A new report by @dianecoyle1859.bsky.social & Wendy Hall calls for urgent action. 👇
www.bennettinstitute.cam.ac.uk/publications...

A new report by @dianecoyle1859.bsky.social & Wendy Hall calls for urgent action. 👇
www.bennettinstitute.cam.ac.uk/publications...
Proud to live in a country (the Netherlands) that unconditionally supports Ukraine.
Europe needs to re-arm, to support Ukraine and defend itself and democracy.
Ukraine is the one defending Europe from Russian aggression. Ukraine should be part of the EU.
Slava Ukraini 🇺🇦
Proud to live in a country (the Netherlands) that unconditionally supports Ukraine.
Europe needs to re-arm, to support Ukraine and defend itself and democracy.
Ukraine is the one defending Europe from Russian aggression. Ukraine should be part of the EU.
Slava Ukraini 🇺🇦
learn.microsoft.com/en-us/securi...
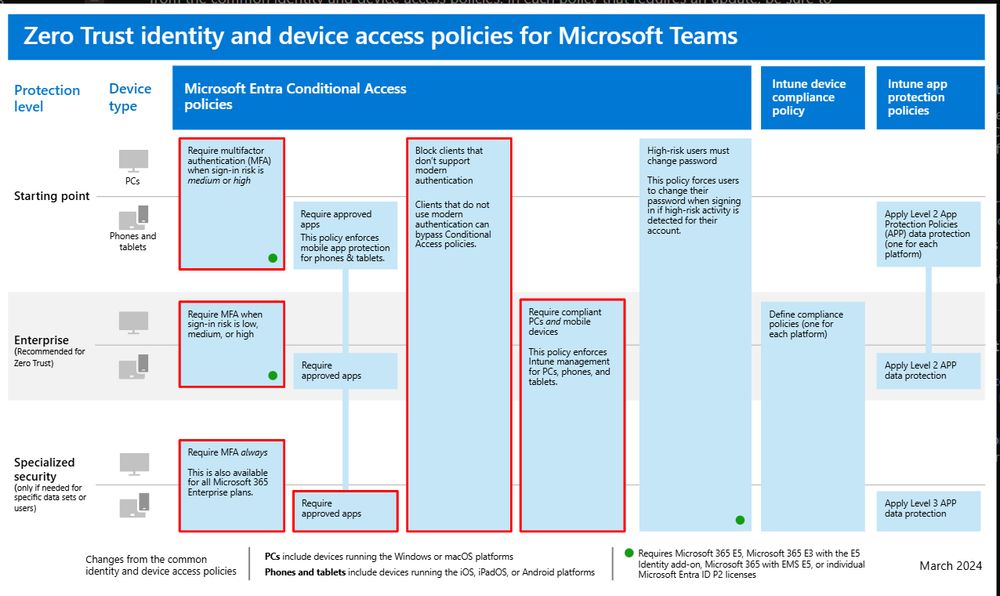
learn.microsoft.com/en-us/securi...
awseye.com

awseye.com
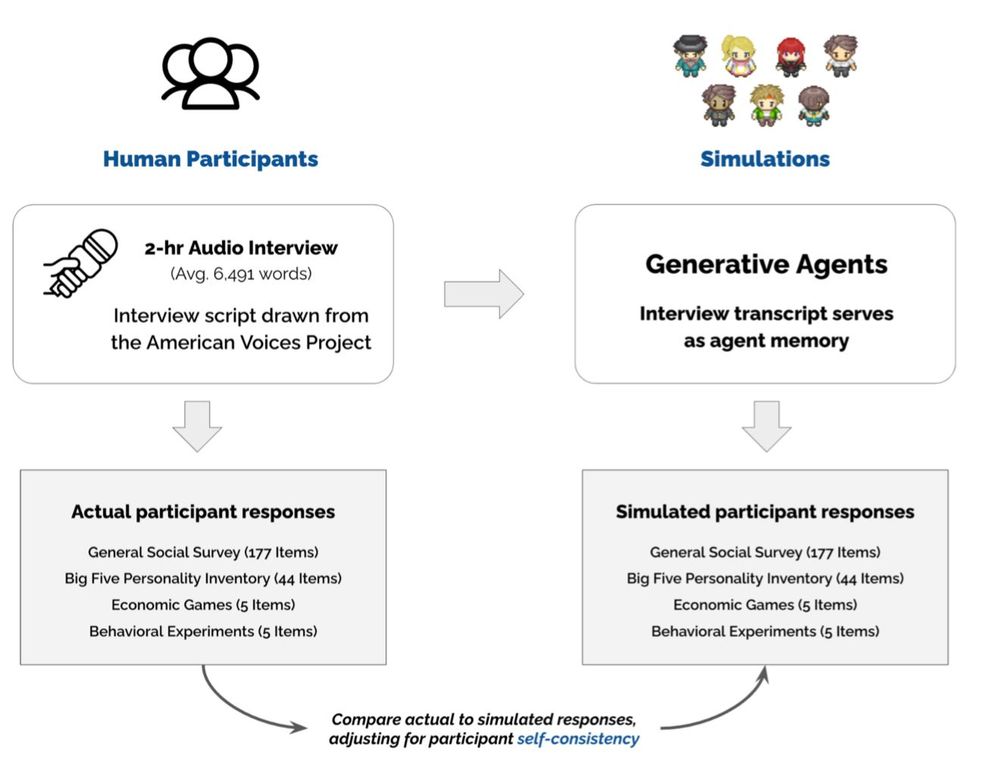
1) Voice-enabled GPT-4o conducted 2 hour
interviews of 1,052 people
2) GPT-4o agents were given the transcripts & prompted to simulate the people
3) The agents were given surveys & tasks. They achieved 85% accuracy in simulating interviewees real answers!

