Checkpoint published research on VoidLink C2 framework.
They call it "advanced malware framework"; but maybe I'm not sure what "advanced" means in this context.
Rule at end
1/2

Checkpoint published research on VoidLink C2 framework.
They call it "advanced malware framework"; but maybe I'm not sure what "advanced" means in this context.
Rule at end
1/2
Came across a low detection malware which seems YARA resistant. Currently in use by ransomware actor.
I'll post some thoughts, but would love suggestions from others.
I'll explain the malware and show the best I could come up with.
Rule at bottom
1/7

Came across a low detection malware which seems YARA resistant. Currently in use by ransomware actor.
I'll post some thoughts, but would love suggestions from others.
I'll explain the malware and show the best I could come up with.
Rule at bottom
1/7
Came across a low detection malware which seems YARA resistant. Currently in use by ransomware actor.
I'll post some thoughts, but would love suggestions from others.
I'll explain the malware and show the best I could come up with.
Rule at bottom
1/7

Came across a low detection malware which seems YARA resistant. Currently in use by ransomware actor.
I'll post some thoughts, but would love suggestions from others.
I'll explain the malware and show the best I could come up with.
Rule at bottom
1/7
Came across a low detection malware which seems YARA resistant. Currently in use by ransomware actor.
I'll post some thoughts, but would love suggestions from others.
I'll explain the malware and show the best I could come up with.
Rule at bottom
1/7

Came across a low detection malware which seems YARA resistant. Currently in use by ransomware actor.
I'll post some thoughts, but would love suggestions from others.
I'll explain the malware and show the best I could come up with.
Rule at bottom
1/7
VirusTotal uses CAPE sandbox to identify many malware families and determine if they can extract the malware's configuration. Since they use CAPE, we can often see their logic. Today, we'll suggest edits to a rule for AgentTesla.
Rule at end.
1/10

VirusTotal uses CAPE sandbox to identify many malware families and determine if they can extract the malware's configuration. Since they use CAPE, we can often see their logic. Today, we'll suggest edits to a rule for AgentTesla.
Rule at end.
1/10
In looking at automatic YARA generation, yarGen-Go is a must. Just released by @cyb3rops, it is a rewrite and advancement from the original yarGen.
We'll look at the same malware from day 10; a targeted HavocC2 loader with decoy.
rule at bottom
1/5

In looking at automatic YARA generation, yarGen-Go is a must. Just released by @cyb3rops, it is a rewrite and advancement from the original yarGen.
We'll look at the same malware from day 10; a targeted HavocC2 loader with decoy.
rule at bottom
1/5
There are a few lines of thinking around automatic YARA generation. I'm exploring these as part of this challenge. Today's we'll look at MCRIT.
MCRIT asks what do we learn by comparing samples? Can we find functions unique to the family?
rule at end
1/5

There are a few lines of thinking around automatic YARA generation. I'm exploring these as part of this challenge. Today's we'll look at MCRIT.
MCRIT asks what do we learn by comparing samples? Can we find functions unique to the family?
rule at end
1/5
YARA looks for the header used in a .SCPT file used by BlueNoroff (DPRK) to target MacOS systems.
Script is delivered to victims disguised as a Zoom meeting launcher.
e.g. a7c7d75c33aa809c231f1b22521ae680248986c980b45aa0881e19c19b7b1892
Rule at end
1/3

YARA looks for the header used in a .SCPT file used by BlueNoroff (DPRK) to target MacOS systems.
Script is delivered to victims disguised as a Zoom meeting launcher.
e.g. a7c7d75c33aa809c231f1b22521ae680248986c980b45aa0881e19c19b7b1892
Rule at end
1/3
For many years, many attackers tried to keep their binaries small. However, the others found the opposite works too: extremely large binaries can cause problems with analysis.
What can be done about these large executables?
Rule at end
1/6

For many years, many attackers tried to keep their binaries small. However, the others found the opposite works too: extremely large binaries can cause problems with analysis.
What can be done about these large executables?
Rule at end
1/6
@malwrhunterteam identified a suspicious file signed by "Xiamen Jialan Guang Information Technology Service Co., Ltd."
While we have a pretty good idea it'll be abused, it hasn't been yet.
So, lets watch for it to be abused.
Rule at end
1/5
@malwrhunterteam identified a suspicious file signed by "Xiamen Jialan Guang Information Technology Service Co., Ltd."
While we have a pretty good idea it'll be abused, it hasn't been yet.
So, lets watch for it to be abused.
Rule at end
1/5
In December and again in January, an unknown actor replaced the download on EmEditor's website with a malicious installer. Each time, the download was a trojan installer with a valid code-signing signature.
How can we detect this?
Rule at end
1/6

