Seth Art
@sethsec.bsky.social
Security Research and Advocacy @ Datadog. Former Principal and Cloud Penetration Testing lead @BishopFox. I like to build, break, learn, and share.
CloudFox, CloudFoxable, BadPods, IAM Vulnerable
Reposted by Seth Art
The July edition of the Datadog Security Digest is out!
securitylabs.datadoghq.com/newsletters/...
• Cloud image investigator by @sethsec.bsky.social
• Our top picks for Black Hat / DEF CON
• A benchmark for LLM coding accuracy and security
• Malicious Homebrew installation campaign
.. and more
securitylabs.datadoghq.com/newsletters/...
• Cloud image investigator by @sethsec.bsky.social
• Our top picks for Black Hat / DEF CON
• A benchmark for LLM coding accuracy and security
• Malicious Homebrew installation campaign
.. and more

Preparing for Hacker Summer Camp and a new cloud image investigator | Datadog Security Labs
This month’s digest covers Hacker Summer Camp prep, a new cloud image investigator, and supply-chain vulnerabilities associated with the Open VSX Registry.
securitylabs.datadoghq.com
July 31, 2025 at 9:00 PM
The July edition of the Datadog Security Digest is out!
securitylabs.datadoghq.com/newsletters/...
• Cloud image investigator by @sethsec.bsky.social
• Our top picks for Black Hat / DEF CON
• A benchmark for LLM coding accuracy and security
• Malicious Homebrew installation campaign
.. and more
securitylabs.datadoghq.com/newsletters/...
• Cloud image investigator by @sethsec.bsky.social
• Our top picks for Black Hat / DEF CON
• A benchmark for LLM coding accuracy and security
• Malicious Homebrew installation campaign
.. and more
Reposted by Seth Art
fwd:cloudsec is around the corner! Don't miss these 3 talks from Datadog researchers Seth Sec, Katie Knowles, Greg Foss, and Anthony Randazzo.
fwdcloudsec.org/conference/n...
@sethsec.bsky.social
@siigil.bsky.social
@gregfoss.com
fwdcloudsec.org/conference/n...
@sethsec.bsky.social
@siigil.bsky.social
@gregfoss.com
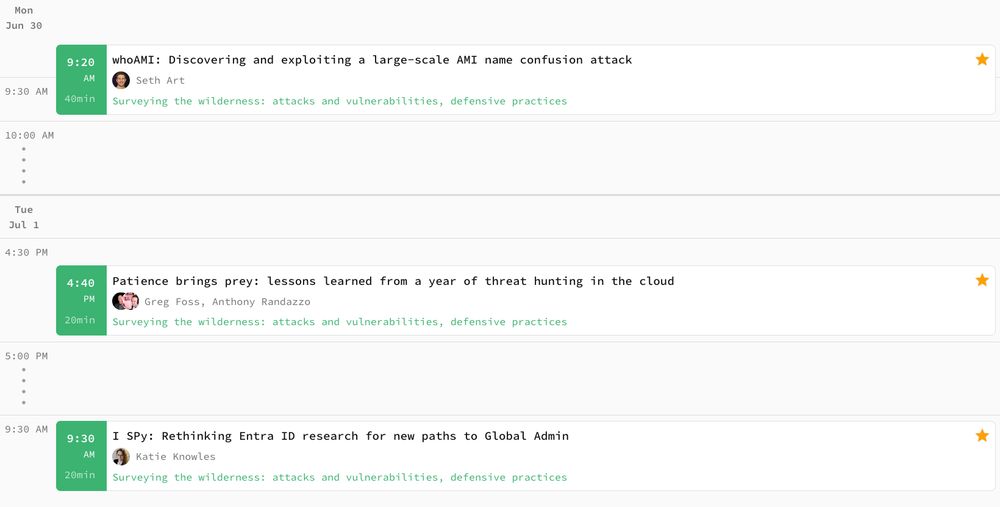
June 27, 2025 at 9:02 PM
fwd:cloudsec is around the corner! Don't miss these 3 talks from Datadog researchers Seth Sec, Katie Knowles, Greg Foss, and Anthony Randazzo.
fwdcloudsec.org/conference/n...
@sethsec.bsky.social
@siigil.bsky.social
@gregfoss.com
fwdcloudsec.org/conference/n...
@sethsec.bsky.social
@siigil.bsky.social
@gregfoss.com
Reposted by Seth Art
The February edition of the Datadog Security Digest is out!
securitylabs.datadoghq.com/newsletters/...
featuring @sethsec.bsky.social, @mccune.org.uk, @karimscloud.bsky.social, @jcfarris.bsky.social, and more
securitylabs.datadoghq.com/newsletters/...
featuring @sethsec.bsky.social, @mccune.org.uk, @karimscloud.bsky.social, @jcfarris.bsky.social, and more

