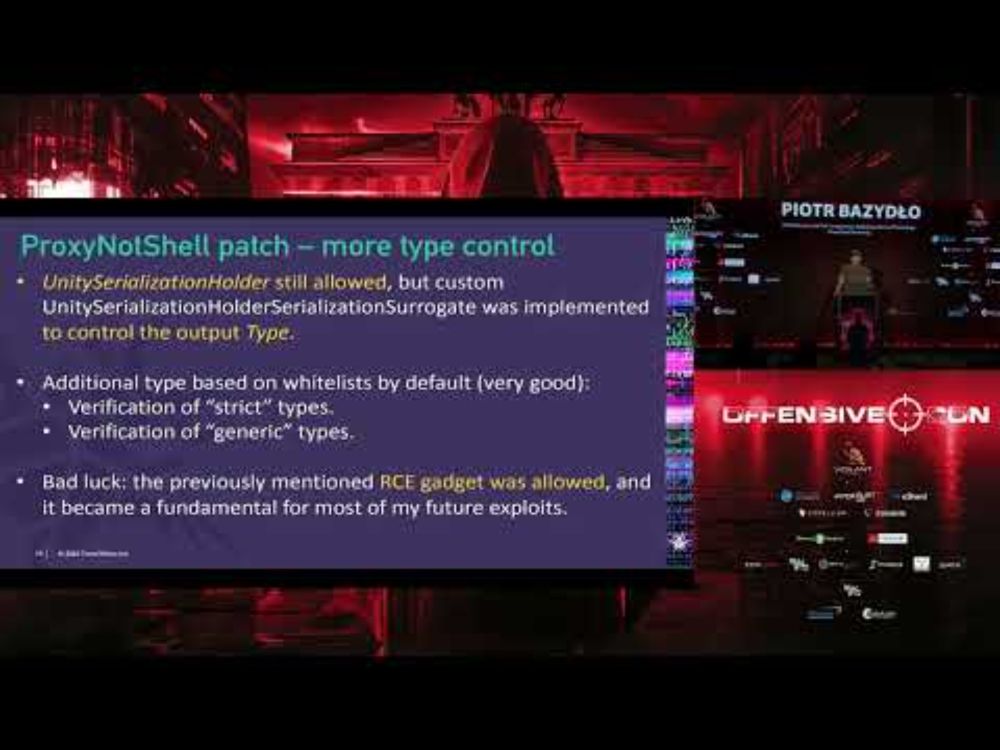
Several RCE chains included.
www.youtube.com/watch?v=AxNO...

I'll discuss it during Black Hat EU and I'll drop a paper afterwards 🫡
www.blackhat.com/eu-25/briefi...

I'll discuss it during Black Hat EU and I'll drop a paper afterwards 🫡
www.blackhat.com/eu-25/briefi...
Here I am today, writing a new whitepaper. You never know the day 😅
Here I am today, writing a new whitepaper. You never know the day 😅
Ivanti EPMM: CVE-2025-4427 and CVE-2025-4428 pre-auth RCE chain.
labs.watchtowr.com/expression-p...

Ivanti EPMM: CVE-2025-4427 and CVE-2025-4428 pre-auth RCE chain.
labs.watchtowr.com/expression-p...
Aren't you afraid of missing some key datails by outsourcing huge tasks to AI? I am.
If you rely on a tool, you're as good as your tool. If AI screws in a huge project, you probably won't even notice that.
Aren't you afraid of missing some key datails by outsourcing huge tasks to AI? I am.
If you rely on a tool, you're as good as your tool. If AI screws in a huge project, you probably won't even notice that.
I would never do this research without @SinSinology He insisted a lot, thx man. 😅
If you know CVE-2024-40711, this vuln can be patch-diffed and exploit armed in 5 minutes. Unfortunately, it's super simple.
labs.watchtowr.com/by-executive...

