

novayagazeta.eu/articles/202...

novayagazeta.eu/articles/202...

You should expect a low load of ~1 artifact for functionality/reproducibility assessments per cycle (max 3 for the whole year).
Please support Open Science and fill the form by Oct 17: forms.gle/WoYRX4govNY1... 🚀

You should expect a low load of ~1 artifact for functionality/reproducibility assessments per cycle (max 3 for the whole year).
Please support Open Science and fill the form by Oct 17: forms.gle/WoYRX4govNY1... 🚀
We’re so entrenched in the usual x86, ARM, RISC-V world, that most people have no idea what’s happening over in China.
LoongArch is a fully independent ISA that’s sorta MIPS…sorta RISC-V…and sorta x87!


We’re so entrenched in the usual x86, ARM, RISC-V world, that most people have no idea what’s happening over in China.
LoongArch is a fully independent ISA that’s sorta MIPS…sorta RISC-V…and sorta x87!
Studying the Use of CVEs in Academia, won distinguished paper award www.usenix.org/conference/u...
Discovering and Exploiting Vulnerable Tunnelling Hosts, won most innovative research Pwnie @ DEFCON www.usenix.org/conference/u...
Big thanks to all co-authors!!


Studying the Use of CVEs in Academia, won distinguished paper award www.usenix.org/conference/u...
Discovering and Exploiting Vulnerable Tunnelling Hosts, won most innovative research Pwnie @ DEFCON www.usenix.org/conference/u...
Big thanks to all co-authors!!
The work will be presented by Angelos Beitis at Black Hat and also at USENIX Security
Brief summary and code: github.com/vanhoefm/tun...
Paper: papers.mathyvanhoef.com/usenix2025-t...
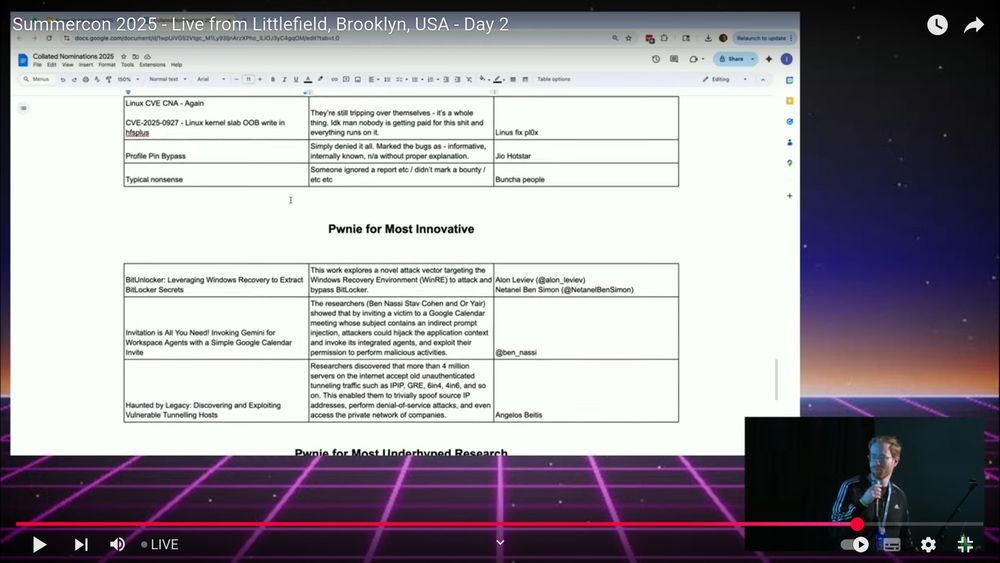
The work will be presented by Angelos Beitis at Black Hat and also at USENIX Security
Brief summary and code: github.com/vanhoefm/tun...
Paper: papers.mathyvanhoef.com/usenix2025-t...

ec.europa.eu/info/funding...
ec.europa.eu/info/funding...
Very informative and quite shocking. Give it a listen.

Very informative and quite shocking. Give it a listen.

You'll review artifacts of accepted papers. We especially encourage junior/senior PhD students & PostDocs to help. Distinguished reviews will get awards!
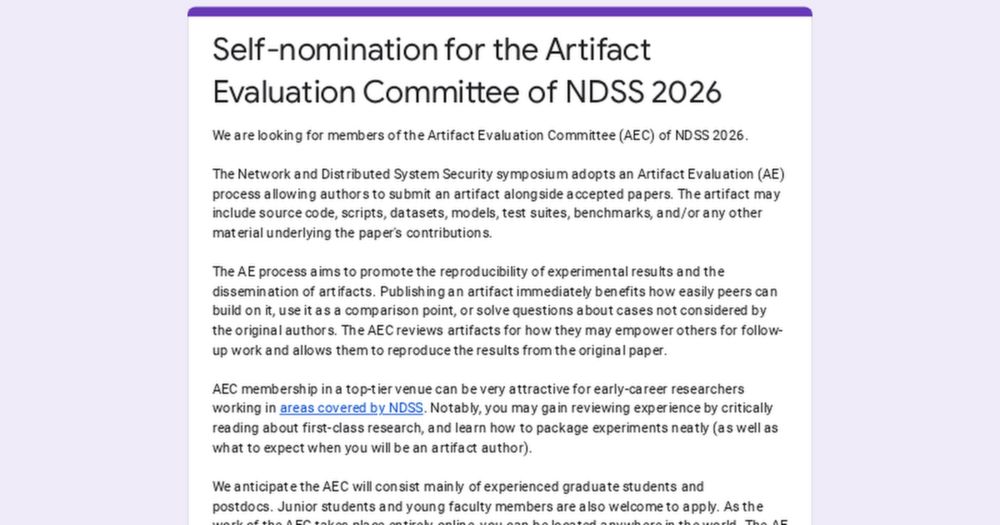
You'll review artifacts of accepted papers. We especially encourage junior/senior PhD students & PostDocs to help. Distinguished reviews will get awards!

You'll review artifacts of accepted papers. We especially encourage junior/senior PhD students & PostDocs to help. Distinguished reviews will get awards!
You'll review artifacts of accepted papers. We especially encourage junior/senior PhD students & PostDocs to help. Distinguished reviews will get awards!

You'll review artifacts of accepted papers. We especially encourage junior/senior PhD students & PostDocs to help. Distinguished reviews will get awards!
Have you worked with private grant consultants for EU research funding (Horizon, EIC, etc.)—Have you had positive or negative experiences?
📩 Share your story: [email protected] / [email protected] (@thordeyaert.bsky.social)
🔁 RT appreciated!

Have you worked with private grant consultants for EU research funding (Horizon, EIC, etc.)—Have you had positive or negative experiences?
📩 Share your story: [email protected] / [email protected] (@thordeyaert.bsky.social)
🔁 RT appreciated!
The number of pages clearly keeps increasing. That includes more features to defend networks, but also more features to potentially abuse 👀

The number of pages clearly keeps increasing. That includes more features to defend networks, but also more features to potentially abuse 👀


