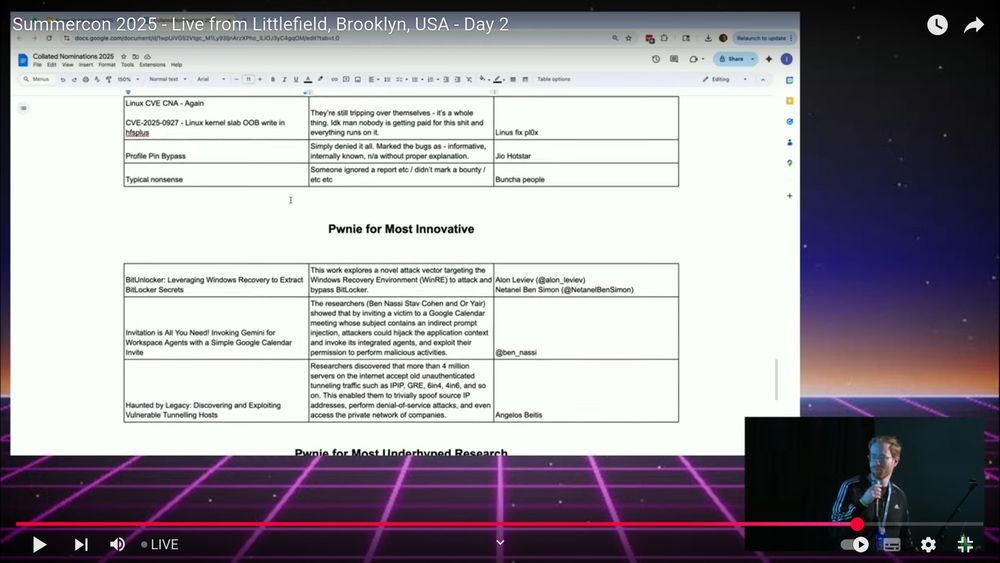
Posts
Media
Videos
Starter Packs
Reposted by aurelsec
Reposted by aurelsec
Reposted by aurelsec
Reposted by aurelsec
Reposted by aurelsec
Reposted by aurelsec
Reposted by aurelsec
Reposted by aurelsec
Reposted by aurelsec
Reposted by aurelsec
Daniel Klischies
@dklischies.bsky.social
· May 11
Reposted by aurelsec
Micah Lee
@micahflee.com
· May 6
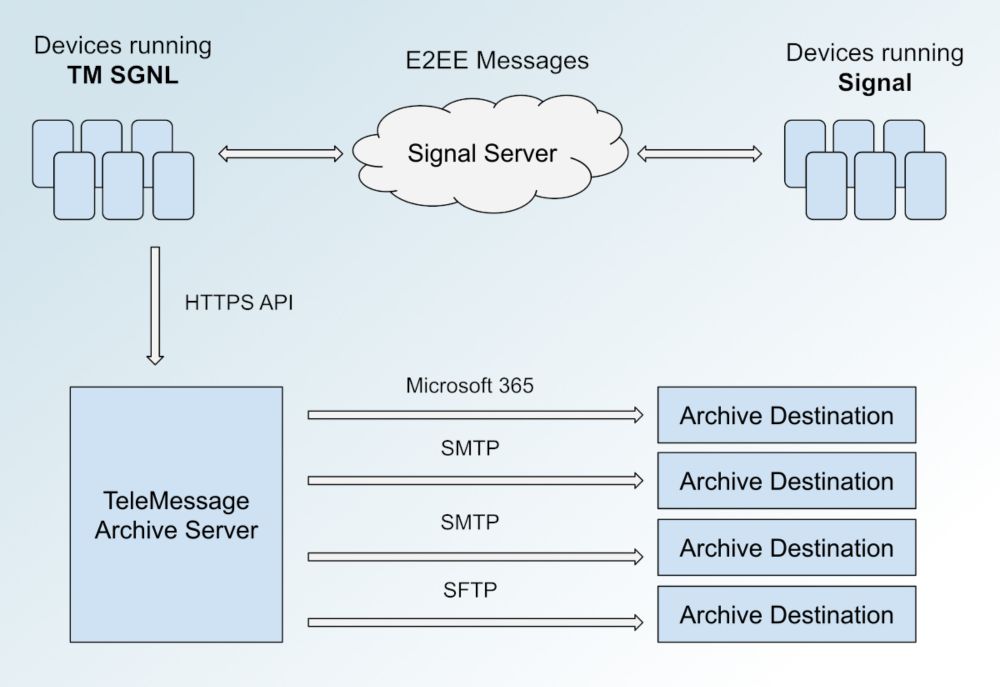
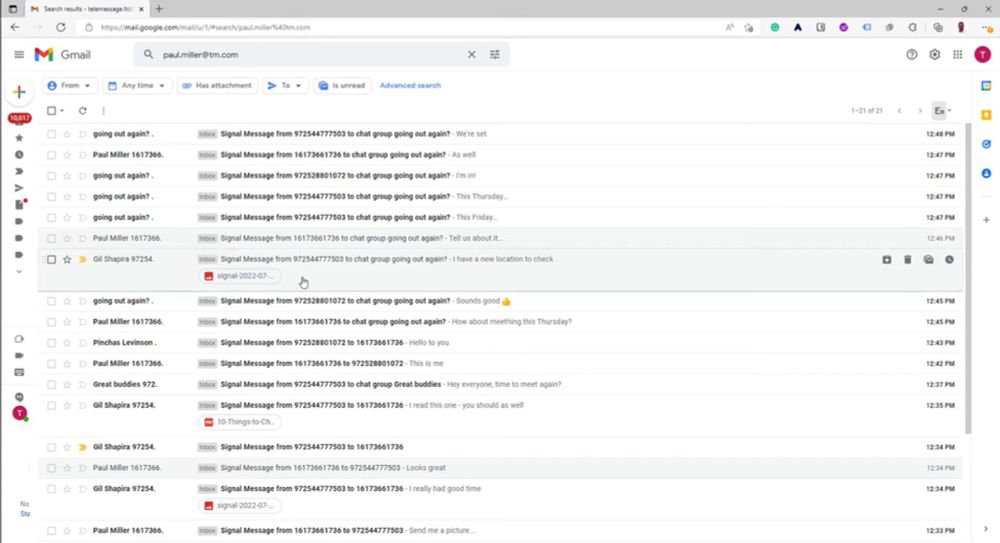
Despite misleading marketing, Israeli company TeleMessage, used by Trump officials, can access plaintext chat logs
Despite their misleading marketing, TeleMessage, the company that makes a modified version of Signal used by senior Trump officials, can access plaintext chat logs from its customers.
In this post I ...
micahflee.com
Reposted by aurelsec
Micah Lee
@micahflee.com
· May 2
TM SGNL, the obscure unofficial Signal app Mike Waltz uses to text with Trump officials
Yesterday, a Reuters photographer captured a photo of the freshly-ousted former National Security Advisor Mike Waltz checking his Signal messages during a Trump cabinet meeting. If you're not familiar...
micahflee.com