
From Estonia.
ZK proofs, SNARKs, security assumptions.
Homepage: https://sites.google.com/view/jannosiim


csa-scientist-open-letter.org/Sep2025
csa-scientist-open-letter.org/Sep2025
![Abstract. A zero-knowledge proof demonstrates that a fact (like that a Sudoku puzzle has a solution) is true while, counterintuitively, revealing nothing else (like what the solution actually is). This remarkable guarantee is extremely useful in cryptographic applications, but it comes at a cost. A classical impossibility result by Goldreich and Oren [J. Cryptol. ’94] shows that zero-knowledge proofs must necessarily sacrifice basic properties of traditional mathematical proofs — namely perfect soundness (that no proof of a false statement exists) and non-interactivity (that a proof can be transmitted in a single message).
Contrary to this impossibility, we show that zero-knowledge with perfect soundness and no interaction is effectively possible. We do so by defining and constructing a powerful new relaxation of zero-knowledge. Intuitively, while the classical zero-knowledge definition requires that an object called a simulator actually exists, our new definition only requires that one cannot rule out that a simulator exists (in a particular logical sense). Using this, we show that every falsifiable security property of (classical) zero-knowledge can be achieved with no interaction, no setup, and perfect soundness. This enables us to remove interaction and setup from (classical) zero-knowledge in essentially all of its applications in the literature, at the relatively mild cost that such applications now have security that is “game-based” instead of “simulation-based.”
Our construction builds on the work of Kuykendall and Zhandry [TCC ’20] and relies on two central, longstanding, and well-studied assumptions that we show are also necessary. The first is the existence of non-interactive witness indistinguishable proofs, which follows from standard assumptions in cryptography. The second is Krajícek and Pudlák’s 1989 conjecture that no optimal proof system exists. This is one of the main conjectures in the field of proof complexity and is the natural finitistic analogue of the impossibility of Hilbert’s second problem (and, hence, also Gödel’s incompleteness theorem). Our high-level idea is to use these assumptions to construct a prover and verifier where no simulator exists, but the non-existence of a simulator is independent (in the logical sense of unprovability) of an arbitrarily strong logical system. One such logical system is the standard axioms of mathematics: ZFC.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:fwa55bujvdrwlwlwgqmmxmuf/bafkreiflntzdprcpqm2vxfmwhx6gke7sa2bzx2oc2ju7zrjnqeqymx3nh4@jpeg)


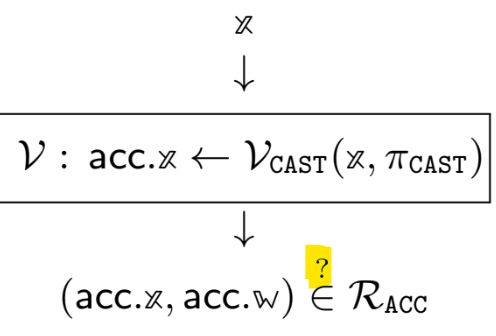
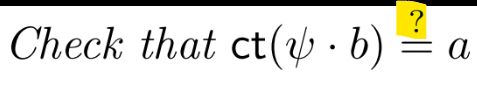

In particular, we show that in BLS12-381 n-PDL (Power DL) is equivalent to n-Diffie-Hellman exponent assumption.
![Abstract. A reduction showing that the hardness of the discrete logarithm (DL) assumption implies the hardness of the computational Diffie-Hellman (CDH) assumption in groups of order p, where p − 1 is smooth, was first presented by den Boer [Crypto, 88].} We also consider groups of prime order p, where p − 1 is somewhat smooth (say, every prime q that divides p − 1 is less than 2¹⁰⁰). Several practically relevant groups satisfy this condition. 1. We present a concretely efficient version of the reduction for such groups. In particular, among practically relevant groups, we obtain the most efficient and tightest reduction in the literature for BLS12-381, showing that DL = CDH. 2. By generalizing the reduction, we show that in these groups the n-Power DL (n-PDL) assumption implies n-Diffie-Hellman Exponent (n-DHE) assumption, where n is polynomial in the security parameter. On the negative side, we show there is no generic reduction, which could demonstrate that n-PDL implies the n-Generalized Diffie-Hellman Exponent (n-GDHE) assumption. This is in stark contrast with the algebraic group model, where this implication holds.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:fwa55bujvdrwlwlwgqmmxmuf/bafkreiezbnvidm7exhiiqdi74nhd7zfkdu25rzyl2kkwgwvotqvn2jaduu@jpeg)

In particular, we show that in BLS12-381 n-PDL (Power DL) is equivalent to n-Diffie-Hellman exponent assumption.

"On Knowledge-Soundness of Plonk in ROM from Falsifiable Assumptions" (Helger Lipmaa, Roberto Parisella, Janno Siim), with ex-students Roberto and @jannosiim.bsky.social (Janno is also now a colleague)
"On Knowledge-Soundness of Plonk in ROM from Falsifiable Assumptions" (Helger Lipmaa, Roberto Parisella, Janno Siim), with ex-students Roberto and @jannosiim.bsky.social (Janno is also now a colleague)


We intend to build a strong ZK research group here + I think it's a really cool place to live and work: virtualtour.ut.ee/en/84-univer...
We intend to build a strong ZK research group here + I think it's a really cool place to live and work: virtualtour.ut.ee/en/84-univer...
@jannosiim.bsky.social
and some PhD students) have additional openings for a postdoc and a PhD student; see crypto.cs.ut.ee/Main/OpenPos... (iacr.org/jobs link will hopefully be up in a few days). Apply by email to me
@jannosiim.bsky.social
and some PhD students) have additional openings for a postdoc and a PhD student; see crypto.cs.ut.ee/Main/OpenPos... (iacr.org/jobs link will hopefully be up in a few days). Apply by email to me
We are looking forward to exciting talks about cryptographic proofs and proof techniques. Thanks to everyone who submitted a proposal!
protecs-workshop.gitlab.io/accepted


We are looking forward to exciting talks about cryptographic proofs and proof techniques. Thanks to everyone who submitted a proposal!
protecs-workshop.gitlab.io/accepted

Submission deadline is March 21, 2025 (AoE).
Please help spread the word! 🙏
privcryptworkshop.github.io
I forgot after one minute that I'm not talking to a human. I guess the movie "Her" is the reality now
I forgot after one minute that I'm not talking to a human. I guess the movie "Her" is the reality now
July 21-23, 2025 – Rabat, Morocco 🇲🇦
Extended submission deadline in 1 week:
africacrypt2025.sciencesconf.org
Submit your best results !
See you in Rabat 🇲🇦 in July 2025.

July 21-23, 2025 – Rabat, Morocco 🇲🇦
Extended submission deadline in 1 week:
africacrypt2025.sciencesconf.org
Submit your best results !
See you in Rabat 🇲🇦 in July 2025.






