
beckystern.com/2025/05/25/s...

beckystern.com/2025/05/25/s...
files.speakerdeck.com/presentation...
files.speakerdeck.com/presentation...
bit.ly/datadog-detect
Our lineup is incredible with experts in the field of detection, response and threat intelligence.

bit.ly/datadog-detect
Our lineup is incredible with experts in the field of detection, response and threat intelligence.
Absolutely love this resource 💙
Just came across this gem from JPCERT
👉 jpcertcc.github.io/ToolAnalysis...
It maps forensic artifacts left behind by tools used for lateral movement or credential dumping. Super detailed.
Absolutely love this resource 💙
Just came across this gem from JPCERT
👉 jpcertcc.github.io/ToolAnalysis...
It maps forensic artifacts left behind by tools used for lateral movement or credential dumping. Super detailed.

Connect-ExchangeOnline
Get-MailboxAuditBypassAssociation -ResultSize Unlimited | Where-Object { $_.AuditBypassEnabled -eq $true }
To alert, try:
CloudAppEvents
| where ActionType == @"Set-MailboxAuditBypassAssociation"

Connect-ExchangeOnline
Get-MailboxAuditBypassAssociation -ResultSize Unlimited | Where-Object { $_.AuditBypassEnabled -eq $true }
To alert, try:
CloudAppEvents
| where ActionType == @"Set-MailboxAuditBypassAssociation"

www.microsoft.com/en-us/securi...

www.microsoft.com/en-us/securi...




www.microsoft.com/en-us/securi...
#security #microsoft #entra #identity
#

www.microsoft.com/en-us/securi...
#security #microsoft #entra #identity
#
You MUST defend against modern cloud phishing techniques for INITIAL ACCCESS. Here are 4 of the top vectors when MFA is enforced:
You MUST defend against modern cloud phishing techniques for INITIAL ACCCESS. Here are 4 of the top vectors when MFA is enforced:
posts.specterops.io/attacking-en...

posts.specterops.io/attacking-en...
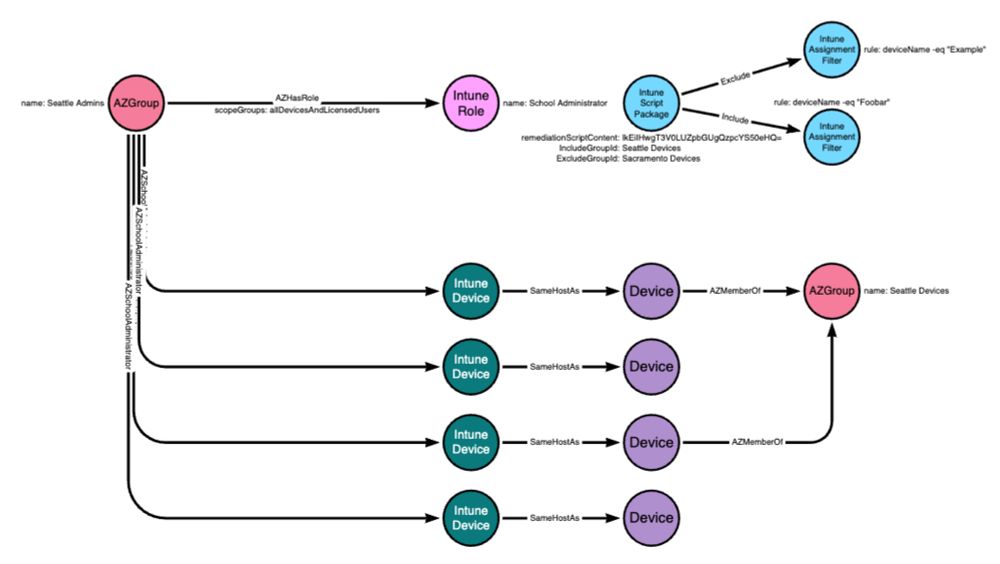
github.com/cisagov/kev-...
Via Socket: socket.dev/blog/cisa-br...

github.com/cisagov/kev-...
Via Socket: socket.dev/blog/cisa-br...
As of right now, there were 372 *publicly reported* ransomware attacks against healthcare providers in 2024. Currently down from 2023 (377). BUT there can be a 1-2 month delay in reporting, so the final number will increase.

As of right now, there were 372 *publicly reported* ransomware attacks against healthcare providers in 2024. Currently down from 2023 (377). BUT there can be a 1-2 month delay in reporting, so the final number will increase.

The report includes KQL, SPL and Powershell code to perform incident response.
www.cisa.gov/resources-to...
The report includes KQL, SPL and Powershell code to perform incident response.
www.cisa.gov/resources-to...
#MicrosoftSentinel #Cybersecurity #MicrosoftSecurity #Security #DefenderXDR
#MicrosoftSentinel #Cybersecurity #MicrosoftSecurity #Security #DefenderXDR
It'll be on malware analysis. It covers everything you need to know to get started and even some advanced topics!
🔗Follow here so you don't miss it:

It'll be on malware analysis. It covers everything you need to know to get started and even some advanced topics!
🔗Follow here so you don't miss it:


