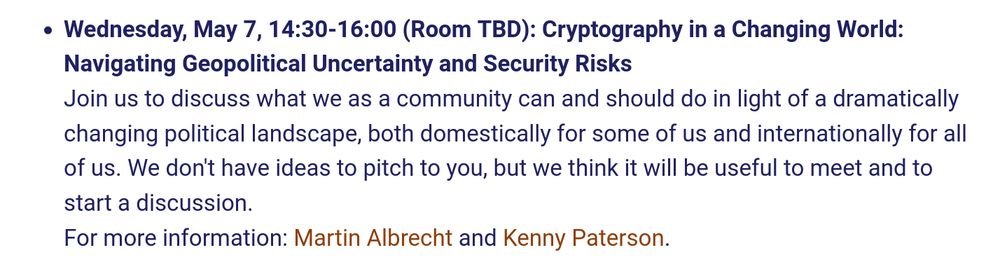
support.apple.com/en-us/122756
support.apple.com/en-us/122756
Congratulations to the authors on their IACR grant slam of breaks :)


Congratulations to the authors on their IACR grant slam of breaks :)
Yet here we are.
Yet here we are.
(And @schollster.bsky.social will present it at S&P 2025!)
A summary 🧵


(And @schollster.bsky.social will present it at S&P 2025!)
A summary 🧵
conference.sdo.esoc.esa.int/proceedings/...
#cryptography
conference.sdo.esoc.esa.int/proceedings/...
#cryptography




So, who despite US Americans and Russians do you think will go at this point?

So, who despite US Americans and Russians do you think will go at this point?

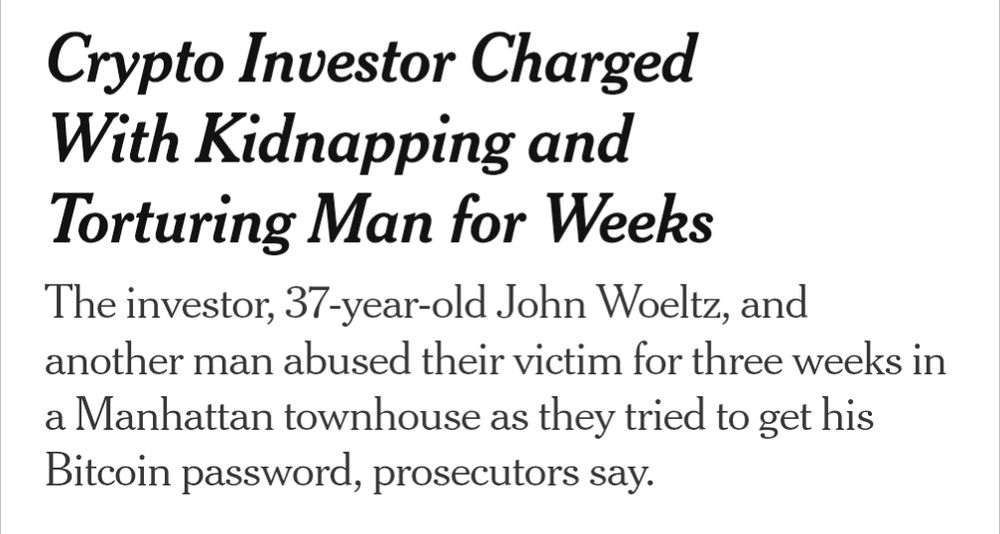
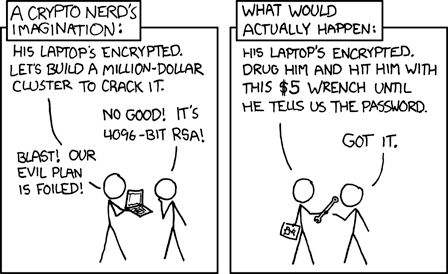
Despite the obvious trainwreck that this news is (but not surprising), I'd like to thank them all for some extra material I'll teach tomorrow in a course about private communication :)
Despite the obvious trainwreck that this news is (but not surprising), I'd like to thank them all for some extra material I'll teach tomorrow in a course about private communication :)