
More at edwincovert.com


www.theatlantic.com/politics/202...

www.theatlantic.com/politics/202...

Man repeatedly begs agents to look at his digital passport ID—they refuse.
Drove him 7 miles away before releasing him alone into Minnesota snow storm—told him to "walk home" in freezing weather advisory.






“I didn’t say that, you said that. Fake news.”
5 days apart 😬
(From @therecount.com )
“I didn’t say that, you said that. Fake news.”
5 days apart 😬
(From @therecount.com )
John Lewis explores the Supreme Court's handling of the litigation challenging the Trump administration’s funding actions.

John Lewis explores the Supreme Court's handling of the litigation challenging the Trump administration’s funding actions.
Ah, no.
Ah, no.
IP data is being shared in Vulnerable HTTP reports: www.shadowserver.org/what-we-do/n...
Dashboard geo breakdown: dashboard.shadowserver.org/statistics/c...
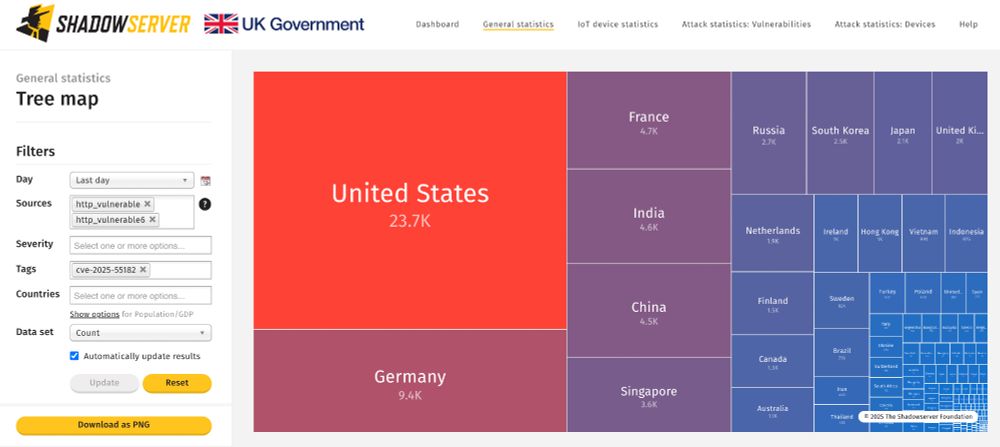
IP data is being shared in Vulnerable HTTP reports: www.shadowserver.org/what-we-do/n...
Dashboard geo breakdown: dashboard.shadowserver.org/statistics/c...
Winter is coming. Not all weather offices are ready.
www.washingtonpost.com/weather/2025...

Winter is coming. Not all weather offices are ready.
www.washingtonpost.com/weather/2025...
Thursday: here's new floor plans for a golden ballroom expansion
Thursday: here's new floor plans for a golden ballroom expansion







