
I want to give a special shout out to @cxiao.net (Thank You 🙏) who provided valuable feedback making the plugin experience better.
Happy rule writing!
Learn more @ github.com/xorhex/BinYars

I want to give a special shout out to @cxiao.net (Thank You 🙏) who provided valuable feedback making the plugin experience better.
Happy rule writing!
Learn more @ github.com/xorhex/BinYars




CfP rules and submissions here: pretalx.com/pivotcon26/cfp
#ThreatIntel #ThreatResearch #CTI

CfP rules and submissions here: pretalx.com/pivotcon26/cfp
#ThreatIntel #ThreatResearch #CTI
forms.gle/i3n4srD6hWzf...

forms.gle/i3n4srD6hWzf...
For those able to use #BinaryNinja projects; #BinYars can sort the files into folders based upon the #Yara-X rule metadata field, BNFolder. The folder nesting structure is determined by the number of matches that reside under each folder - check out the video below!

github.com/VirusTotal/y...

github.com/VirusTotal/y...
Normally when Steam\bin\steam_monitor.exe loads up, it will load Steam\crashhandler.dll as part of the loading process.
When loading the crashhandler.dll dependency, steam_monitor.exe checks for the path of the tier0_s.dll to-

Normally when Steam\bin\steam_monitor.exe loads up, it will load Steam\crashhandler.dll as part of the loading process.
When loading the crashhandler.dll dependency, steam_monitor.exe checks for the path of the tier0_s.dll to-


Stream live on Twitch or YouTube
h̲t̲t̲p̲s̲://w̲w̲w̲.t̲w̲i̲t̲c̲h̲.t̲v̲/b̲s̲i̲d̲e̲s̲p̲y̲o̲n̲g̲y̲a̲n̲g̲
Stream live on Twitch or YouTube
h̲t̲t̲p̲s̲://w̲w̲w̲.t̲w̲i̲t̲c̲h̲.t̲v̲/b̲s̲i̲d̲e̲s̲p̲y̲o̲n̲g̲y̲a̲n̲g̲
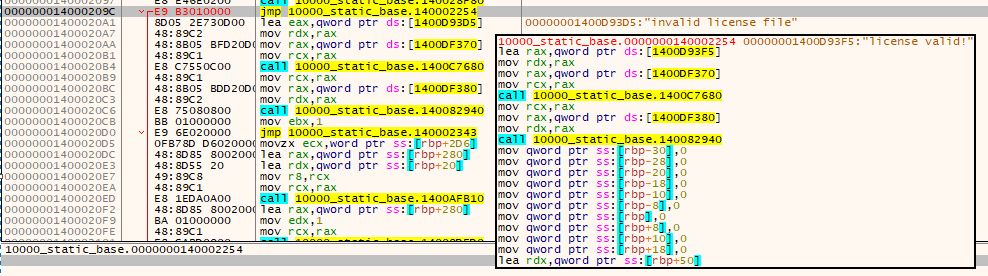
Assumptions:
- Null terminated string
- It's a string pointer versus a string match, so ! won't work
- variable name: offset
- length =< 100
Assumptions:
- Null terminated string
- It's a string pointer versus a string match, so ! won't work
- variable name: offset
- length =< 100
disksnapshot -c -k -v c:\test
will print out file info including sha256 for every file in the directory

disksnapshot -c -k -v c:\test
will print out file info including sha256 for every file in the directory

With some of our most requested features of all time including bitfield support, containers, hexagon, Ghidra import, and a huge upgrade to TTD capabilities, plus a ton more, make sure to check out the changelog!

With some of our most requested features of all time including bitfield support, containers, hexagon, Ghidra import, and a huge upgrade to TTD capabilities, plus a ton more, make sure to check out the changelog!
Please read carefully the whole 🧵 for the rules about invite -> registration (1/6)🌐

Please read carefully the whole 🧵 for the rules about invite -> registration (1/6)🌐
We uncover how German ISP aurologic GmbH has become a central nexus for high-risk hosting networks, sustaining large concentrations of malicious infrastructure.

