Martin R. Albrecht
@malb.bsky.social
820 followers
300 following
91 posts
Cryptography Professor at King's College London and Principal Research Scientist at SandboxAQ. Erdős–Bacon Number: 6. He/him or they/them.
https://malb.io
Posts
Media
Videos
Starter Packs
Martin R. Albrecht
@malb.bsky.social
· Aug 27

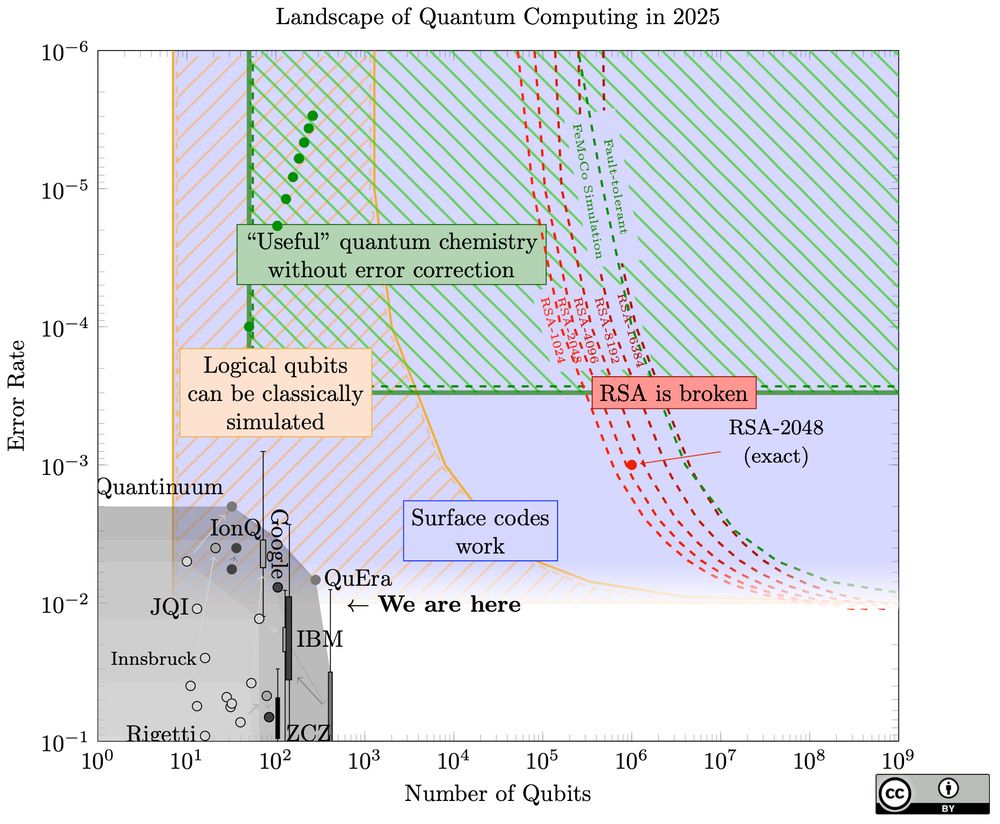
Internship Position on the Lattice Estimator
Eamonn and I are looking to hire an intern for four months to work on the Lattice Estimator. The internship will be based at King’s College London and is funded by a gift from Zama. We are ideally …
martinralbrecht.wordpress.com
Reposted by Martin R. Albrecht
Martin R. Albrecht
@malb.bsky.social
· Aug 25

Postdoc Position in Lattice-Based Cryptography
We are recruiting a postdoc to work with us on “practical advanced post-quantum cryptography from lattices”, the title of my ERC selected, UKRI Frontier Research funded project: Standardisation eff…
martinralbrecht.wordpress.com
Reposted by Martin R. Albrecht
Reposted by Martin R. Albrecht
Martin R. Albrecht
@malb.bsky.social
· Jun 14

