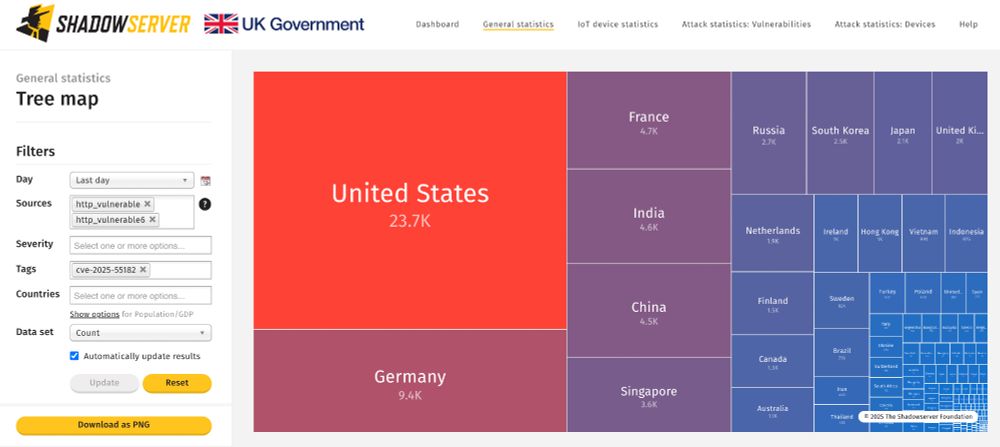
IP data is being shared in Vulnerable HTTP reports: www.shadowserver.org/what-we-do/n...
Dashboard geo breakdown: dashboard.shadowserver.org/statistics/c...
IP data is being shared in Vulnerable HTTP reports: www.shadowserver.org/what-we-do/n...
Dashboard geo breakdown: dashboard.shadowserver.org/statistics/c...
VulnCheck (vulncheck.com) continues to grow as we welcome them as a new Shadowserver Alliance Partner -Silver tier!
We look forward to enhancing our joint efforts to help network defenders globally with vulnerability management.

VulnCheck (vulncheck.com) continues to grow as we welcome them as a new Shadowserver Alliance Partner -Silver tier!
We look forward to enhancing our joint efforts to help network defenders globally with vulnerability management.

Data shared in a our Compromised Account Report www.shadowserver.org/what-we-do/n... (search for 2025-11-26 & compromised_account prefix)

Data shared in a our Compromised Account Report www.shadowserver.org/what-we-do/n... (search for 2025-11-26 & compromised_account prefix)
dashboard.shadowserver.org/statistics/c...

dashboard.shadowserver.org/statistics/c...
86M stolen data items from 525K victim IPs across 226 countries included in our new Rhadamanthys Historic Bot Victims Special Report, run overnight 2025-11-12
More details:
shadowserver.org/news/rhadama...

86M stolen data items from 525K victim IPs across 226 countries included in our new Rhadamanthys Historic Bot Victims Special Report, run overnight 2025-11-12
More details:
shadowserver.org/news/rhadama...
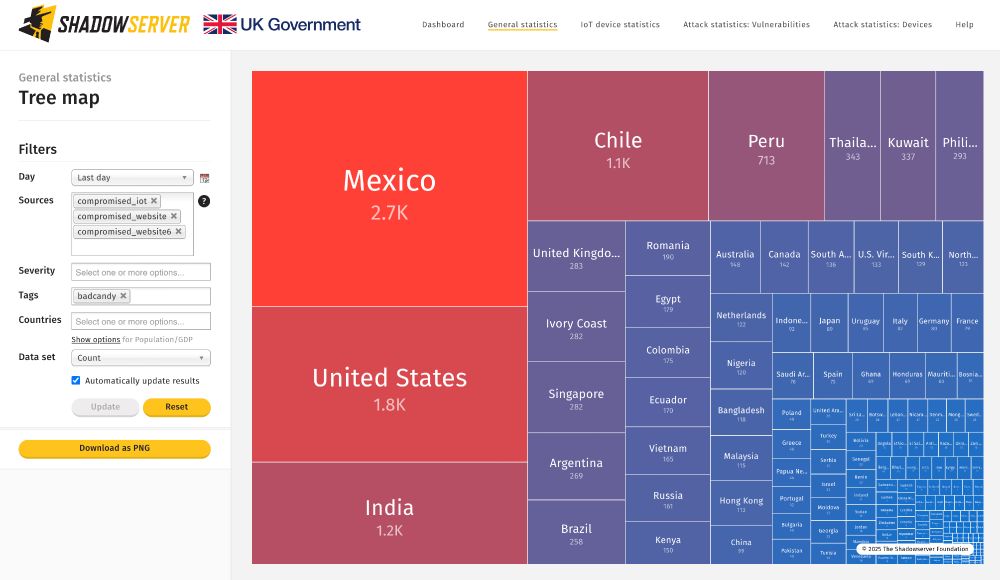
The Australian Signals Directorate (ASD) recently published an advisory on the BadCandy implant still present in many Cisco IOS XE devices: www.cyber.gov.au/about-us/vie...
We still see around 15 000 Cisco IOS XE devices with the implant
The Australian Signals Directorate (ASD) recently published an advisory on the BadCandy implant still present in many Cisco IOS XE devices: www.cyber.gov.au/about-us/vie...
We still see around 15 000 Cisco IOS XE devices with the implant
We found nearly 8898 unpatched DNS open resolvers on 2025-10-30, down to 6653 on 2025-11-01: dashboard.shadowserver.org/statistics/c...

We found nearly 8898 unpatched DNS open resolvers on 2025-10-30, down to 6653 on 2025-11-01: dashboard.shadowserver.org/statistics/c...

Top affected: US with 23.2K instances

Top affected: US with 23.2K instances
Operation SIMCARTEL
Great work everyone involved 👏
europol.europa.eu/media-press/...


Operation SIMCARTEL
Great work everyone involved 👏
europol.europa.eu/media-press/...
We are sharing daily IP data on F5 exposures in our Device ID www.shadowserver.org/what-we-do/n... (device_vendor set to F5).
~269K IPs seen daily, nearly half in US.
Geo breakdown: dashboard.shadowserver.org/statistics/i...

We are sharing daily IP data on F5 exposures in our Device ID www.shadowserver.org/what-we-do/n... (device_vendor set to F5).
~269K IPs seen daily, nearly half in US.
Geo breakdown: dashboard.shadowserver.org/statistics/i...
IP data in www.shadowserver.org/what-we-do/n...
World map view of likely vulnerable instances: dashboard.shadowserver.org/statistics/c...

IP data in www.shadowserver.org/what-we-do/n...
World map view of likely vulnerable instances: dashboard.shadowserver.org/statistics/c...
Around ~45K vulnerable seen on 2025-10-04

Around ~45K vulnerable seen on 2025-10-04
It identifies the use of known or very weak cryptographic secrets across a variety of web frameworks/platforms. 12168 IPs seen (2025-09-14) using "bad" secrets!

It identifies the use of known or very weak cryptographic secrets across a variety of web frameworks/platforms. 12168 IPs seen (2025-09-14) using "bad" secrets!
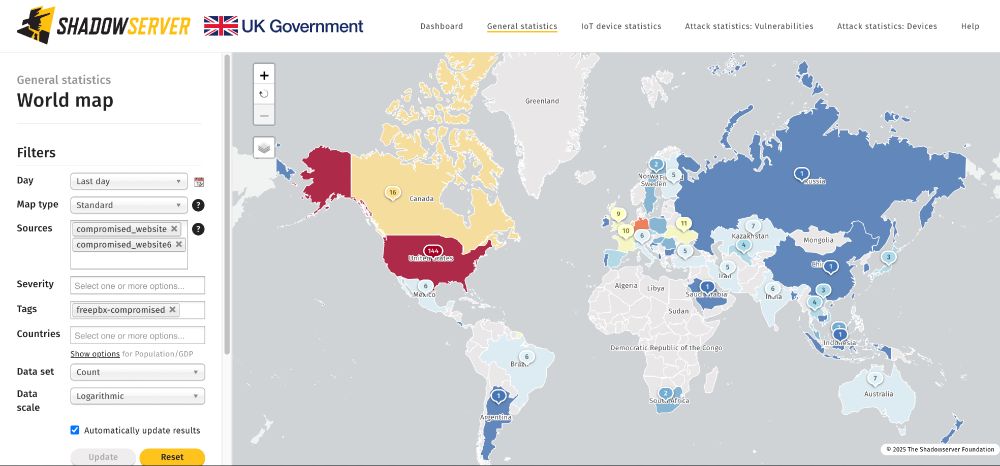
Dashboard links:
Vulnerable (unpatched): dashboard.shadowserver.org/statistics/c...
Compromised:
dashboard.shadowserver.org/statistics/c...

