Corgi dad 🐶
Cat servant 🐱
Tattoo collector 🖼️
Runner 🏃🏻
When attackers use conversation context to bypass LLM safeguards, single-prompt evals just don't cut it anymore.
Dive into @atomicchonk.bsky.social's latest blog on multi-prompt attack detection. ghst.ly/47qJhzn

When attackers use conversation context to bypass LLM safeguards, single-prompt evals just don't cut it anymore.
Dive into @atomicchonk.bsky.social's latest blog on multi-prompt attack detection. ghst.ly/47qJhzn
Join @atomicchonk.bsky.social next week to understand Windows access tokens & their use in the Windows environment. ghst.ly/june-web-bsky

Join @atomicchonk.bsky.social next week to understand Windows access tokens & their use in the Windows environment. ghst.ly/june-web-bsky

Join our upcoming webinar w/ @atomicchonk.bsky.social as he breaks down the starchy workings of potato exploits — from Windows access tokens to technical walkthroughs of Rotten, Juicy, and Rogue potatoes.
Register at ghst.ly/june-web-bsky

Join our upcoming webinar w/ @atomicchonk.bsky.social as he breaks down the starchy workings of potato exploits — from Windows access tokens to technical walkthroughs of Rotten, Juicy, and Rogue potatoes.
Register at ghst.ly/june-web-bsky
Also added some PowerShell on my GitHub to create and remove the mitigations.
Check out @jimsycurity.adminsdholder.com's latest blog post to understand how you can mitigate risk. ghst.ly/4kXTLd9
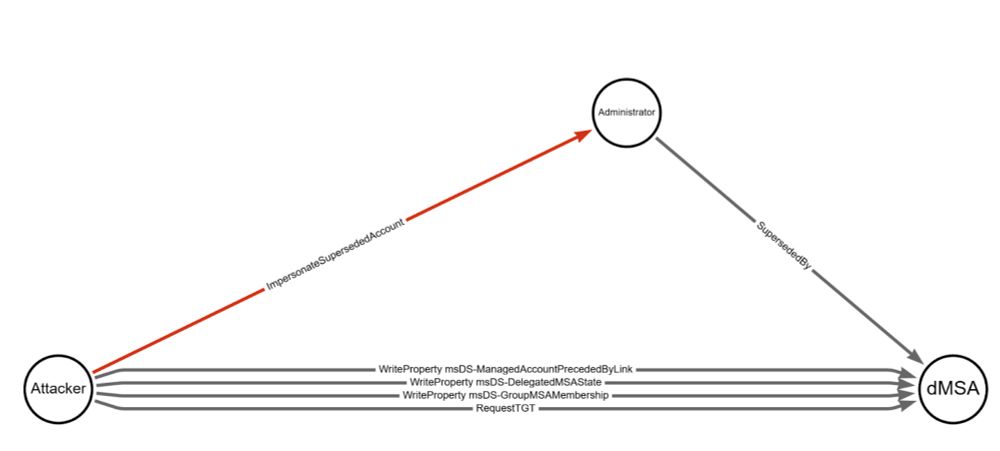
Also added some PowerShell on my GitHub to create and remove the mitigations.
Check out @jimsycurity.adminsdholder.com's latest blog post to understand how you can mitigate risk. ghst.ly/4kXTLd9

Check out @jimsycurity.adminsdholder.com's latest blog post to understand how you can mitigate risk. ghst.ly/4kXTLd9




Join @atomicchonk.bsky.social at @cackalackycon.bsky.social this weekend for a walkthrough of Windows access token manipulation and get the answer. ghst.ly/4jzjlnI

Join @atomicchonk.bsky.social at @cackalackycon.bsky.social this weekend for a walkthrough of Windows access token manipulation and get the answer. ghst.ly/4jzjlnI

Learn more ➡️ ghst.ly/4jzjlnI

Learn more ➡️ ghst.ly/4jzjlnI

Check out the schedule to learn more ➡️ ghst.ly/4jzjlnI

Check out the schedule to learn more ➡️ ghst.ly/4jzjlnI
1️⃣ Microsoft Authentication Library (MSAL)
2️⃣ Token Protection
3️⃣ Continuous Access Evaluation (CAE)
1️⃣ Microsoft Authentication Library (MSAL)
2️⃣ Token Protection
3️⃣ Continuous Access Evaluation (CAE)
www.ketman.org/dprk-it-work...

www.ketman.org/dprk-it-work...
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31

Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31