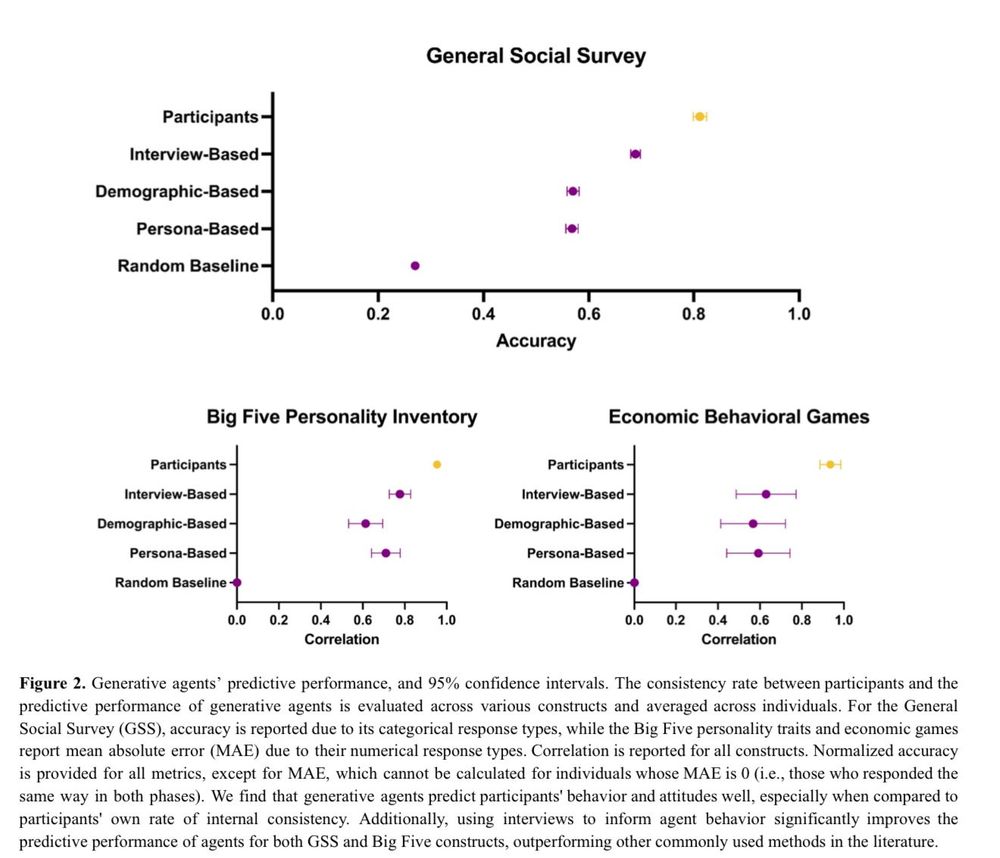
1) Voice-enabled GPT-4o conducted 2 hour
interviews of 1,052 people
2) GPT-4o agents were given the transcripts & prompted to simulate the people
3) The agents were given surveys & tasks. They achieved 85% accuracy in simulating interviewees real answers!
We can now configure FQDN based filtering in Defender Firewall without Intune/Defender for Endpoint?
Looks like we can do create these rules via PowerShell or GPO (likely need to update your ADMX templates)
learn.microsoft.com/en-us/window...

We can now configure FQDN based filtering in Defender Firewall without Intune/Defender for Endpoint?
Looks like we can do create these rules via PowerShell or GPO (likely need to update your ADMX templates)
learn.microsoft.com/en-us/window...
There's also talks going back to 2016 in case you really want to watch a lot of container security videos!
There's also talks going back to 2016 in case you really want to watch a lot of container security videos!
$ websocat "wss://jetstream1.us-east.bsky.network/subscribe?wantedCollections=app.bsky.feed.post" | jq 'select(.commit.record.text != null) | select(.commit.record.text | test("CVE-\\d{4}-\\d+"))'
$ websocat "wss://jetstream1.us-east.bsky.network/subscribe?wantedCollections=app.bsky.feed.post" | jq 'select(.commit.record.text != null) | select(.commit.record.text | test("CVE-\\d{4}-\\d+"))'
at the core of atproto is the data. it lives own your own computer (or someone hosts it for you). think of it as a hard drive with JSON files on it
data is structured (i.e. has a type), and can references other records on other peoples' computer with a URI like a hyperlink

at the core of atproto is the data. it lives own your own computer (or someone hosts it for you). think of it as a hard drive with JSON files on it
data is structured (i.e. has a type), and can references other records on other peoples' computer with a URI like a hyperlink




