akamai.com/blog/securit...
Credits Ori David
#infosec #linux

akamai.com/blog/securit...
Credits Ori David
#infosec #linux
I didn't have admin rights and was trying to capture network traffic from a pop-up, so Dev Tools wasn't working
Apparently this is built into Chrome/Edge! So cool :)
edge://net-export/
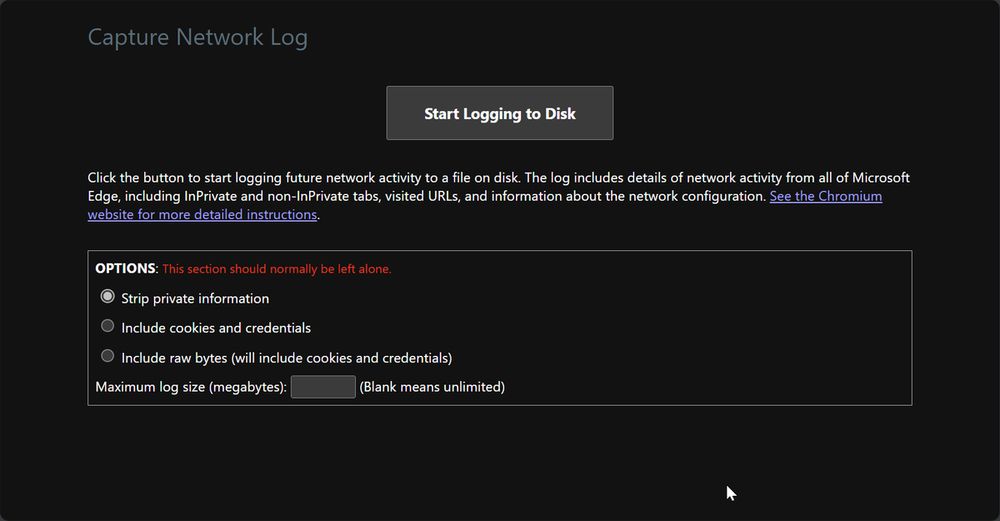
I didn't have admin rights and was trying to capture network traffic from a pop-up, so Dev Tools wasn't working
Apparently this is built into Chrome/Edge! So cool :)
edge://net-export/
#dfir #blueteam #cybersecurity

#dfir #blueteam #cybersecurity

