

The talented @OSINTgeek & I will be teaching our "Fundamentals of Cyber Investigations & Human Intelligence" class on the 9-10th of December in London!
Open AI has released a new report outlining the ways in which threat actors used their generative AI products to support their social engineering attack operations. They provide the case studies.
openai.com/global-affai...
Why is this useful? 🧵
Open AI has released a new report outlining the ways in which threat actors used their generative AI products to support their social engineering attack operations. They provide the case studies.
openai.com/global-affai...
Why is this useful? 🧵
I SO look forward to it and to meeting the participants!! 🤩👩🏻💻
Full class content & details: www.brucon.org/training-det...

I SO look forward to it and to meeting the participants!! 🤩👩🏻💻
Full class content & details: www.brucon.org/training-det...
It started with 2 days full of #socialengineering & #OSINT training where I had the privilege to teach a class that was present, curious, and ready to try things out.
Big bonus: reconnecting with friends during the conference days afterwards😊


It started with 2 days full of #socialengineering & #OSINT training where I had the privilege to teach a class that was present, curious, and ready to try things out.
Big bonus: reconnecting with friends during the conference days afterwards😊
I wrote an article explaining what Agentic AI really is & how it can shape the future of the social engineering threat landscape.
christina-lekati.medium.com/when-ai-goes...

I wrote an article explaining what Agentic AI really is & how it can shape the future of the social engineering threat landscape.
christina-lekati.medium.com/when-ai-goes...
I wrote an article explaining what Agentic AI really is & how it can shape the future of the social engineering threat landscape.
christina-lekati.medium.com/when-ai-goes...

I wrote an article explaining what Agentic AI really is & how it can shape the future of the social engineering threat landscape.
christina-lekati.medium.com/when-ai-goes...
New class modules:
🔸️State-Sponsored social engineering schemes
🔸️Using AI for OSINT tasks (responsibly)
🔸️How attackers are using AI to supercharge their SE.
Hands-on, practical & realistic. See you at x33fcon in only 4 weeks! 😱🥳
New class modules:
🔸️State-Sponsored social engineering schemes
🔸️Using AI for OSINT tasks (responsibly)
🔸️How attackers are using AI to supercharge their SE.
Hands-on, practical & realistic. See you at x33fcon in only 4 weeks! 😱🥳
Eliska & Julien do a great job in breaking down important concepts, risks, benefits & analytical aspects of using HUMINT tactics in a CTI workflow ⬇️
youtu.be/o1TTO5d1DXQ?...

Eliska & Julien do a great job in breaking down important concepts, risks, benefits & analytical aspects of using HUMINT tactics in a CTI workflow ⬇️
youtu.be/o1TTO5d1DXQ?...
"OSINT used to be a thinking game. Now it’s becoming a trusting game and that should terrify you."
#OSINT #OSINT4good #AI
Read the blog here: www.dutchosintguy.com/post/the-slo...

"OSINT used to be a thinking game. Now it’s becoming a trusting game and that should terrify you."
#OSINT #OSINT4good #AI
Read the blog here: www.dutchosintguy.com/post/the-slo...
This is an intensive, 2-day training 🧵

This is an intensive, 2-day training 🧵


The Dark Overlord investigation is an interesting report showcasing how HUMINT helps better understand threat actor activities, and even infiltrate their inner circles to uncover real identities.
Some notes 🧵
nightlion.com/wp-content/u...

The Dark Overlord investigation is an interesting report showcasing how HUMINT helps better understand threat actor activities, and even infiltrate their inner circles to uncover real identities.
Some notes 🧵
nightlion.com/wp-content/u...
www.theregister.com/2025/01/15/s...

www.theregister.com/2025/01/15/s...
Used in social engineering, intelligence collection, & negotiations, elicitation is the subtle art of extracting sensitive information during a seemingly regular conversation.
Read more in my new blog:
christina-lekati.medium.com/elicitation-...

Used in social engineering, intelligence collection, & negotiations, elicitation is the subtle art of extracting sensitive information during a seemingly regular conversation.
Read more in my new blog:
christina-lekati.medium.com/elicitation-...
🔹 On the 21st of January I will be giving a 4-hour online class on #Elicitation 𝗧𝗲𝗰𝗵𝗻𝗶𝗾𝘂𝗲𝘀.
🔹 On the 28th of January @osintgeek.de will be teaching #Telegram 𝗜𝗻𝘃𝗲𝘀𝘁𝗶𝗴𝗮𝘁𝗶𝗼𝗻𝘀.
⬇️🧵
🔹 On the 21st of January I will be giving a 4-hour online class on #Elicitation 𝗧𝗲𝗰𝗵𝗻𝗶𝗾𝘂𝗲𝘀.
🔹 On the 28th of January @osintgeek.de will be teaching #Telegram 𝗜𝗻𝘃𝗲𝘀𝘁𝗶𝗴𝗮𝘁𝗶𝗼𝗻𝘀.
⬇️🧵
Used in social engineering, intelligence collection, & negotiations, elicitation is the subtle art of extracting sensitive information during a seemingly regular conversation.
Read more in my new blog:
christina-lekati.medium.com/elicitation-...