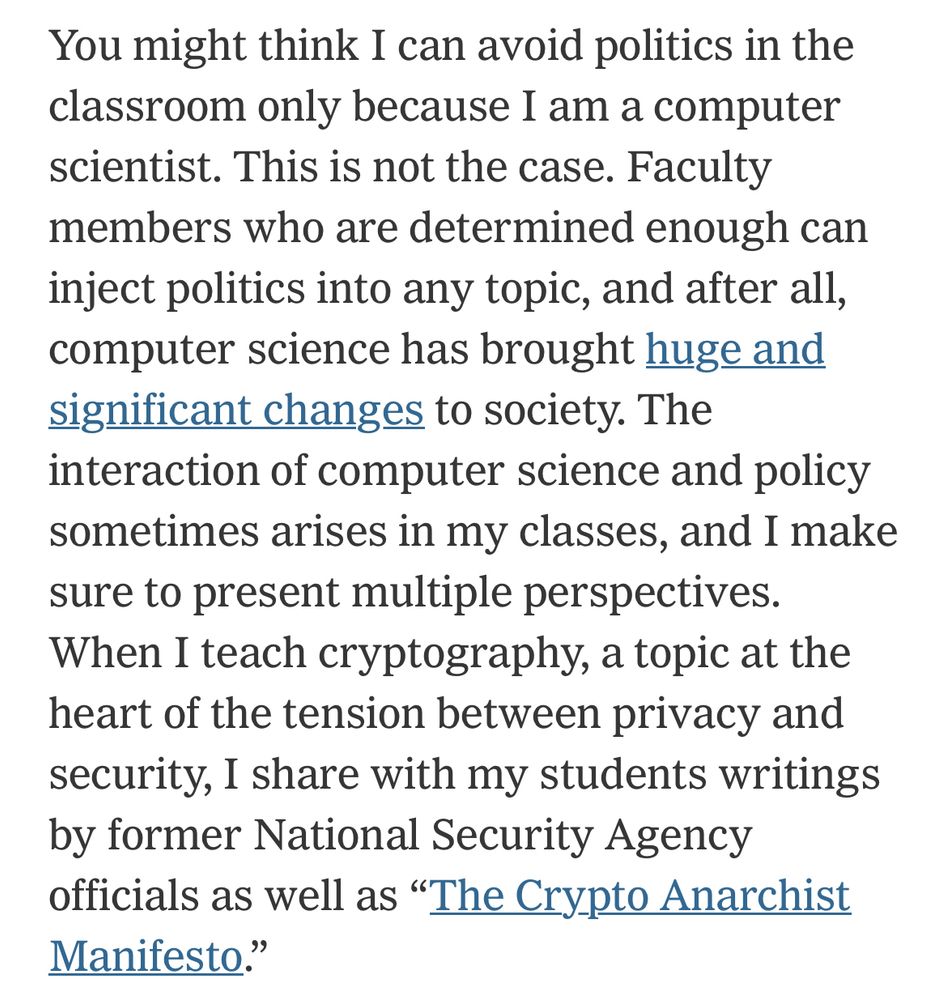
On the Virtues of Information Security in the UK Climate Movement
Our paper – titled “On the Virtues of Information Security in the UK Climate Movement” – was accepted at USENIX Security’25. Here’s the abstract: We report on an ethnographic study with members of …
martinralbrecht.wordpress.com
Reposted by Martin R. Albrecht
Martin R. Albrecht
@malb.bsky.social
· Apr 15
Martin R. Albrecht
@malb.bsky.social
· May 15
Martin R. Albrecht
@malb.bsky.social
· May 8
Reposted by Martin R. Albrecht
Reposted by Martin R. Albrecht
Kenny Paterson
@kennyog.bsky.social
· May 4
Reposted by Martin R. Albrecht
Reposted by Martin R. Albrecht
Reposted by Martin R. Albrecht
Reposted by Martin R. Albrecht
Durham UCU
@ducu.bsky.social
· Apr 29
Reposted by Martin R. Albrecht