The whoAMI name confusion attack, modern phishing tactics, and K8s network security fundamentals | Datadog Security Labs
This February edition of the Datadog Security Digest dives into the
securitylabs.datadoghq.com
February 27, 2025 at 4:32 PM
The February edition of the Datadog Security Digest is out!
securitylabs.datadoghq.com/newsletters/...
featuring @sethsec.bsky.social, @mccune.org.uk, @karimscloud.bsky.social, @jcfarris.bsky.social, and more
securitylabs.datadoghq.com/newsletters/...
featuring @sethsec.bsky.social, @mccune.org.uk, @karimscloud.bsky.social, @jcfarris.bsky.social, and more
Reposted by Seth Art
The Datadog Security Digest is a monthly, practitioner-focused newsletter.
Don't miss our February edition going live tomorrow!
securitylabs.datadoghq.com/newsletters/...
Don't miss our February edition going live tomorrow!
securitylabs.datadoghq.com/newsletters/...

February 26, 2025 at 11:55 AM
The Datadog Security Digest is a monthly, practitioner-focused newsletter.
Don't miss our February edition going live tomorrow!
securitylabs.datadoghq.com/newsletters/...
Don't miss our February edition going live tomorrow!
securitylabs.datadoghq.com/newsletters/...
Reposted by Seth Art
whoAMI attacks give hackers code execution on Amazon EC2 instances

whoAMI attacks give hackers code execution on Amazon EC2 instances
Security researchers discovered a name confusion attack that allows access to an Amazon Web Services account to anyone that publishes an Amazon Machine Image (AMI) with a specific name.
www.bleepingcomputer.com
February 13, 2025 at 11:59 PM
whoAMI attacks give hackers code execution on Amazon EC2 instances
Reposted by Seth Art
When I first started reading this I though,t “is this really news, this issue has been around for years…” but then it gets interesting - kudos to the researchers on this one!
I’m excited to share our research on the “whoAMI” attack. We discovered that AWS customers pulling AMI IDs insecurely could accidentally use malicious images instead of the legitimate ones— leading to remote code execution.
securitylabs.datadoghq.com/articles/who...
securitylabs.datadoghq.com/articles/who...

whoAMI: A cloud image name confusion attack | Datadog Security Labs
Detailing the discovery and impact of the whoAMI cloud image name confusion attack, which could allow attackers to execute code within AWS accounts due to a vulnerable pattern in AMI retrieval.
securitylabs.datadoghq.com
February 12, 2025 at 8:25 PM
When I first started reading this I though,t “is this really news, this issue has been around for years…” but then it gets interesting - kudos to the researchers on this one!
Reposted by Seth Art
Need to hack thousands of AWS customers? What about on internal AWS systems? Datadog Security Research found that a number of tools, including one published by AWS, are susceptible to name confusion attacks, leading to RCE in vulnerable environments!
securitylabs.datadoghq.com/articles/who...
securitylabs.datadoghq.com/articles/who...

whoAMI: A cloud image name confusion attack | Datadog Security Labs
Detailing the discovery and impact of the whoAMI cloud image name confusion attack, which could allow attackers to execute code within AWS accounts due to a vulnerable pattern in AMI retrieval.
securitylabs.datadoghq.com
February 12, 2025 at 5:19 PM
Need to hack thousands of AWS customers? What about on internal AWS systems? Datadog Security Research found that a number of tools, including one published by AWS, are susceptible to name confusion attacks, leading to RCE in vulnerable environments!
securitylabs.datadoghq.com/articles/who...
securitylabs.datadoghq.com/articles/who...
I’m excited to share our research on the “whoAMI” attack. We discovered that AWS customers pulling AMI IDs insecurely could accidentally use malicious images instead of the legitimate ones— leading to remote code execution.
securitylabs.datadoghq.com/articles/who...
securitylabs.datadoghq.com/articles/who...

whoAMI: A cloud image name confusion attack | Datadog Security Labs
Detailing the discovery and impact of the whoAMI cloud image name confusion attack, which could allow attackers to execute code within AWS accounts due to a vulnerable pattern in AMI retrieval.
securitylabs.datadoghq.com
February 12, 2025 at 4:56 PM
I’m excited to share our research on the “whoAMI” attack. We discovered that AWS customers pulling AMI IDs insecurely could accidentally use malicious images instead of the legitimate ones— leading to remote code execution.
securitylabs.datadoghq.com/articles/who...
securitylabs.datadoghq.com/articles/who...
Reposted by Seth Art
We discovered a pattern in the way many projects retrieve Amazon Machine Images (AMIs), allowing attackers to publish AMIs with specially crafted names and gain code execution within vulnerable accounts.
securitylabs.datadoghq.com/articles/who...
by @sethsec.bsky.social
securitylabs.datadoghq.com/articles/who...
by @sethsec.bsky.social

whoAMI: A cloud image name confusion attack | Datadog Security Labs
Detailing the discovery and impact of the whoAMI cloud image name confusion attack, which could allow attackers to execute code within AWS accounts due to a vulnerable pattern in AMI retrieval.
securitylabs.datadoghq.com
February 12, 2025 at 3:29 PM
We discovered a pattern in the way many projects retrieve Amazon Machine Images (AMIs), allowing attackers to publish AMIs with specially crafted names and gain code execution within vulnerable accounts.
securitylabs.datadoghq.com/articles/who...
by @sethsec.bsky.social
securitylabs.datadoghq.com/articles/who...
by @sethsec.bsky.social
Reposted by Seth Art
New year, new job!
I've joined the amazing @wiz_io research team
My goal is the "work for the security industry, at Wiz"
I wrote a blog post explaining why, and what that means:
ramimac.me/joining-wiz
I've joined the amazing @wiz_io research team
My goal is the "work for the security industry, at Wiz"
I wrote a blog post explaining why, and what that means:
ramimac.me/joining-wiz

🧙 Why I’m Joining Wiz
I’m joining the leading cloud security startup, hoping to “work for the Security Industry, at Wiz.”
ramimac.me
January 28, 2025 at 3:01 PM
New year, new job!
I've joined the amazing @wiz_io research team
My goal is the "work for the security industry, at Wiz"
I wrote a blog post explaining why, and what that means:
ramimac.me/joining-wiz
I've joined the amazing @wiz_io research team
My goal is the "work for the security industry, at Wiz"
I wrote a blog post explaining why, and what that means:
ramimac.me/joining-wiz
Reposted by Seth Art
Reposted by Seth Art
I'm not saying I'm an AWS expert… but I am saying I finally tracked down the random AWS account charging me small amounts every month and closed it.
January 2, 2025 at 8:23 PM
I'm not saying I'm an AWS expert… but I am saying I finally tracked down the random AWS account charging me small amounts every month and closed it.
Reposted by Seth Art
Reposted by Seth Art
Plenty of additional information about the compromise of OpenWRT’s online build service, involving command-injection and hash bypass 🧠
December 8, 2024 at 9:32 PM
Plenty of additional information about the compromise of OpenWRT’s online build service, involving command-injection and hash bypass 🧠
Reposted by Seth Art
Introducing Supply-Chain Firewall: Protecting Developers from Malicious Open Source Packages
securitylabs.datadoghq.com/articles/int... by @ikretz.bsky.social
New open-source tool designed to transparently block known malicious PyPI and npm packages.
github.com/DataDog/supp...
securitylabs.datadoghq.com/articles/int... by @ikretz.bsky.social
New open-source tool designed to transparently block known malicious PyPI and npm packages.
github.com/DataDog/supp...