In December and again in January, an unknown actor replaced the download on EmEditor's website with a malicious installer. Each time, the download was a trojan installer with a valid code-signing signature.
How can we detect this?
Rule at end
1/6
The Cert Graveyard project reports and documents abuse code-signing including Apple issued certificates.
When reporting a certificate, we want to ensure Apple has all the identifiers they need to investigate and act.
Rule at end
1/7

The Cert Graveyard project reports and documents abuse code-signing including Apple issued certificates.
When reporting a certificate, we want to ensure Apple has all the identifiers they need to investigate and act.
Rule at end
1/7
One heavy user of code-signing certificates is Rhysida Ransomware.
In June, I created a YARA rule focusing on their malware to help me find and report their certificates. To do so, I had to create a YARA rule on the Rich PE Header.
Rule at end
1/7


One heavy user of code-signing certificates is Rhysida Ransomware.
In June, I created a YARA rule focusing on their malware to help me find and report their certificates. To do so, I had to create a YARA rule on the Rich PE Header.
Rule at end
1/7
This relates to obfusheader discussed by @RussianPanda95 and @c0ner0ne.
If the dev is going to use hard-coded strings, lets use them to our advantage.
This thread will demo Malcat's YARA features.
Rule at end of thread
1/5

This relates to obfusheader discussed by @RussianPanda95 and @c0ner0ne.
If the dev is going to use hard-coded strings, lets use them to our advantage.
This thread will demo Malcat's YARA features.
Rule at end of thread
1/5
YARA rule to detect the default Delphi darkmode dib icon.
I've seen this icon excessively over the years. Using @unpacme 's YARA hunting tools, I saw 0 known goodware and 800 packed junk.
Rule at end
1/4

YARA rule to detect the default Delphi darkmode dib icon.
I've seen this icon excessively over the years. Using @unpacme 's YARA hunting tools, I saw 0 known goodware and 800 packed junk.
Rule at end
1/4
YARA rule to detect the default Delphi darkmode dib icon.
I've seen this icon excessively over the years. Using @unpacme 's YARA hunting tools, I saw 0 known goodware and 800 packed junk.
Rule at end
1/4

YARA rule to detect the default Delphi darkmode dib icon.
I've seen this icon excessively over the years. Using @unpacme 's YARA hunting tools, I saw 0 known goodware and 800 packed junk.
Rule at end
1/4
This YARA rule detects a technique used in #TrashAgent malware. The malware has a hard-coded list of apps to check for on the system. This YARA looks for the way they parse the list.
In the image, the list is demarcated with "nepo"
rule at end
1/7

This YARA rule detects a technique used in #TrashAgent malware. The malware has a hard-coded list of apps to check for on the system. This YARA looks for the way they parse the list.
In the image, the list is demarcated with "nepo"
rule at end
1/7
2 time reigning champ Yashraj
has kindly offered to take the helm for this community effort! Give the homie a follow 👊
Check the repo to contribute: github.com/100DaysofYARA
And gear up for Jan 1 when #100DaysofYARA will kick off!

