Organisers of the annual Virus Bulletin conference.

More details coming soon on the venue, call for papers, sponsorship opportunities, and how to join us.
Can't wait to see you there!

CfP rules and submissions here: pretalx.com/pivotcon26/cfp
#ThreatIntel #ThreatResearch #CTI

CfP rules and submissions here: pretalx.com/pivotcon26/cfp
#ThreatIntel #ThreatResearch #CTI


It’s time to retire outdated cyber advice! More than 80 cybersecurity veterans have signed an open letter urging a shift from folklore to guidance that actually helps people avoid the most common attacks. 🔐
Blog: medium.com/@boblord/let...
Site: www.hacklore.org
It’s time to retire outdated cyber advice! More than 80 cybersecurity veterans have signed an open letter urging a shift from folklore to guidance that actually helps people avoid the most common attacks. 🔐
Blog: medium.com/@boblord/let...
Site: www.hacklore.org




Troopers - www.youtube.com/playlist?lis...
Hexacon - www.youtube.com/playlist?lis...
Bsides Canberra - www.youtube.com/playlist?lis...
NYMJCSC - www.youtube.com/playlist?lis...
VirusBulletin - www.youtube.com/playlist?lis...

Troopers - www.youtube.com/playlist?lis...
Hexacon - www.youtube.com/playlist?lis...
Bsides Canberra - www.youtube.com/playlist?lis...
NYMJCSC - www.youtube.com/playlist?lis...
VirusBulletin - www.youtube.com/playlist?lis...
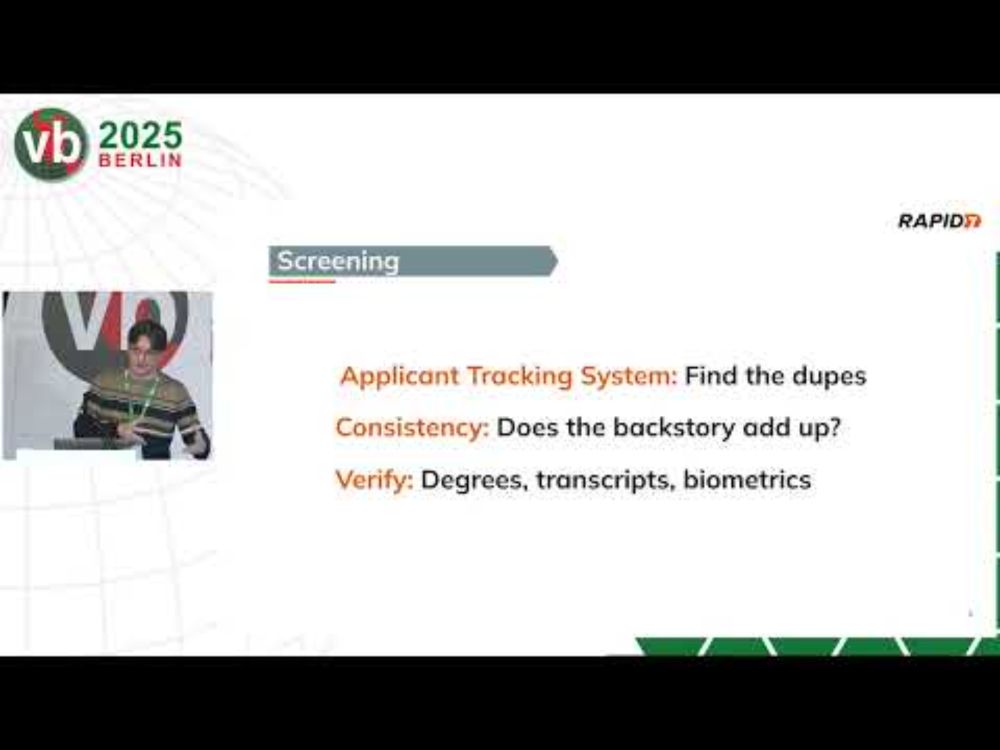
TIPS is a mini-summit within the VB Conference that unites analysts, researchers, operators, and developers to address the key challenges and successes in threat intelligence.
www.youtube.com/playlist?lis...

TIPS is a mini-summit within the VB Conference that unites analysts, researchers, operators, and developers to address the key challenges and successes in threat intelligence.
www.youtube.com/playlist?lis...












