или платит чей-то ботнет.
Модель «подарка с крючком» 90% «кряков» и «лоадеров» -это:
loader + stealer,
loader + dropper,
loader + C2 beacon.
или платит чей-то ботнет.
Модель «подарка с крючком» 90% «кряков» и «лоадеров» -это:
loader + stealer,
loader + dropper,
loader + C2 beacon.
This is ~1 new Rust malware family per month. Rust as a programming language for malware is here to stay!
This is ~1 new Rust malware family per month. Rust as a programming language for malware is here to stay!
#Malware #C2 #Credential #Theft #Downloader
Origin | Interest | Match

#Malware #C2 #Credential #Theft #Downloader
Origin | Interest | Match
Details at github.com/malware-traf...




Details at github.com/malware-traf...
PhantomVAI Loader uses phishing and steganography to deliver multiple infostealers like Katz Stealer, AsyncRAT, and XWorm.
-
IOCs: (None identified)
-
#Infostealer #Malware #PhantomVAI #ThreatIntel
PhantomVAI Loader uses phishing and steganography to deliver multiple infostealers like Katz Stealer, AsyncRAT, and XWorm.
-
IOCs: (None identified)
-
#Infostealer #Malware #PhantomVAI #ThreatIntel

#ClickFix #LummaStealer #MonsterV2 #Proofpoint #Rhadamanthys #TA585
www.matricedigitale.it/2025/10/14/t...

#ClickFix #LummaStealer #MonsterV2 #Proofpoint #Rhadamanthys #TA585
www.matricedigitale.it/2025/10/14/t...
⚡️Has capabilities of a remote access trojan (RAT), loader, and stealer
⚡️ Avoids infecting computers in Commonwealth of Independent States (CIS) countries
⚡️ Expensive compared to its peer malware families
⚡️ Used by TA585 and a small number of actors
⚡️Has capabilities of a remote access trojan (RAT), loader, and stealer
⚡️ Avoids infecting computers in Commonwealth of Independent States (CIS) countries
⚡️ Expensive compared to its peer malware families
⚡️ Used by TA585 and a small number of actors
Not sure what type of #malware this is, but it's not Koi Stealer.
Details at github.com/malware-traf...




Not sure what type of #malware this is, but it's not Koi Stealer.
Details at github.com/malware-traf...

North Korean-aligned APT37 is using a new Rust-based backdoor (Rustonotto) and a Python loader to deploy the FadeStealer info-stealer.
-
IOCs: Rustonotto, FadeStealer
-
#APT37 #Malware #Rust #ThreatIntel
North Korean-aligned APT37 is using a new Rust-based backdoor (Rustonotto) and a Python loader to deploy the FadeStealer info-stealer.
-
IOCs: Rustonotto, FadeStealer
-
#APT37 #Malware #Rust #ThreatIntel
✅ Stealer can now be launched on all or selected bots
⚙️ Loader speed improved
🐞 Bug fix for browser cookie theft on high-handle systems
📌 Rebuild required – expect fresh variants in the wild
#ThreatIntel #Malware #HVNC #Infostealer

✅ Stealer can now be launched on all or selected bots
⚙️ Loader speed improved
🐞 Bug fix for browser cookie theft on high-handle systems
📌 Rebuild required – expect fresh variants in the wild
#ThreatIntel #Malware #HVNC #Infostealer
#ARECHCLIENT2 #INFOSTEALER #Lumma #Rhadamanthys #SHELLTER
www.matricedigitale.it/2025/07/08/s...

#ARECHCLIENT2 #INFOSTEALER #Lumma #Rhadamanthys #SHELLTER
www.matricedigitale.it/2025/07/08/s...
Highly modular & stealthy malware targeting over 110 browsers, 70+ apps (incl. wallets & 2FA), and 250+ extensions.
Server-side decryption
Custom shellcode & morpher
Loader included
Cookie theft w/o killing processes
#CyberSecurity #ThreatIntel #Malware #InfoStealer


