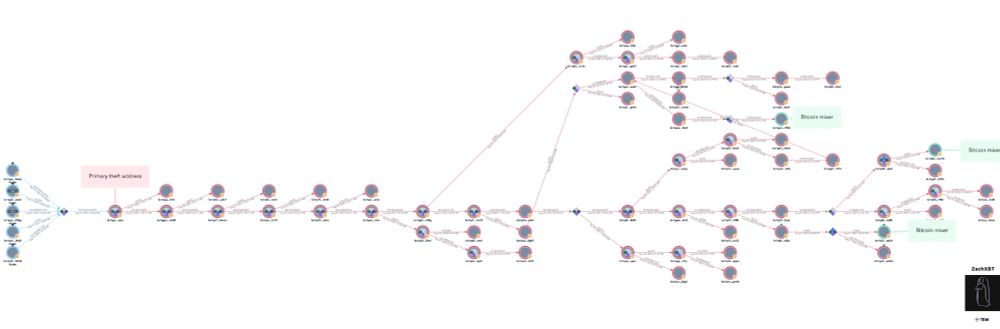
Theft txn hash
da598f2a941ee3c249a3c11e5e171e186a08900012f6aad26e6d11b8e8816457
Theft address
bc1qyxyk4qgyrkx4rjwsuevug04wahdk6uf95mqlej
There’s also the negligence by the teams hiring them who become combative when alerted.

There’s also the negligence by the teams hiring them who become combative when alerted.
Well besides all of the fraudulent documents detailed above their search history showed frequent Google Translate usage with translations to Korean with a Russian IP.


Well besides all of the fraudulent documents detailed above their search history showed frequent Google Translate usage with translations to Korean with a Russian IP.




Additional DPRK ITWs were identified at projects from the 0x78e1 address.

Additional DPRK ITWs were identified at projects from the 0x78e1 address.
0x78e1a4781d184e7ce6a124dd96e765e2bea96f2c


0x78e1a4781d184e7ce6a124dd96e765e2bea96f2c
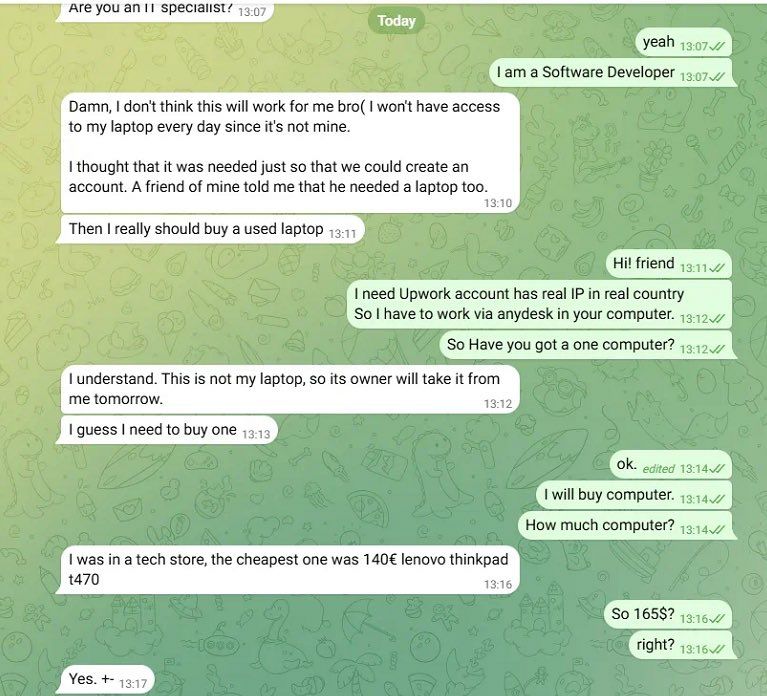



“I can't understand job requirement, and don't know what I need to do”
“Solution / fix: Put enough efforts in heart”


“I can't understand job requirement, and don't know what I need to do”
“Solution / fix: Put enough efforts in heart”
Google products were extensively used by them to organize their team’s schedules, tasks, and budgets with communications primarily in English.

Google products were extensively used by them to organize their team’s schedules, tasks, and budgets with communications primarily in English.


TLDR: Term consists of 12 MONTHS and 1 DAY as to each count, to be served concurrently; 3 YR SR TERM W/ CONDITIONS - term consists of 3 YEARS as to each count, to run concurrently; $400 SA; $248,257.07 Restitution; $60,000 Fine




TLDR: Term consists of 12 MONTHS and 1 DAY as to each count, to be served concurrently; 3 YR SR TERM W/ CONDITIONS - term consists of 3 YEARS as to each count, to run concurrently; $400 SA; $248,257.07 Restitution; $60,000 Fine