Introducing Supply-Chain Firewall: Protecting Developers from Malicious Open Source Packages | Datadog Security Labs
Release of Supply-Chain Firewall, an open source tool for preventing the installation of malicious PyPI and npm packages
securitylabs.datadoghq.com
December 6, 2024 at 12:33 PM
Introducing Supply-Chain Firewall: Protecting Developers from Malicious Open Source Packages
securitylabs.datadoghq.com/articles/int... by @ikretz.bsky.social
New open-source tool designed to transparently block known malicious PyPI and npm packages.
github.com/DataDog/supp...
securitylabs.datadoghq.com/articles/int... by @ikretz.bsky.social
New open-source tool designed to transparently block known malicious PyPI and npm packages.
github.com/DataDog/supp...
Reposted by Seth Art
Another cool little tool from Datadog Labs. #cybersecurity
https://github.com/DataDog/supply-chain-firewall
https://github.com/DataDog/supply-chain-firewall
GitHub - DataDog/supply-chain-firewall: A tool for preventing the installation of malicious PyPI and npm packages :fire:
A tool for preventing the installation of malicious PyPI and npm packages :fire: - DataDog/supply-chain-firewall
github.com
December 6, 2024 at 12:43 PM
Another cool little tool from Datadog Labs. #cybersecurity
https://github.com/DataDog/supply-chain-firewall
https://github.com/DataDog/supply-chain-firewall
Reposted by Seth Art
We're now officially on Bluesky!
Expect:
➔ New articles on Security Labs about cloud, container and application security
➔ OSS projects for cloud security practioners
➔ Conference talks at community conferences
See also our starter pack bsky.app/starter-pack... with our authors and researchers!
Expect:
➔ New articles on Security Labs about cloud, container and application security
➔ OSS projects for cloud security practioners
➔ Conference talks at community conferences
See also our starter pack bsky.app/starter-pack... with our authors and researchers!
December 3, 2024 at 2:30 PM
We're now officially on Bluesky!
Expect:
➔ New articles on Security Labs about cloud, container and application security
➔ OSS projects for cloud security practioners
➔ Conference talks at community conferences
See also our starter pack bsky.app/starter-pack... with our authors and researchers!
Expect:
➔ New articles on Security Labs about cloud, container and application security
➔ OSS projects for cloud security practioners
➔ Conference talks at community conferences
See also our starter pack bsky.app/starter-pack... with our authors and researchers!
Reposted by Seth Art
The self described “Shodan of AWS” is now live! This is an amazing project from Daniel Grzelak that helps democratize cloud resource enumeration for the masses. Very excited about this!
awseye.com
awseye.com

Awseye - See Inside AWS Accounts
Awseye tracks publicly accessible AWS data to help identify and secure known and exposed AWS resources. Empowering defenders with open-source intelligence.
awseye.com
November 26, 2024 at 2:31 AM
The self described “Shodan of AWS” is now live! This is an amazing project from Daniel Grzelak that helps democratize cloud resource enumeration for the masses. Very excited about this!
awseye.com
awseye.com
Reposted by Seth Art
DualCore and I spoke at the Red Team Village this year. Here are the slides. QR code with link to gist with all the reference links on last page. Unfortunately it wasn't recorded.
docs.google.com/presentation...
#redteam #purpleteam #redteamvillage
docs.google.com/presentation...
#redteam #purpleteam #redteamvillage
Modern Red Teaming: macOS, K8s, and Cloud - RTV 24 (Public)
Modern Red Teaming: macOS, K8s, and Cloud Carnal0wnage int0x80
docs.google.com
November 24, 2024 at 7:35 PM
DualCore and I spoke at the Red Team Village this year. Here are the slides. QR code with link to gist with all the reference links on last page. Unfortunately it wasn't recorded.
docs.google.com/presentation...
#redteam #purpleteam #redteamvillage
docs.google.com/presentation...
#redteam #purpleteam #redteamvillage
The November edition of the Datadog Security Digest is live!
securitylabs.datadoghq.com/newsletters/...
Featuring:
- Exploring Google Cloud default service accounts: deep dive and real-world adoption trends by Christophe Tafani-Dereeper
🧵(1/3)
securitylabs.datadoghq.com/newsletters/...
Featuring:
- Exploring Google Cloud default service accounts: deep dive and real-world adoption trends by Christophe Tafani-Dereeper
🧵(1/3)

