@hotnops.bsky.social explores cross-domain compromise tradecraft within the same tenant.
Read more: ghst.ly/3ISMGN9

@hotnops.bsky.social explores cross-domain compromise tradecraft within the same tenant.
Read more: ghst.ly/3ISMGN9
Basically the yellow pages for Microsoft first party apps.
#TROOPERS25
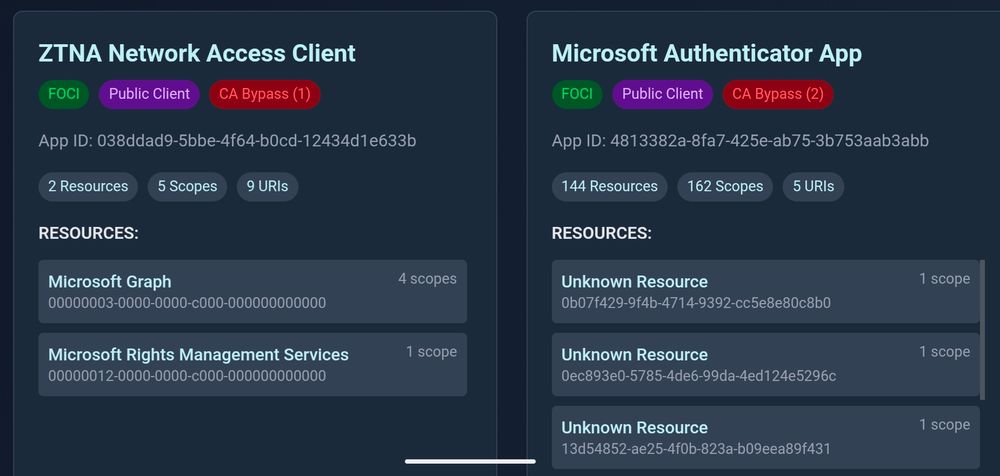
Basically the yellow pages for Microsoft first party apps.
#TROOPERS25
@subat0mik.bsky.social & @unsignedsh0rt.bsky.social dive into the research & its impact on the state of SCCM security. Read more: ghst.ly/460vI9d

@subat0mik.bsky.social & @unsignedsh0rt.bsky.social dive into the research & its impact on the state of SCCM security. Read more: ghst.ly/460vI9d
First dives into how we're improving the way BloodHound models attack paths through AD trusts: specterops.io/blog/2025/06...
Second covers an attack technique I came across while exploring AD trust abuse: specterops.io/blog/2025/06...
Hope you enjoy the read 🥳
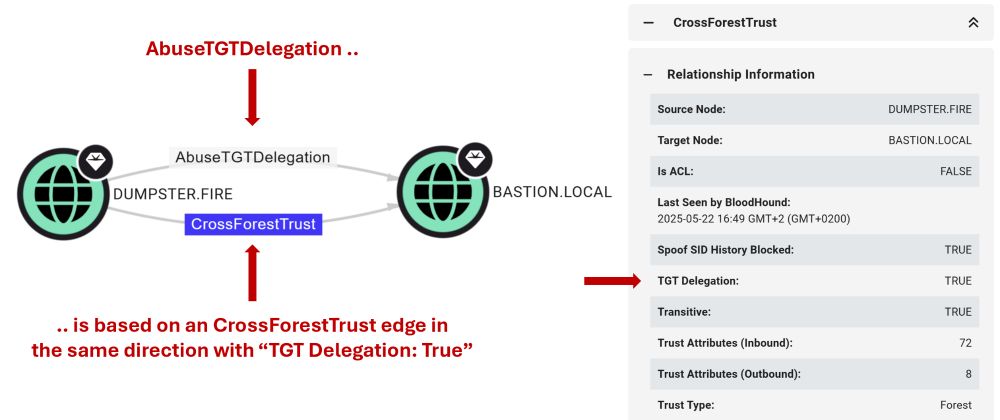
First dives into how we're improving the way BloodHound models attack paths through AD trusts: specterops.io/blog/2025/06...
Second covers an attack technique I came across while exploring AD trust abuse: specterops.io/blog/2025/06...
Hope you enjoy the read 🥳
Released with ~90 new Cypher queries, go check them out!
@joeydreijer.bsky.social and I spent many hours creating it and we hope you find it useful. All feedback is appreciated :)
Released with ~90 new Cypher queries, go check them out!
@joeydreijer.bsky.social and I spent many hours creating it and we hope you find it useful. All feedback is appreciated :)
@xpnsec.com covers the architecture, access controls, and why some legacy UAC bypass techniques remain effective in his latest blog post. ghst.ly/44mw5JM