2 time reigning champ Yashraj
has kindly offered to take the helm for this community effort! Give the homie a follow 👊
Check the repo to contribute: github.com/100DaysofYARA
And gear up for Jan 1 when #100DaysofYARA will kick off!
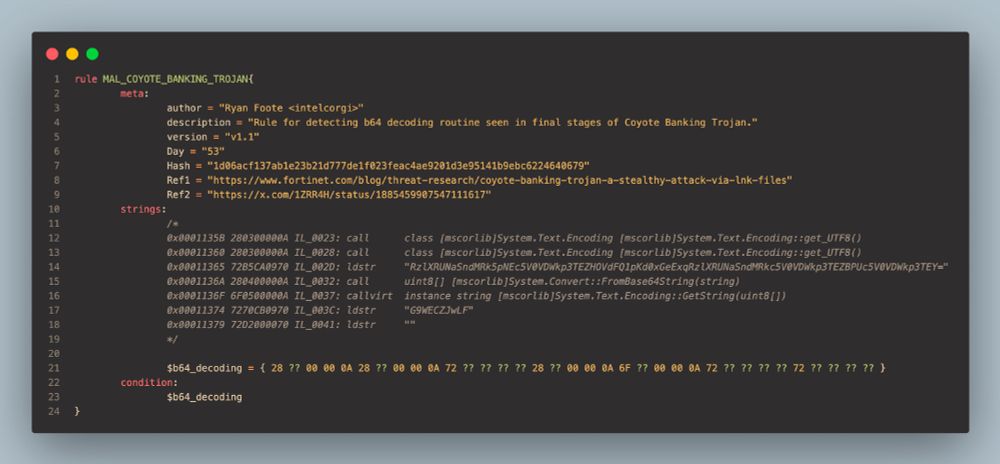
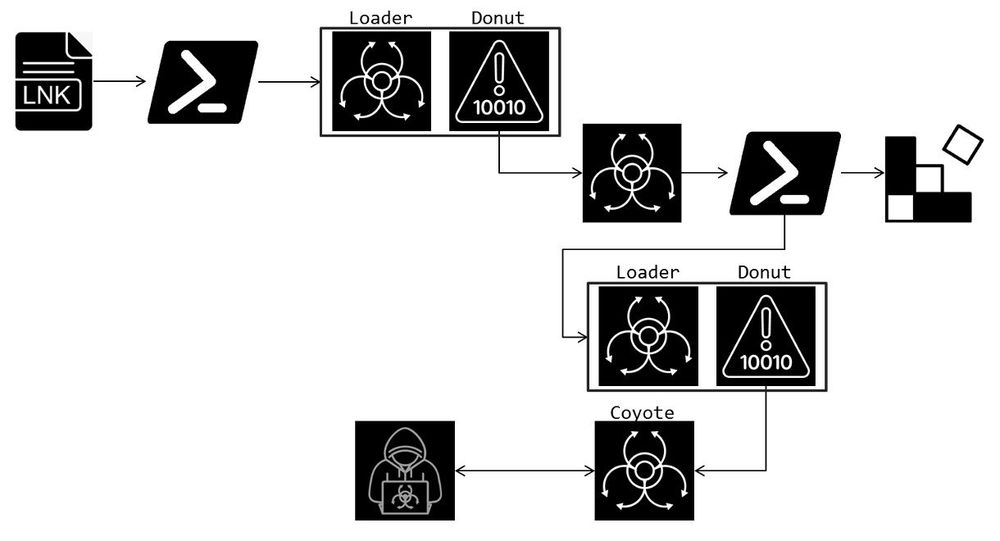
E.g. IL code patterns, method signature definitions, GUIDs, compressed length
#GDATATechblog #100DaysOfYara
www.gdatasoftware.com/blog/2025/04...

E.g. IL code patterns, method signature definitions, GUIDs, compressed length
#GDATATechblog #100DaysOfYara
www.gdatasoftware.com/blog/2025/04...
buff.ly/4ibEkwZ
Always more to learn! Is it too late for #100DaysOfYara?! 😉

buff.ly/4ibEkwZ
Always more to learn! Is it too late for #100DaysOfYara?! 😉
Im using it for targeted live strings extraction in Velociraptor and some cool workflow to drive things like building yara rules.
The screenshot shows VQL to dynamically generate a yara rule to preferred string size.


Im using it for targeted live strings extraction in Velociraptor and some cool workflow to drive things like building yara rules.
The screenshot shows VQL to dynamically generate a yara rule to preferred string size.
Also going to be doing much more Macho because I have been working on Offsec's MacOS Exploit Dev course
github.com/augustvansic...

Also going to be doing much more Macho because I have been working on Offsec's MacOS Exploit Dev course
github.com/augustvansic...
Todays sample is a sh file, typically a script on unix based systems. It calls different files from a C2 hosting, gives them 'chmod 777' permissions (so it can execute), executes them on disk, and removes the file after execution in memory.
github.com/augustvansic...
Todays sample is a sh file, typically a script on unix based systems. It calls different files from a C2 hosting, gives them 'chmod 777' permissions (so it can execute), executes them on disk, and removes the file after execution in memory.
github.com/augustvansic...

