
Anyhow, Timbernetes (v1.35.0 of Kubernetes) was released yesterday and I've updated my port for illumos, FreeBSD and OpenBSD...
#kubernetes #homelab #illumos #freebsd #openbsd
github.com/tnorlin/kube...

Anyhow, Timbernetes (v1.35.0 of Kubernetes) was released yesterday and I've updated my port for illumos, FreeBSD and OpenBSD...
#kubernetes #homelab #illumos #freebsd #openbsd
github.com/tnorlin/kube...
If you couldn't attend or want to catch a detail you missed, the full playlist is here ➡️ www.youtube.com/watch?v=4Y8f...
#KubeCon #Cilium #CloudNative

If you couldn't attend or want to catch a detail you missed, the full playlist is here ➡️ www.youtube.com/watch?v=4Y8f...
#KubeCon #Cilium #CloudNative


bookshop.org/p/books/cont...

bookshop.org/p/books/cont...
github.com/tnorlin/kube...
#kubernetes #homelab #illumos #freebsd #openbsd

github.com/tnorlin/kube...
#kubernetes #homelab #illumos #freebsd #openbsd
This time it breaks for me:
+++ [0827 17:47:48] Building go targets for illumos/amd64
k8s.io/kubernetes/cmd/kube-apiserver (static)
# k8s.io/kubernetes/pkg/securitycontext
pkg/securitycontext/util.go:212:23: undefined: possibleCPUs
This time it breaks for me:
+++ [0827 17:47:48] Building go targets for illumos/amd64
k8s.io/kubernetes/cmd/kube-apiserver (static)
# k8s.io/kubernetes/pkg/securitycontext
pkg/securitycontext/util.go:212:23: undefined: possibleCPUs

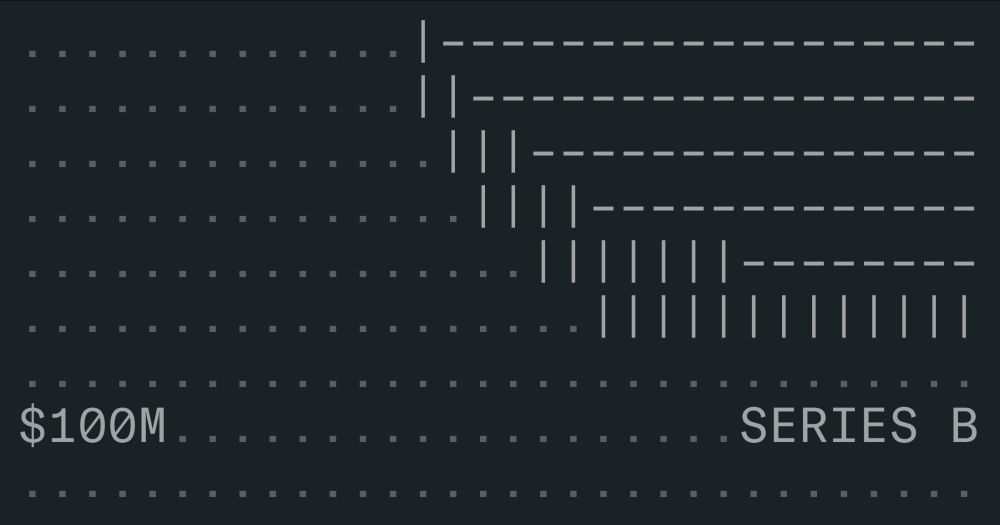
oxide.computer/blog/our-100...
Well, it was very evident that he never visited Sweden. Five minutes were like five days in Grosseto. 🦟
Well, it was very evident that he never visited Sweden. Five minutes were like five days in Grosseto. 🦟
What’s working? What’s not? What should we tackle next? Take our short survey and help shape what comes next.
➡️ Take the survey sidero.surveysparrow.com/s/talosuseq2...
#TalosLinux

What’s working? What’s not? What should we tackle next? Take our short survey and help shape what comes next.
➡️ Take the survey sidero.surveysparrow.com/s/talosuseq2...
#TalosLinux
RIP Ozzy

RIP Ozzy

Anyone have recommendations for self-hosted video doorbells that don't suck?

Anyone have recommendations for self-hosted video doorbells that don't suck?

I've had a technical debt since "a while" - my primary WAN is on pfSense (in bhyve in OmniOS).. but I think it's about time now to do something about it. OPNSense is my natural contestant for running in a virtual appliance..
I've had a technical debt since "a while" - my primary WAN is on pfSense (in bhyve in OmniOS).. but I think it's about time now to do something about it. OPNSense is my natural contestant for running in a virtual appliance..