I would never do this research without @SinSinology He insisted a lot, thx man. 😅
If you know CVE-2024-40711, this vuln can be patch-diffed and exploit armed in 5 minutes. Unfortunately, it's super simple.
labs.watchtowr.com/by-executive...
labs.watchtowr.com/bypassing-au...

labs.watchtowr.com/bypassing-au...
Bad news: It overlaps with my kid's estimated due date 😅
Happy hacking to all of you who's planning to go to Redmond 😎

Bad news: It overlaps with my kid's estimated due date 😅
Happy hacking to all of you who's planning to go to Redmond 😎
I haven't done that for several years, and it seems that the wait time is much bigger nowadays 🤔
I haven't done that for several years, and it seems that the wait time is much bigger nowadays 🤔

www.ambionics.io/blog/iconv-c...
www.ambionics.io/blog/lightye...
www.ambionics.io/blog/iconv-c...
www.ambionics.io/blog/lightye...
chudypb.github.io/exchange-powershell.html
chudypb.github.io/exchange-powershell.html
Does it work for a setup with a VM on a half of the screen and browser/IDE on the second half?🤔
Does it work for a setup with a VM on a half of the screen and browser/IDE on the second half?🤔
New challenges and adventures are starting in 2025 :)
PS. Watch out for the ZDI blog, as several of my posts should appear there in 2025.
New challenges and adventures are starting in 2025 :)
PS. Watch out for the ZDI blog, as several of my posts should appear there in 2025.
Talk: www.youtube.com/watch?v=_CJm...
White paper: github.com/thezdi/prese...
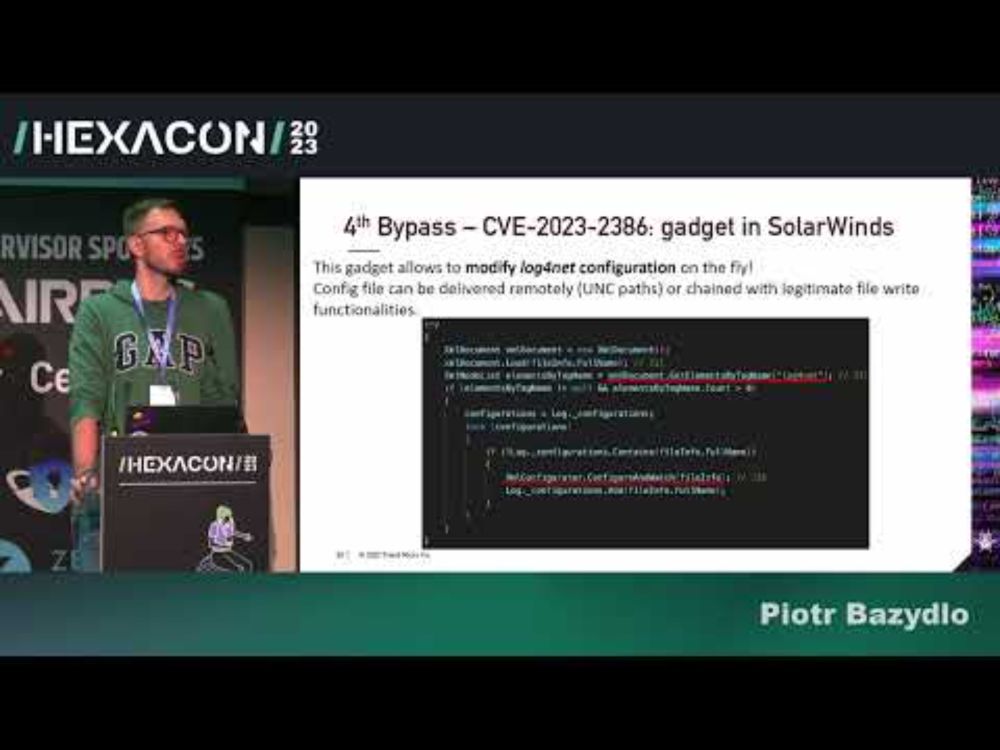
Talk: www.youtube.com/watch?v=_CJm...
White paper: github.com/thezdi/prese...
- Arbitrary File Write to drop DLL.
- Arbitrary FIle Read to leak DLL drop location
- DLL load gadget.
www.zerodayinitiative.com/blog/2024/9/...

- Arbitrary File Write to drop DLL.
- Arbitrary FIle Read to leak DLL drop location
- DLL load gadget.
www.zerodayinitiative.com/blog/2024/9/...
Several RCE chains included.
www.youtube.com/watch?v=AxNO...

Several RCE chains included.
www.youtube.com/watch?v=AxNO...
Let's kick off with SharePoint XXE blog, which could be abused due to URL parsing confusion between SharePoint and .NET components:
www.zerodayinitiative.com/blog/2024/5/...

Let's kick off with SharePoint XXE blog, which could be abused due to URL parsing confusion between SharePoint and .NET components:
www.zerodayinitiative.com/blog/2024/5/...

Remote Code Execution with Spring Properties :: srcincite.io/blog/2024/11...


