
Report also has interesting stories about state actors' AI use.





After two second places and a third place, Paddy won the AvD-Histo-Tour 2025 in the Sanduhr category! He raced at the legendary Nordschleife, the Nürburgring Grand Prix Sprint race track, Circuit de Spa-Francorchamps, and Circuit Zolder. Good things come to […]
After two second places and a third place, Paddy won the AvD-Histo-Tour 2025 in the Sanduhr category! He raced at the legendary Nordschleife, the Nürburgring Grand Prix Sprint race track, Circuit de Spa-Francorchamps, and Circuit Zolder. Good things come to […]
Also includes ESC1 over Intune (in some cases).
dirkjanm.io/extending-ad...
Oh, and a new tool for SCEP: github.com/dirkjanm/sce...
Also includes ESC1 over Intune (in some cases).
dirkjanm.io/extending-ad...
Oh, and a new tool for SCEP: github.com/dirkjanm/sce...
An article about the key components of Command and Control (C2), highlights potential detection vectors, and outlines high-level strategies for designing resilient and stealthy C2 infrastructure by @m8r1us
https://www.scip.ch/en/?labs.20250612

* Support for Intune is a work in progress. I have implemented the first checks and updated a lot of findings
* Added CIS Benchmark lists for Windows 11 and Windows Server 2025
* The Windows 11 24H4 CIS list is the first to include Intune recommendations (though not yet […]
* Support for Intune is a work in progress. I have implemented the first checks and updated a lot of findings
* Added CIS Benchmark lists for Windows 11 and Windows Server 2025
* The Windows 11 24H4 CIS list is the first to include Intune recommendations (though not yet […]
Another failed standard?
www.linkedin.com/feed/update/...

Another failed standard?
www.linkedin.com/feed/update/...
If this query hits, you're DA: www.akamai.com/blog/securit...
If this query hits, you're DA: www.akamai.com/blog/securit...
blog.compass-security.com/2025/05/bypa...
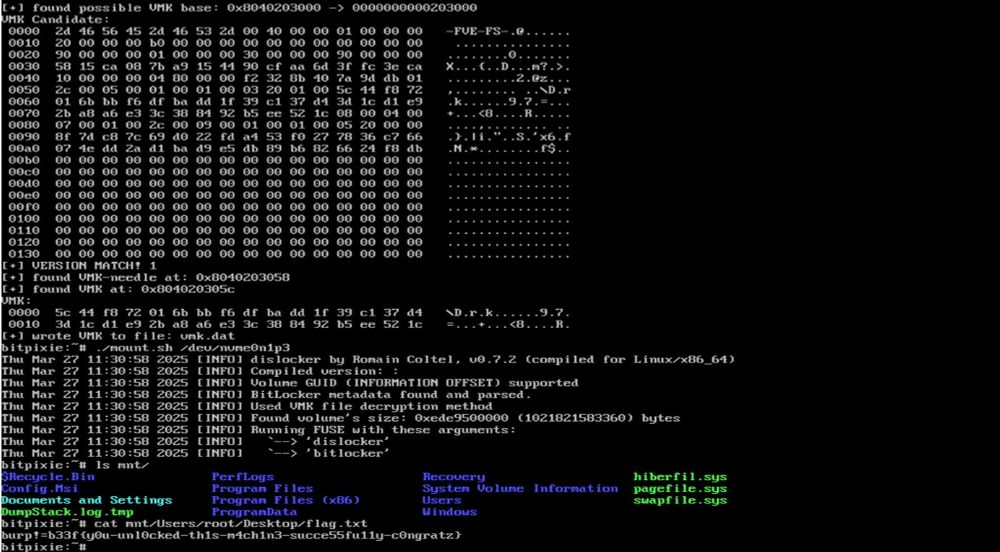
blog.compass-security.com/2025/05/bypa...
Well with the new version, MacroPack Pro is now also a powerful assembly obfuscation/weaponization tool ! 😎
We wrote a tutorial about that here:
blog.balliskit.com/obfuscation-...

Well with the new version, MacroPack Pro is now also a powerful assembly obfuscation/weaponization tool ! 😎
We wrote a tutorial about that here:
blog.balliskit.com/obfuscation-...
https://github.com/0x6d69636b/windows_hardening/releases/tag/v.0.9.3

https://github.com/0x6d69636b/windows_hardening/releases/tag/v.0.9.3
Today, we're releasing NachoVPN, our VPN client exploitation tool, as presented at SANS HackFest Hollywood. Get it on the @amberwolfsec.bsky.social blog:
blog.amberwolf.com/blog/2024/no...
Today, we're releasing NachoVPN, our VPN client exploitation tool, as presented at SANS HackFest Hollywood. Get it on the @amberwolfsec.bsky.social blog:
blog.amberwolf.com/blog/2024/no...
ShadowHound is a PowerShell alternative to SharpHound for Active Directory enumeration, using native PowerShell or ADModule (ADWS). As a bonus I also talk about some MDI detections and how to avoid them.
blog.fndsec.net/2024/11/25/s...


ShadowHound is a PowerShell alternative to SharpHound for Active Directory enumeration, using native PowerShell or ADModule (ADWS). As a bonus I also talk about some MDI detections and how to avoid them.
blog.fndsec.net/2024/11/25/s...
www.cisa.gov/news-events/...
www.cisa.gov/news-events/...
Please follow that profile, I will mostly post there and do not cross post to keep your timeline clean ;-)
Please follow that profile, I will mostly post there and do not cross post to keep your timeline clean ;-)
www.scip.ch/en/?labs.202...
www.scip.ch/en/?labs.202...


