Posts
Media
Videos
Starter Packs
Reposted by Mark Kelly
Mark Kelly
@mkyo.bsky.social
· 22d
Mark Kelly
@mkyo.bsky.social
· 22d
Mark Kelly
@mkyo.bsky.social
· 27d
Mark Kelly
@mkyo.bsky.social
· Jul 16

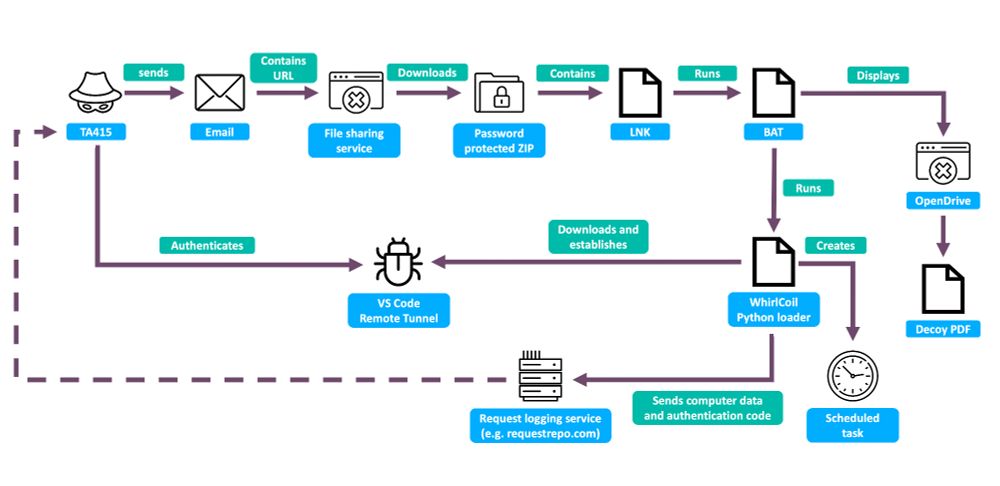
Phish and Chips: China-Aligned Espionage Actors Ramp Up Taiwan Semiconductor Industry Targeting | Proofpoint US
Key findings Between March and June 2025, Proofpoint Threat Research observed three Chinese state-sponsored threat actors conduct targeted phishing campaigns against the Taiwanese
www.proofpoint.com
Reposted by Mark Kelly
AJ Vicens
@ajvicens.bsky.social
· Jul 16

Exclusive: China-linked hackers target Taiwan's chip industry with increasing attacks, researchers say
Chinese-linked hackers are targeting the Taiwanese semiconductor industry and investment analysts as part of a string of cyber espionage campaigns, researchers said on Wednesday.
www.reuters.com
Reposted by Mark Kelly
Greg Lesnewich
@greg-l.bsky.social
· Jun 30

10 Things I Hate About Attribution: RomCom vs. TransferLoader | Proofpoint US
Threat Research would like to acknowledge and thank the Paranoids, Spur, and Pim Trouerbach for their collaboration to identify, track, and disrupt this activity. Key takeaways
www.proofpoint.com
Reposted by Mark Kelly
Calwarez
@calwarez.bsky.social
· Jun 20
Reposted by Mark Kelly
Saher
@saffronsec.bsky.social
· Jun 4

The Bitter End: Unraveling Eight Years of Espionage Antics—Part One | Proofpoint US
This is a two-part blog series, detailing research undertaken in collaboration with Threatray. Part two of this blog series can be found on their website here. Analyst note: Throughout
www.proofpoint.com
Reposted by Mark Kelly
Mark Kelly
@mkyo.bsky.social
· May 17
Mark Kelly
@mkyo.bsky.social
· May 13
Reposted by Mark Kelly
Reposted by Mark Kelly