buff.ly/agWWCnp

buff.ly/agWWCnp


Introduction: A Threat That Refuses to Fade QuasarRAT has been circulating through the cyber underworld for more than a decade, yet its influence has not diminished. Instead, it has evolved into one of the most persistent tools in…

Introduction: A Threat That Refuses to Fade QuasarRAT has been circulating through the cyber underworld for more than a decade, yet its influence has not diminished. Instead, it has evolved into one of the most persistent tools in…

Technical walkthrough on extracting encrypted configurations from both clean and obfuscated samples of the QuasarRAT .NET malware.
-
IOCs: (None identified)
-
#QuasarRAT #RAT #ThreatIntel
Technical walkthrough on extracting encrypted configurations from both clean and obfuscated samples of the QuasarRAT .NET malware.
-
IOCs: (None identified)
-
#QuasarRAT #RAT #ThreatIntel
https://platform.censys.io/hosts/185.208.159.161
https://search.censys.io/hosts/185.208.159.161
#malware #thread 🧵


https://platform.censys.io/hosts/185.208.159.161
https://search.censys.io/hosts/185.208.159.161
#malware #thread 🧵
#AI #LLM #malware #phishing #QuasarRAT #RevengeHotels #TA558 #VenomRAT
www.matricedigitale.it/2025/09/17/r...

#AI #LLM #malware #phishing #QuasarRAT #RevengeHotels #TA558 #VenomRAT
www.matricedigitale.it/2025/09/17/r...
DarkSamural’s false-flag tactics used Vietnamese branding to obscure Patchwork’s role. The group deployed tools like BADNEWS, QuasarRAT & Mythic to evade defenses. South Asian orgs must harden email filtering & detection.
#Patchwork #ThreatIntel #Malware #Infosec #APT
DarkSamural’s false-flag tactics used Vietnamese branding to obscure Patchwork’s role. The group deployed tools like BADNEWS, QuasarRAT & Mythic to evade defenses. South Asian orgs must harden email filtering & detection.
#Patchwork #ThreatIntel #Malware #Infosec #APT
http://episode-windsor-subdivision-delivery.trycloudflare\\.com
https://lol-julian-impossible-bermuda.trycloudflare\\.com
https://italia-committees-practical-violence.trycloudflare\\.com
#AsyncRAT #purehvnc #quasarrat
jskeywon […]
[Original post on infosec.exchange]



http://episode-windsor-subdivision-delivery.trycloudflare\\.com
https://lol-julian-impossible-bermuda.trycloudflare\\.com
https://italia-committees-practical-violence.trycloudflare\\.com
#AsyncRAT #purehvnc #quasarrat
jskeywon […]
[Original post on infosec.exchange]
#AsyncRAT #QuasarRAT
www.welivesecurity.com/en/eset-rese...
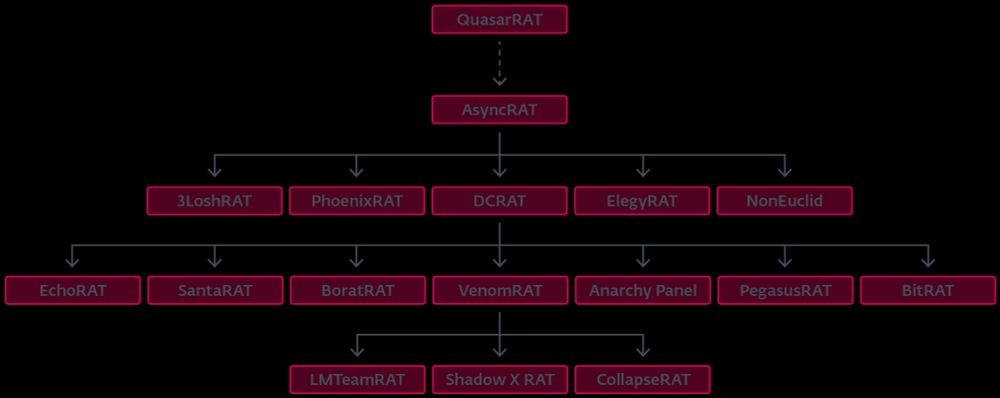
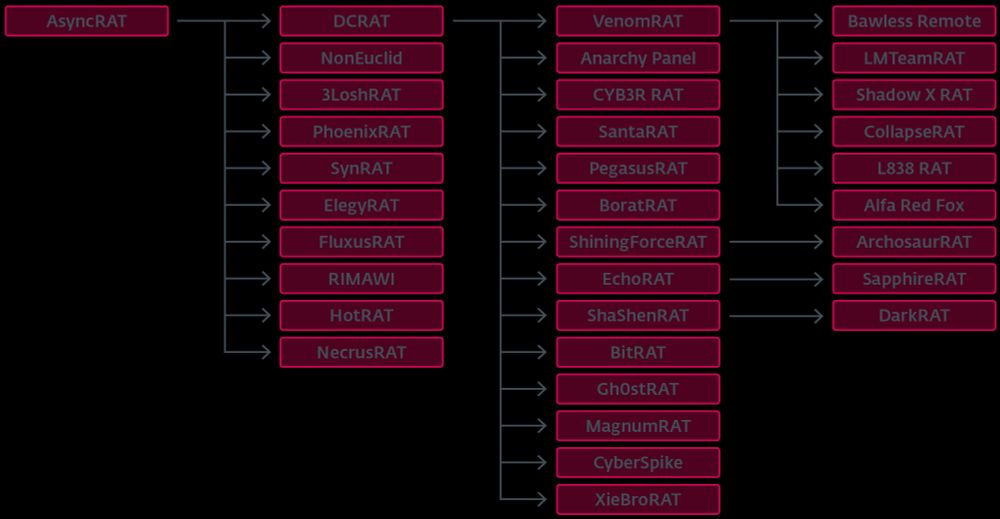
#AsyncRAT #QuasarRAT
www.welivesecurity.com/en/eset-rese...
#hackers #PHP #PHPflaw #quasarRAT #remoteaccesstrojan #XMRigminers #cyberattacks

