
#appsec #appsecurity #cve
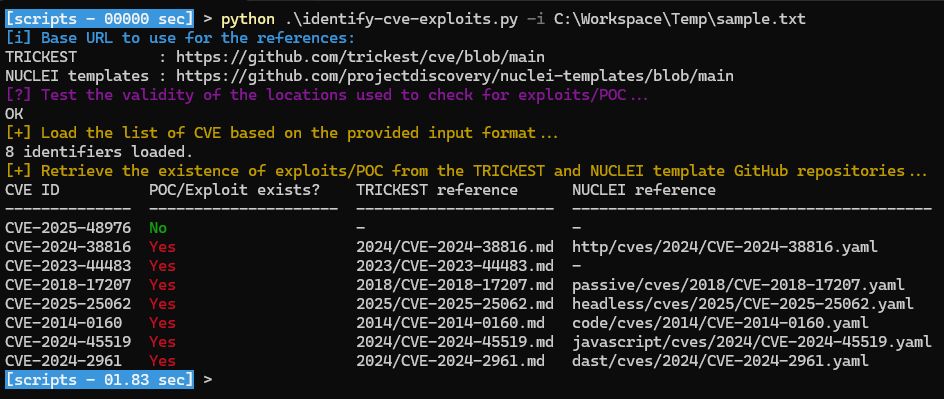
#appsec #appsecurity #cve





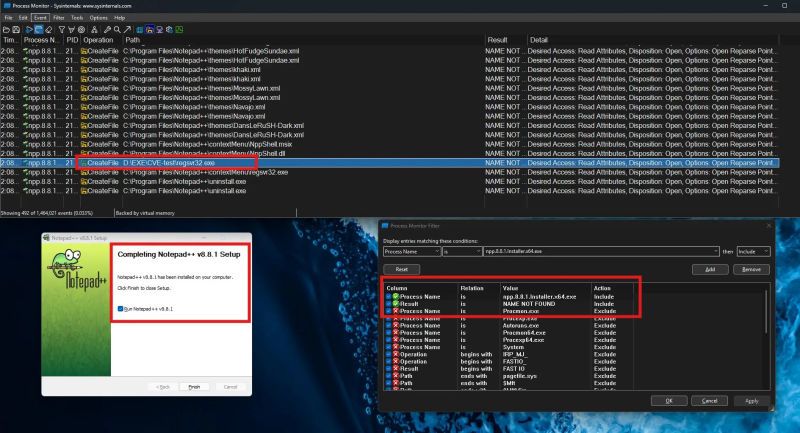
"Unexpected security footguns in Go's parsers"
#go #appsec #appsecurity
blog.trailofbits.com/2025/06/17/u...
"Unexpected security footguns in Go's parsers"
#go #appsec #appsecurity
blog.trailofbits.com/2025/06/17/u...

- Proper DNS
- PKI
- Automatic signed certificates
- New secrets management
- Proxmox clustering
- Cloud integration

- Proper DNS
- PKI
- Automatic signed certificates
- New secrets management
- Proxmox clustering
- Cloud integration



I procrastinated on this because, honestly, who cares about my writing process? But after repeatedly answering the same qns, I finally wrote this.
eugeneyan.com/writing/writ...
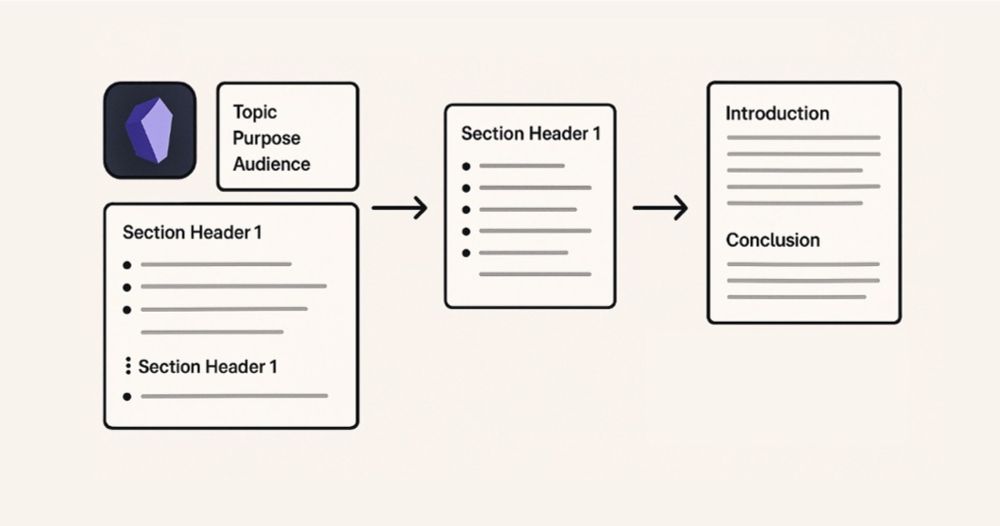
I procrastinated on this because, honestly, who cares about my writing process? But after repeatedly answering the same qns, I finally wrote this.
eugeneyan.com/writing/writ...

The new malware includes four new Linux rootkits (Puma, Pumatsune, Kitsune, and Megatsune) and the Bulldog backdoor.
rt-solar.ru/solar-4rays/...
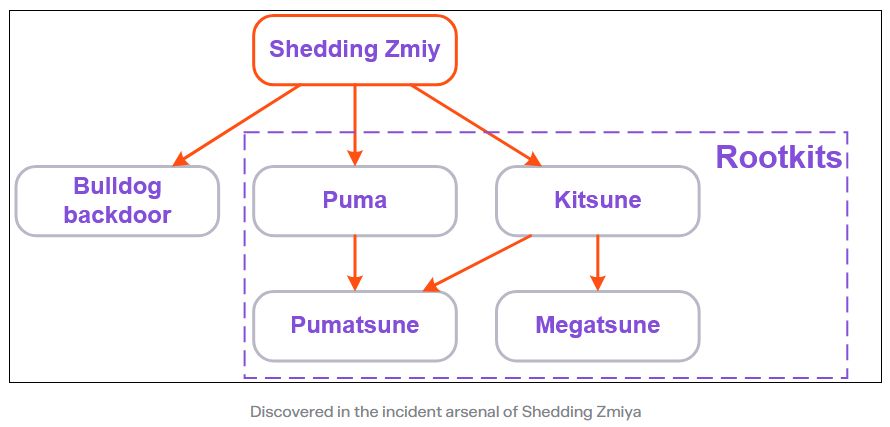
The new malware includes four new Linux rootkits (Puma, Pumatsune, Kitsune, and Megatsune) and the Bulldog backdoor.
rt-solar.ru/solar-4rays/...
www.zscaler.com/blogs/securi...

www.zscaler.com/blogs/securi...
www.metacurity.com/best-infosec...

www.metacurity.com/best-infosec...
Read the announcement here: old.reddit.com/r/cybersecur...
The code is on GitHub: github.com/TheFirewall-...
Read the announcement here: old.reddit.com/r/cybersecur...
The code is on GitHub: github.com/TheFirewall-...

