
But one of the disclosed bugs involves the good old pipe character in Perl "filenames" 🤯
Another great investigation by the Qualys Threat Research Unit 💎
Talk: www.youtube.com/watch?v=_CJm...
White paper: github.com/thezdi/prese...
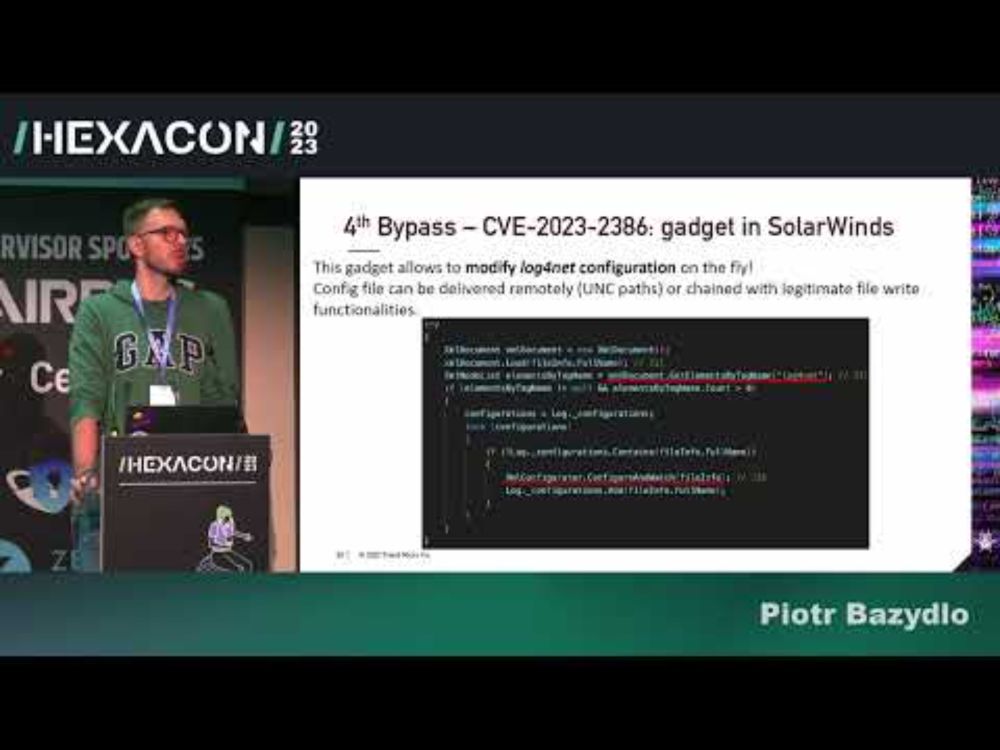
Talk: www.youtube.com/watch?v=_CJm...
White paper: github.com/thezdi/prese...
- Arbitrary File Write to drop DLL.
- Arbitrary FIle Read to leak DLL drop location
- DLL load gadget.
www.zerodayinitiative.com/blog/2024/9/...

- Arbitrary File Write to drop DLL.
- Arbitrary FIle Read to leak DLL drop location
- DLL load gadget.
www.zerodayinitiative.com/blog/2024/9/...
Several RCE chains included.
www.youtube.com/watch?v=AxNO...
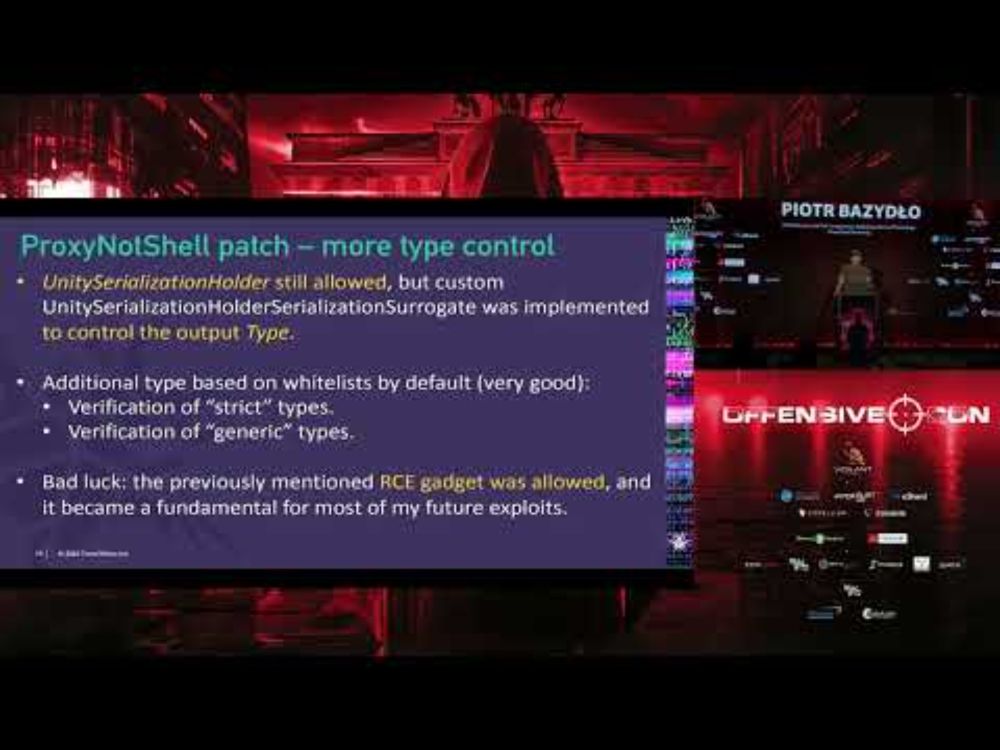
Several RCE chains included.
www.youtube.com/watch?v=AxNO...
Let's kick off with SharePoint XXE blog, which could be abused due to URL parsing confusion between SharePoint and .NET components:
www.zerodayinitiative.com/blog/2024/5/...

Let's kick off with SharePoint XXE blog, which could be abused due to URL parsing confusion between SharePoint and .NET components:
www.zerodayinitiative.com/blog/2024/5/...