Used in social engineering, intelligence collection, & negotiations, elicitation is the subtle art of extracting sensitive information during a seemingly regular conversation.
Read more in my new blog:
christina-lekati.medium.com/elicitation-...
🔹 On the 21st of January I will be giving a 4-hour online class on #Elicitation 𝗧𝗲𝗰𝗵𝗻𝗶𝗾𝘂𝗲𝘀.
🔹 On the 28th of January @osintgeek.de will be teaching #Telegram 𝗜𝗻𝘃𝗲𝘀𝘁𝗶𝗴𝗮𝘁𝗶𝗼𝗻𝘀.
⬇️🧵
🔹 On the 21st of January I will be giving a 4-hour online class on #Elicitation 𝗧𝗲𝗰𝗵𝗻𝗶𝗾𝘂𝗲𝘀.
🔹 On the 28th of January @osintgeek.de will be teaching #Telegram 𝗜𝗻𝘃𝗲𝘀𝘁𝗶𝗴𝗮𝘁𝗶𝗼𝗻𝘀.
⬇️🧵
Spent the week giving our 2-day training to a largely diverse class, strolling around London, celebrating a birthday (thanks to @osintgeek.de who is the best work buddy you can have), and attending the conference!
You can say it was a real FULL week.



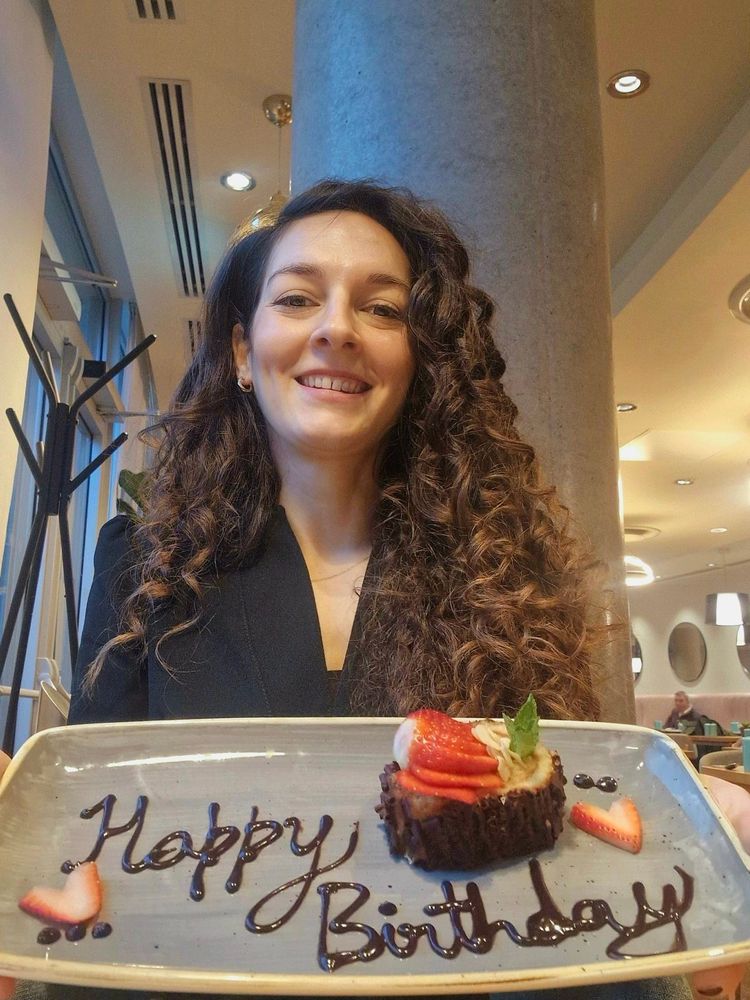
Spent the week giving our 2-day training to a largely diverse class, strolling around London, celebrating a birthday (thanks to @osintgeek.de who is the best work buddy you can have), and attending the conference!
You can say it was a real FULL week.
If you have been wanting to learn OSINT, HUMINT, Elicitation techniques or investigating Telegram, this is a very good chance.
More details below ⬇️
Enjoy!
Get 30% OFF ALL of our courses-including the new ones! 🤯
This Sale Ends on Cyber Monday: 2 December 2024 at 23:59 CET!
Code: WHISPERS
Let's see an overview of the classes included 🧵
#BlackFriday #OSINT #SOCMINT #HUMINT #OpenSourceIntelligence #Training
If you have been wanting to learn OSINT, HUMINT, Elicitation techniques or investigating Telegram, this is a very good chance.
More details below ⬇️
Enjoy!
Get 30% OFF ALL of our courses-including the new ones! 🤯
This Sale Ends on Cyber Monday: 2 December 2024 at 23:59 CET!
Code: WHISPERS
Let's see an overview of the classes included 🧵
#BlackFriday #OSINT #SOCMINT #HUMINT #OpenSourceIntelligence #Training
Get 30% OFF ALL of our courses-including the new ones! 🤯
This Sale Ends on Cyber Monday: 2 December 2024 at 23:59 CET!
Code: WHISPERS
Let's see an overview of the classes included 🧵
#BlackFriday #OSINT #SOCMINT #HUMINT #OpenSourceIntelligence #Training
Not just with China...

Not just with China...

Join this 4-hour training session to learn how to geolocate images and videos effectively
Get all the details and register here: www.eventbrite.fr/e/predicta-l...

Join this 4-hour training session to learn how to geolocate images and videos effectively
Get all the details and register here: www.eventbrite.fr/e/predicta-l...
It was the first time I delivered a deep-dive focusing entirely on the #psychology interplaying in social engineering & HUMINT operations at a cybersecurity conference.
It is very energizing to have a class full of curious minds!

It was the first time I delivered a deep-dive focusing entirely on the #psychology interplaying in social engineering & HUMINT operations at a cybersecurity conference.
It is very energizing to have a class full of curious minds!