bsky.app/profile/cnot...
- restricted permissions on Directory Synchronization Accounts role
- new dedicated sync app
Let’s find out how sync still works 🔍
Some old tricks persist—and new ones have emerged 💥
tenable.com/blog/despite... 🧵

bsky.app/profile/cnot...

dfir-delight.de/p/incident-c...
@moettle.bsky.social

dfir-delight.de/p/incident-c...
@moettle.bsky.social
Elad Shamir unpacks everything you need to know about NTLM & how the new edges help make identifying and visualizing these attack paths remarkably simple. ghst.ly/4lv3E31

Elad Shamir unpacks everything you need to know about NTLM & how the new edges help make identifying and visualizing these attack paths remarkably simple. ghst.ly/4lv3E31
Microsoft just introduced linkable identifiers in Microsoft Entra ID logs.
The bad guys 🥷 are going to hate this so much 😂
Learn more at learn.microsoft.com/...
Share the good news 👍

Microsoft just introduced linkable identifiers in Microsoft Entra ID logs.
The bad guys 🥷 are going to hate this so much 😂
Learn more at learn.microsoft.com/...
Share the good news 👍

Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;)
github.com/decoder-it/K...
Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;)
github.com/decoder-it/K...


cloud.google.com/blog/topics/...
cloud.google.com/blog/topics/...
Check out our latest blog post from Dev Bhatt to learn about the enhancements in this update, aimed at helping security teams visualize #AttackPaths, prioritize risks, & track remediation. ghst.ly/3CPDQwT
🧵: 1/4
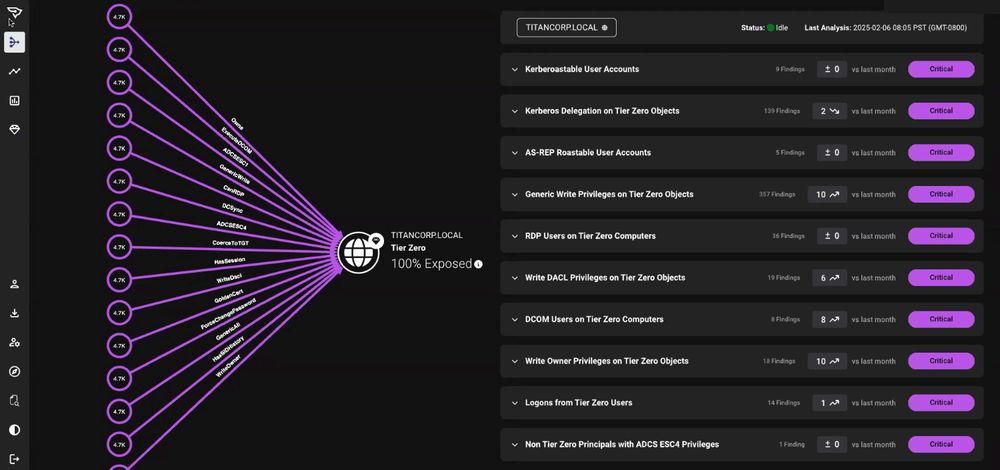
Check out our latest blog post from Dev Bhatt to learn about the enhancements in this update, aimed at helping security teams visualize #AttackPaths, prioritize risks, & track remediation. ghst.ly/3CPDQwT
🧵: 1/4
👇
www.reddit.com/r/ent...



👇
www.reddit.com/r/ent...
Microsoft just dropped a bunch of new least privilege Graph permissions.
Avoid granting super privileges like Directory.ReadWrite.All and User.ReadWrite.All to apps. Instead use these new least privilege permissions where possible.

Microsoft just dropped a bunch of new least privilege Graph permissions.
Avoid granting super privileges like Directory.ReadWrite.All and User.ReadWrite.All to apps. Instead use these new least privilege permissions where possible.

