#Cybersecurity #BinaryAnalysis

#Cybersecurity #BinaryAnalysis


#Akai #MPD218 Preset File Format (.mpd218)
akai-mpd218_preset_file_format.md
gist.github.com/mxmilkiib/018f4a55a529640427a29f143a3978d3
generated by Claude Sonnet + GPT-5 (high reasoning)
#midi #controller #sysex #controllerism #fileformat #binaryanalysis #djing #creativecoding

#Akai #MPD218 Preset File Format (.mpd218)
akai-mpd218_preset_file_format.md
gist.github.com/mxmilkiib/018f4a55a529640427a29f143a3978d3
generated by Claude Sonnet + GPT-5 (high reasoning)
#midi #controller #sysex #controllerism #fileformat #binaryanalysis #djing #creativecoding
Read: bit.ly/4glKiLs
#MachineLearning #BinaryAnalysis #OpenScience #ACRT

Read: bit.ly/4glKiLs
#MachineLearning #BinaryAnalysis #OpenScience #ACRT
In our Security Short, Edwin makes it clear: to protect IoT products, you have to go deeper than the surface.
#IoT
In our Security Short, Edwin makes it clear: to protect IoT products, you have to go deeper than the surface.
#IoT
In our "Security Short", Edwin stresses that the only way to truly understand what’s inside precompiled binaries is through #BinaryAnalysis.
Visibility matters.
In our "Security Short", Edwin stresses that the only way to truly understand what’s inside precompiled binaries is through #BinaryAnalysis.
Visibility matters.
👎 No binary scanning
🕳️ Incomplete #SBOMs
📉 Missed vulnerabilities
Here are 6 signs it's time to upgrade & what to look for 👉 finitestate.io/blog/when-to...
#ProductSecurity #IoTSecurity #SBOM #BinaryAnalysis #DevSecOps #SCA #SAST

👎 No binary scanning
🕳️ Incomplete #SBOMs
📉 Missed vulnerabilities
Here are 6 signs it's time to upgrade & what to look for 👉 finitestate.io/blog/when-to...
#ProductSecurity #IoTSecurity #SBOM #BinaryAnalysis #DevSecOps #SCA #SAST
In our latest blog, we explore the blind spots in traditional SCA/SAST & how Finite State helps teams uncover what others miss 👉https://t.co/R9giOUBz2E
#IoTSecurity #ProductSecurity #BinaryAnalysis #SCA #SAST

In our latest blog, we explore the blind spots in traditional SCA/SAST & how Finite State helps teams uncover what others miss 👉https://t.co/R9giOUBz2E
#IoTSecurity #ProductSecurity #BinaryAnalysis #SCA #SAST
🔗Check it out:
github.com/M3rcuryLake/...
#binaryanalysis #linuxelf #reverseengineering #malwareanalysis #threathunting #infosec
🔗Check it out:
github.com/M3rcuryLake/...
#binaryanalysis #linuxelf #reverseengineering #malwareanalysis #threathunting #infosec


www.businesswire.com/news/home/20...
#BinaryAnalysis #SBOM #SoftwareSupplyChain #DevSecOps #AppSec #OpenSource #Security #BCA #Compliance #ThirdPartyRisk

www.businesswire.com/news/home/20...
#BinaryAnalysis #SBOM #SoftwareSupplyChain #DevSecOps #AppSec #OpenSource #Security #BCA #Compliance #ThirdPartyRisk
#LLM4Code #LLM #BinaryAnalysis #Security
@cerias.bsky.social @iclr-conf.bsky.social
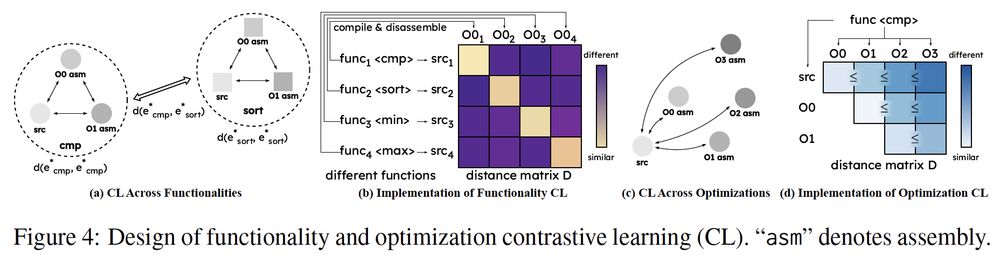
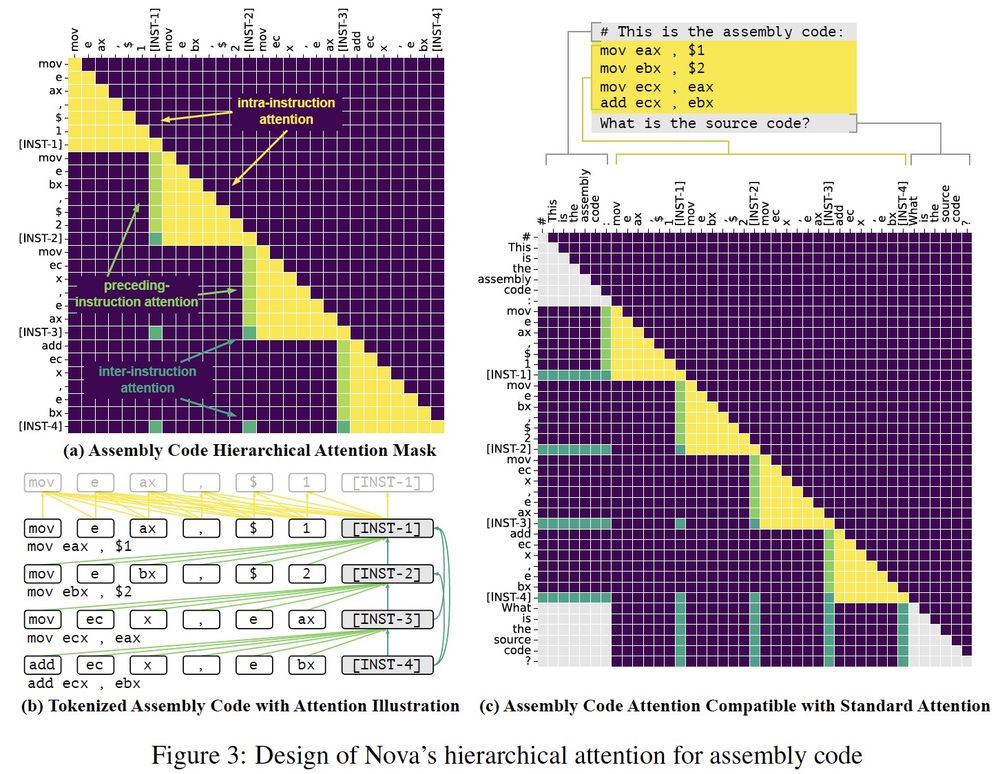

#LLM4Code #LLM #BinaryAnalysis #Security
@cerias.bsky.social @iclr-conf.bsky.social