Google Cloud Trends, DPRK npm Threats, & Privilege Escalation Walkthroughs | Datadog Security Labs
In the November edition, read about Google Cloud Trends, DPRK npm Threats, & Privilege Escalation Walkthroughs, and more.
securitylabs.datadoghq.com
November 22, 2024 at 7:40 PM
The November edition of the Datadog Security Digest is live!
securitylabs.datadoghq.com/newsletters/...
Featuring:
- Exploring Google Cloud default service accounts: deep dive and real-world adoption trends by Christophe Tafani-Dereeper
🧵(1/3)
securitylabs.datadoghq.com/newsletters/...
Featuring:
- Exploring Google Cloud default service accounts: deep dive and real-world adoption trends by Christophe Tafani-Dereeper
🧵(1/3)
Reposted by Seth Art
Latest video in my Kubernetes Security Fundamentals series is out. Looking at some lesser known bits of Kubernetes authentication, bootstrap and static tokens!
youtu.be/1QNKj1rW5H0?...
youtu.be/1QNKj1rW5H0?...

Kubernetes Security Fundamentals: Authentication - Part 2
YouTube video by Datadog
youtu.be
November 21, 2024 at 10:00 AM
Latest video in my Kubernetes Security Fundamentals series is out. Looking at some lesser known bits of Kubernetes authentication, bootstrap and static tokens!
youtu.be/1QNKj1rW5H0?...
youtu.be/1QNKj1rW5H0?...
Reposted by Seth Art
Now as a starter pack: go.bsky.app/5HpWAcM
Cloud Security
Join the conversation
go.bsky.app
November 18, 2024 at 3:40 PM
Now as a starter pack: go.bsky.app/5HpWAcM
Reposted by Seth Art
We made it easy for you to find us!
The Red Siege Starter Pack is now up!
Find the team here - go.bsky.app/ERU72bD
#infosec #cybersecurity
The Red Siege Starter Pack is now up!
Find the team here - go.bsky.app/ERU72bD
#infosec #cybersecurity

November 19, 2024 at 3:37 PM
We made it easy for you to find us!
The Red Siege Starter Pack is now up!
Find the team here - go.bsky.app/ERU72bD
#infosec #cybersecurity
The Red Siege Starter Pack is now up!
Find the team here - go.bsky.app/ERU72bD
#infosec #cybersecurity
Reposted by Seth Art
This is such a good story about how "gotofail" started as a drunken brag in a bar and ended up being disclosed to Apple via a burner phone. It was Ryan all along, finally taking credit after all these years!
Oh, I never posted my gotofail story on here.
Early 2014, someone came to me about a catastrophic vulnerability in Apple's TLS implementation.
I shit you not, they'd overheard someone at a bar drunkenly bragging about how they were going to sell it to a FVEY intelligence agency for six figures.
Early 2014, someone came to me about a catastrophic vulnerability in Apple's TLS implementation.
I shit you not, they'd overheard someone at a bar drunkenly bragging about how they were going to sell it to a FVEY intelligence agency for six figures.
November 18, 2024 at 10:53 AM
This is such a good story about how "gotofail" started as a drunken brag in a bar and ended up being disclosed to Apple via a burner phone. It was Ryan all along, finally taking credit after all these years!
Reposted by Seth Art
I created a list of Cloud Security folks on here. bsky.app/profile/scot...
November 18, 2024 at 12:57 AM
I created a list of Cloud Security folks on here. bsky.app/profile/scot...