Sabine Oechsner 🟥
@proofnerd.bsky.social
200 followers
180 following
48 posts
cryptography and pretty proofs | PL-curious | assistant professor @ VU Amsterdam
soechsner.de
Posts
Media
Videos
Starter Packs
Reposted by Sabine Oechsner 🟥
Reposted by Sabine Oechsner 🟥
Reposted by Sabine Oechsner 🟥
Reposted by Sabine Oechsner 🟥
Reposted by Sabine Oechsner 🟥
Sabine Oechsner 🟥
@proofnerd.bsky.social
· Sep 12
Reposted by Sabine Oechsner 🟥
Reposted by Sabine Oechsner 🟥
Reposted by Sabine Oechsner 🟥
Reposted by Sabine Oechsner 🟥
Sabine Oechsner 🟥
@proofnerd.bsky.social
· Aug 15
Reposted by Sabine Oechsner 🟥
Alex
@alexanderlhicks.com
· Aug 8
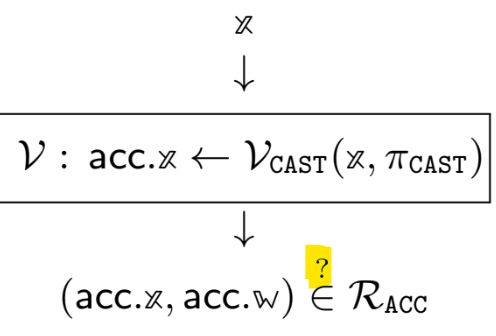
Ethereum Foundation - Researcher/Engineer (Formal Verification)
Role summary As a member of the Protocol Snarkification team, you will work towards snarkifying Ethereum by working to specify and verify the core cryptographic components of proof systems and their i...
jobs.lever.co
Reposted by Sabine Oechsner 🟥
Reposted by Sabine Oechsner 🟥