Get your free copy of our 2025 Threat Detection Report now. ⬇️
#ThreatReport #SecOps #ThreatIntel
redcanary.com/threat-detec...

Get your free copy of our 2025 Threat Detection Report now. ⬇️
#ThreatReport #SecOps #ThreatIntel
redcanary.com/threat-detec...
I saw this on a forum post today, and I swear it's the macOS/Linux version of "it's not the fall that kills, it's the impact"
I saw this on a forum post today, and I swear it's the macOS/Linux version of "it's not the fall that kills, it's the impact"
My goal is to continue to raise awareness on the abuse and the impact revocation has on malware distributors. Keep an eye on my socials for more news.
My goal is to continue to raise awareness on the abuse and the impact revocation has on malware distributors. Keep an eye on my socials for more news.
forensicitguy.github.io/exploring-ve...
#malware
forensicitguy.github.io/exploring-ve...
#malware
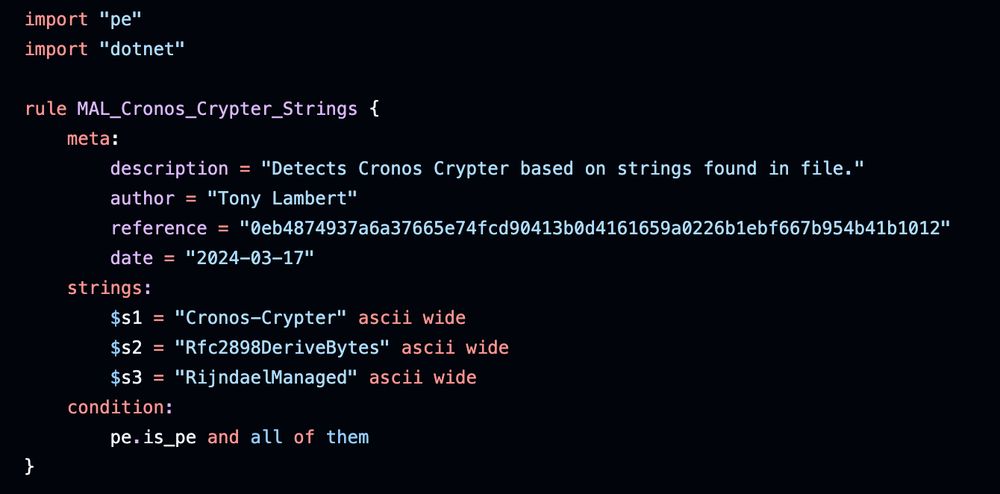
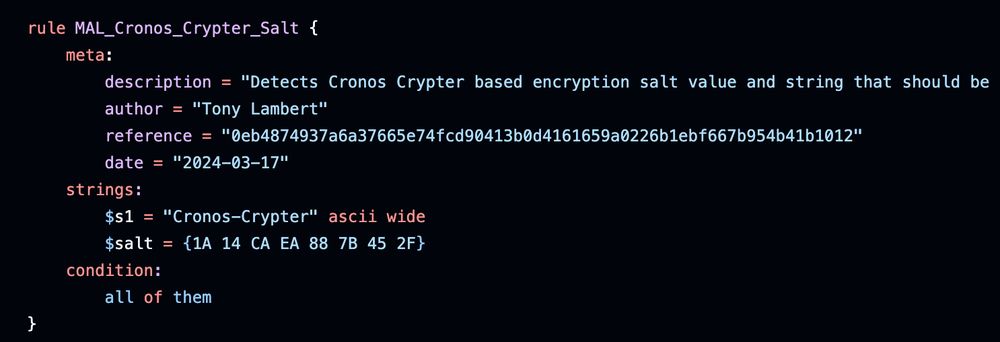

Pivoting on best-net[.]biz in URLscan show signs of six other compromised sites: urlscan.io/search/#best...
#NetSupportRAT




Pivoting on best-net[.]biz in URLscan show signs of six other compromised sites: urlscan.io/search/#best...
#NetSupportRAT
⚠️
https[:]//sites[.]google.com/view/pay-pal-helpcustomerservic/
#malvertising

⚠️
https[:]//sites[.]google.com/view/pay-pal-helpcustomerservic/
#malvertising
falconforce.nl/detection-en...
#detectionengineering #kql #blueteam

falconforce.nl/detection-en...
#detectionengineering #kql #blueteam



Bugfix - indicators could be printed in duplicate
certReport makes reporting code-signing certs easy. No-one likes spending time reading or writing reports. That is: I just noticed the problem. Maybe someone else did. I don't know. It is gone now.
Bugfix - indicators could be printed in duplicate
certReport makes reporting code-signing certs easy. No-one likes spending time reading or writing reports. That is: I just noticed the problem. Maybe someone else did. I don't know. It is gone now.


s4xevents.com/s4x25-traini...
s4xevents.com/s4x25-traini...
It is common for malware to be signed with code signing certificates.
How is this possible? Impostors receive the cert directly and sign malware.
In this blog-post, we look at 100 certs used by #Solarmarker #malware to learn more.
squiblydoo.blog/2024/05/13/i...

It is common for malware to be signed with code signing certificates.
How is this possible? Impostors receive the cert directly and sign malware.
In this blog-post, we look at 100 certs used by #Solarmarker #malware to learn more.
squiblydoo.blog/2024/05/13/i...
www.youtube.com/watch?v=O69e...

www.youtube.com/watch?v=O69e...