#hackers #PHP #PHPflaw #quasarRAT #remoteaccesstrojan #XMRigminers #cyberattacks
Please report them to centralpki@microsoft[.com or just tag me at a minimum, please.
Microsoft has been good at revoking them
This week I saw
Lumma Infostealer
QuasarRAT
CobaltStrike (C2: uuuqf[.]com)
www.virustotal.com/gui/file/401...
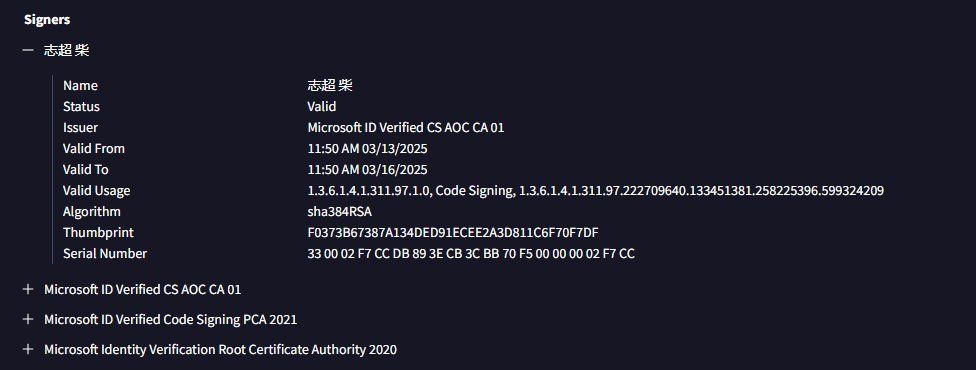
Please report them to centralpki@microsoft[.com or just tag me at a minimum, please.
Microsoft has been good at revoking them
This week I saw
Lumma Infostealer
QuasarRAT
CobaltStrike (C2: uuuqf[.]com)
www.virustotal.com/gui/file/401...
#NPMpackage #disguised #Ethereumtool #QuasarRAT #RAT #remoteaccesstrojan #cybersecurity #cybersec #cyberattacks
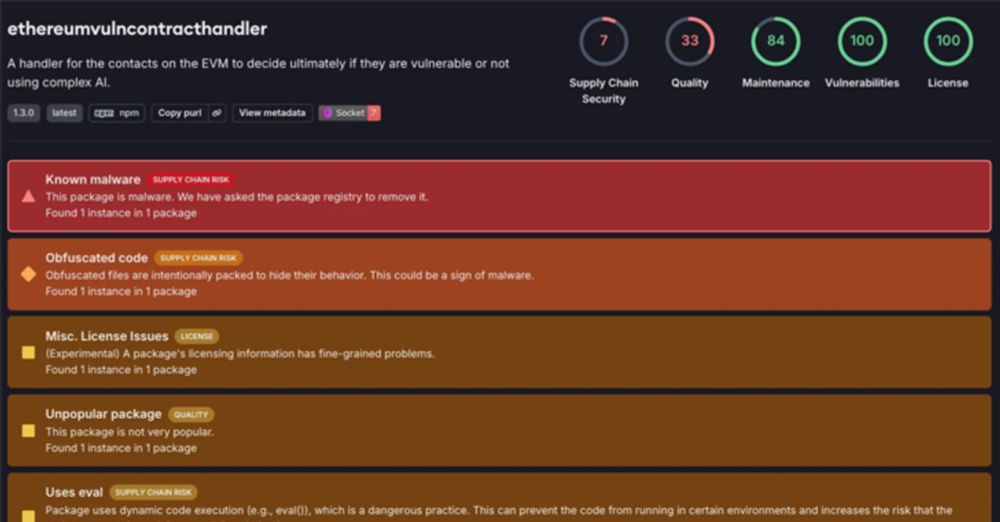
#NPMpackage #disguised #Ethereumtool #QuasarRAT #RAT #remoteaccesstrojan #cybersecurity #cybersec #cyberattacks
Read: hackread.com/npm-package-...
#CyberSecurity #NPM #Malware #Ethereum

Read: hackread.com/npm-package-...
#CyberSecurity #NPM #Malware #Ethereum
#cybersecurity #ethereum #malevolo #npm #pacchettonpm #QuasarRAT #supplychain
www.matricedigitale.it/sicurezza-in...

#cybersecurity #ethereum #malevolo #npm #pacchettonpm #QuasarRAT #supplychain
www.matricedigitale.it/sicurezza-in...

blog.talosintelligence.com/lilacsquid/

blog.talosintelligence.com/lilacsquid/

svchost in PDB:
BALLCONTROL
TREASUREMAP
GhostShell
TAIDOOR
EternalRocks
svchost in OriginalFilename:
Zebrocy
CASPER
GH0ST_RAT
MarkiRAT
GhostEmperor
Skipper
svchost in DLLName:
QUASARRAT
DUSTPAN
TAIDOOR
SIG31
QUICKHEAL
TypeHash
XDll
Carbon
Uroburos
svchost in PDB:
BALLCONTROL
TREASUREMAP
GhostShell
TAIDOOR
EternalRocks
svchost in OriginalFilename:
Zebrocy
CASPER
GH0ST_RAT
MarkiRAT
GhostEmperor
Skipper
svchost in DLLName:
QUASARRAT
DUSTPAN
TAIDOOR
SIG31
QUICKHEAL
TypeHash
XDll
Carbon
Uroburos