Dashboard links:
Vulnerable (unpatched): dashboard.shadowserver.org/statistics/c...
Compromised:
dashboard.shadowserver.org/statistics/c...
Patch info: support.citrix.com/support-home...
Top affected: US, Germany
Dashboard geo breakdown: dashboard.shadowserver.org/statistics/c...
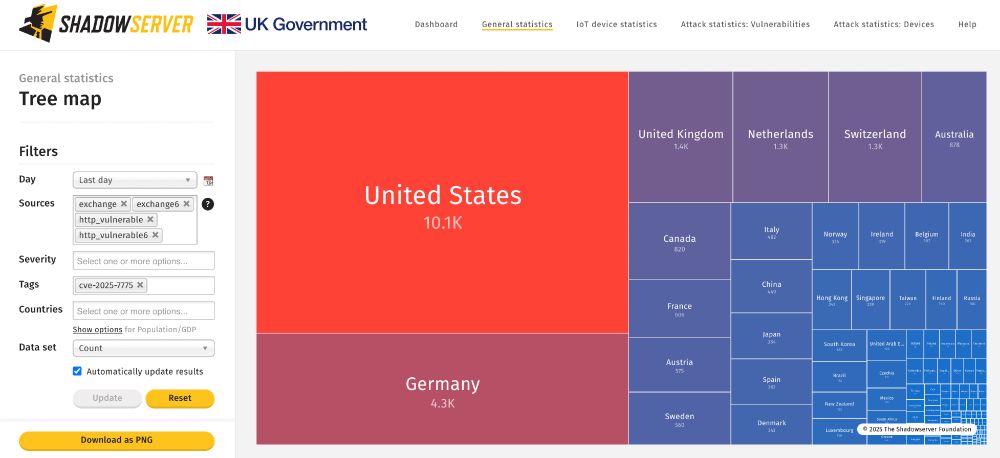
Report format: www.shadowserver.org/what-we-do/n...
Dashboard World map: dashboard.shadowserver.org/statistics/c...




Report format: www.shadowserver.org/what-we-do/n...
Dashboard World map: dashboard.shadowserver.org/statistics/c...
IP data on these scans shared in www.shadowserver.org/what-we-do/n...

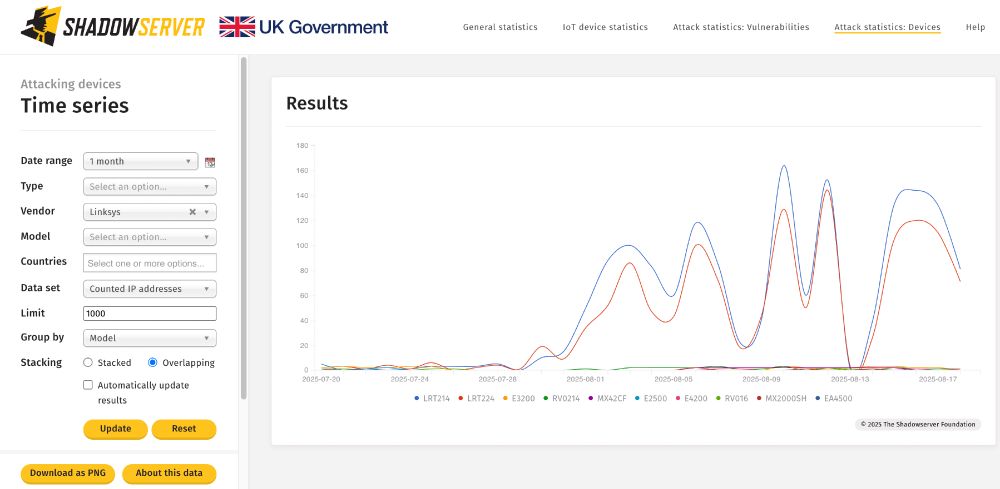

IP data on these scans shared in www.shadowserver.org/what-we-do/n...
Top affected: US, Canada, Netherlands, UK
Dashboard map view: dashboard.shadowserver.org/statistics/c...

Top affected: US, Canada, Netherlands, UK
Dashboard map view: dashboard.shadowserver.org/statistics/c...
Top affected: France, China, US, Germany


Top affected: France, China, US, Germany
Over 28K IPs unpatched (2025-08-07). Top affected: US, Germany, Russia
Dashboard world map: dashboard.shadowserver.org/statistics/c...


Over 28K IPs unpatched (2025-08-07). Top affected: US, Germany, Russia
Dashboard world map: dashboard.shadowserver.org/statistics/c...
Top affected: US, Japan, Germany
Dashboard map: dashboard.shadowserver.org/statistics/c...
NVD entry: nvd.nist.gov/vuln/detail/...

Top affected: US, Japan, Germany
Dashboard map: dashboard.shadowserver.org/statistics/c...
NVD entry: nvd.nist.gov/vuln/detail/...
CISA KEV catalog. We added version based detection of unpatched IPs with 129 seen (2025-08-03).
dashboard.shadowserver.org/statistics/c...
We also scan for CVE-2023-39143 & CVE-2023-27350. Data in Vulnerable HTTP: shadowserver.org/what-we-do/n...


CISA KEV catalog. We added version based detection of unpatched IPs with 129 seen (2025-08-03).
dashboard.shadowserver.org/statistics/c...
We also scan for CVE-2023-39143 & CVE-2023-27350. Data in Vulnerable HTTP: shadowserver.org/what-we-do/n...
Together with SURFcert and fellow Alliance Partners, we’re making the Internet more secure for all.
Read more about SURFcert:
www.surf.nl/en

Together with SURFcert and fellow Alliance Partners, we’re making the Internet more secure for all.
Read more about SURFcert:
www.surf.nl/en

