github.blog/security/ai-...

github.blog/security/ai-...
And of course, the framework is open source.

And of course, the framework is open source.


if you're thinking about automating a trivial task for the third time: just do it now!
It doesn't need to be something complicated, often a shell script is enough. $1 refers to the first argument passed to the shell script. (noted so I don't forget 😉)
if you're thinking about automating a trivial task for the third time: just do it now!
It doesn't need to be something complicated, often a shell script is enough. $1 refers to the first argument passed to the shell script. (noted so I don't forget 😉)
It looks like Einstein never used LLMs.
It looks like Einstein never used LLMs.
If you are using WooCommerce, please update. For more info see:
developer.woocommerce.com/2025/12/22/s...

If you are using WooCommerce, please update. For more info see:
developer.woocommerce.com/2025/12/22/s...
This is a great opportunity to get involved in Open Source projects like @assertj.github.io, with direct guidance from the maintainers!
switzerland2025.hack-commit-pu.sh
This is a great opportunity to get involved in Open Source projects like @assertj.github.io, with direct guidance from the maintainers!
We recently announced upcoming changes to the pull_request_target event and environment protection rules to make GitHub Actions more secure by default.
We’ve opened a discussion to gather feedback 👇
🔗 github.com/orgs/communi...
We recently announced upcoming changes to the pull_request_target event and environment protection rules to make GitHub Actions more secure by default.
We’ve opened a discussion to gather feedback 👇
🔗 github.com/orgs/communi...
Join us at the GitHub booth at 15:30 for the GitHub Quiz 🧠
Test your security knowledge, win exclusive GitHub swag, grab some stickers, and chat with our experts!
👉 gh.io/eko

Check out our plan to create a more secure future for the JavaScript community.👇
https://github.blog/security/supply-chain-security/our-plan-for-a-more-secure-npm-supply-chain/

Check out our plan to create a more secure future for the JavaScript community.👇
https://github.blog/security/supply-chain-security/our-plan-for-a-more-secure-npm-supply-chain/


Prompt injections are a real and growing threat for VS Code Copilot Agent.
Learn how these attacks work and how you can defend your environment.
Read the full research: github.blog/security/vul...

Prompt injections are a real and growing threat for VS Code Copilot Agent.
Learn how these attacks work and how you can defend your environment.
Read the full research: github.blog/security/vul...
My wife and I are urgently looking for a specialist in neuropediatrics or a similar field for our autistic child with a diagnosed, but not further specified, movement disorder [1/4]
My wife and I are urgently looking for a specialist in neuropediatrics or a similar field for our autistic child with a diagnosed, but not further specified, movement disorder [1/4]
Want your project to be part of this effort? Now’s the time to get involved! 💪
🔗 Find out more: github.blog/open-source/...

Want your project to be part of this effort? Now’s the time to get involved! 💪
🔗 Find out more: github.blog/open-source/...
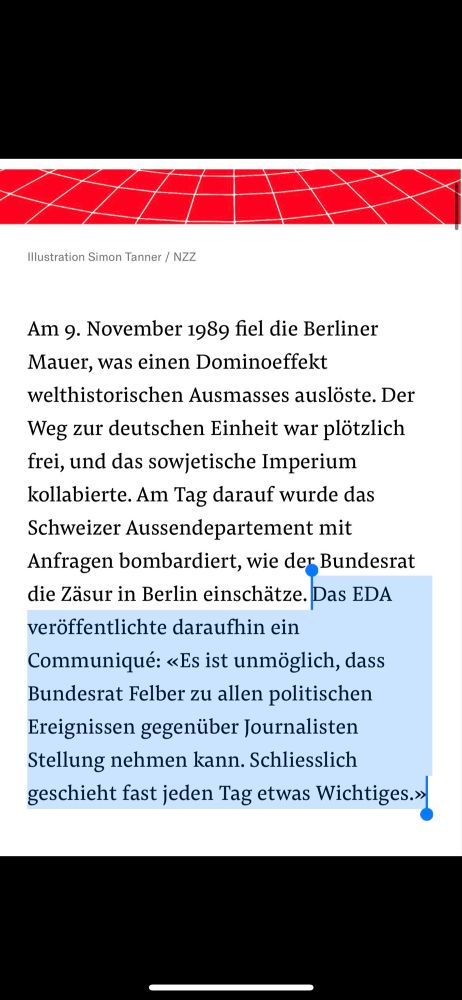


hexarcana.ch/lp/files/?ut...

hexarcana.ch/lp/files/?ut...
github.blog/security/sig...
github.blog/security/sig...
We are a team of security experts who cultivate a collaborative community where developers and security professionals come together to secure open source software.
We are a team of security experts who cultivate a collaborative community where developers and security professionals come together to secure open source software.