Highly modular & stealthy malware targeting over 110 browsers, 70+ apps (incl. wallets & 2FA), and 250+ extensions.
Server-side decryption
Custom shellcode & morpher
Loader included
Cookie theft w/o killing processes
#CyberSecurity #ThreatIntel #Malware #InfoStealer
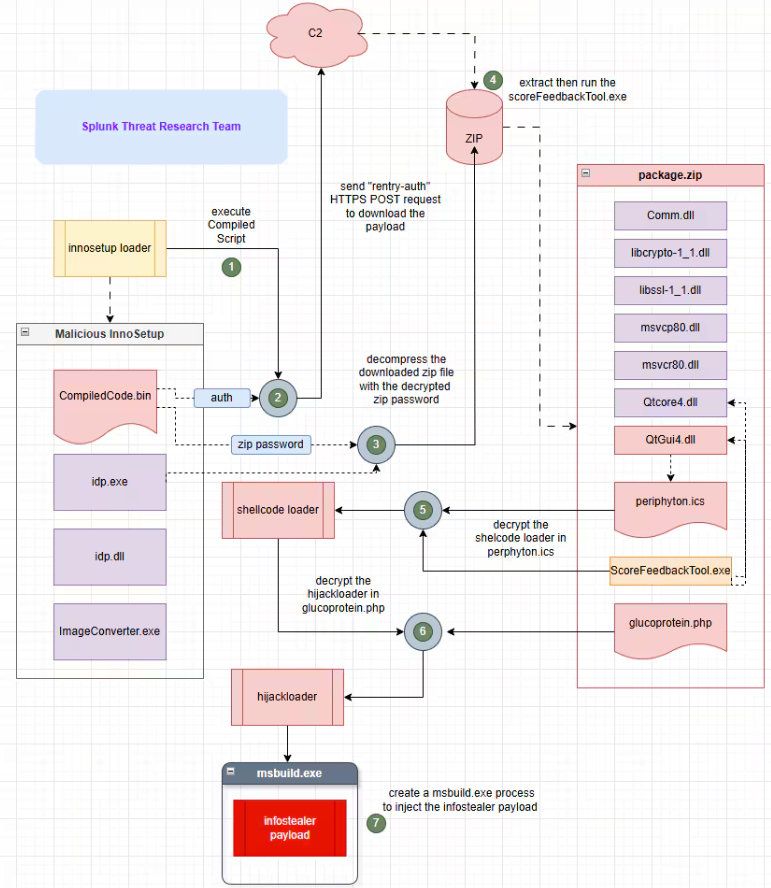
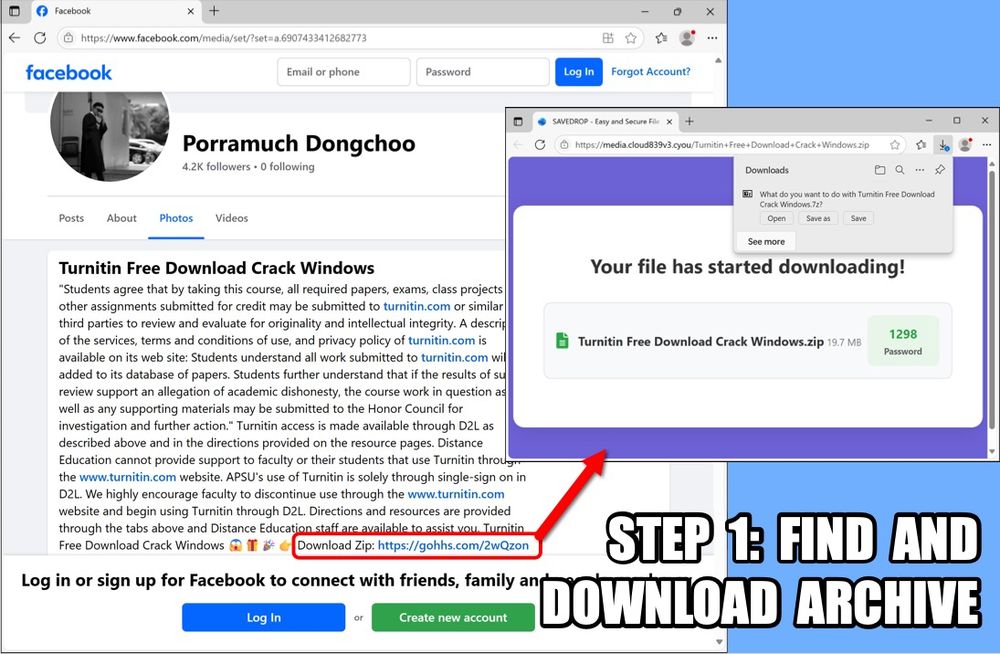
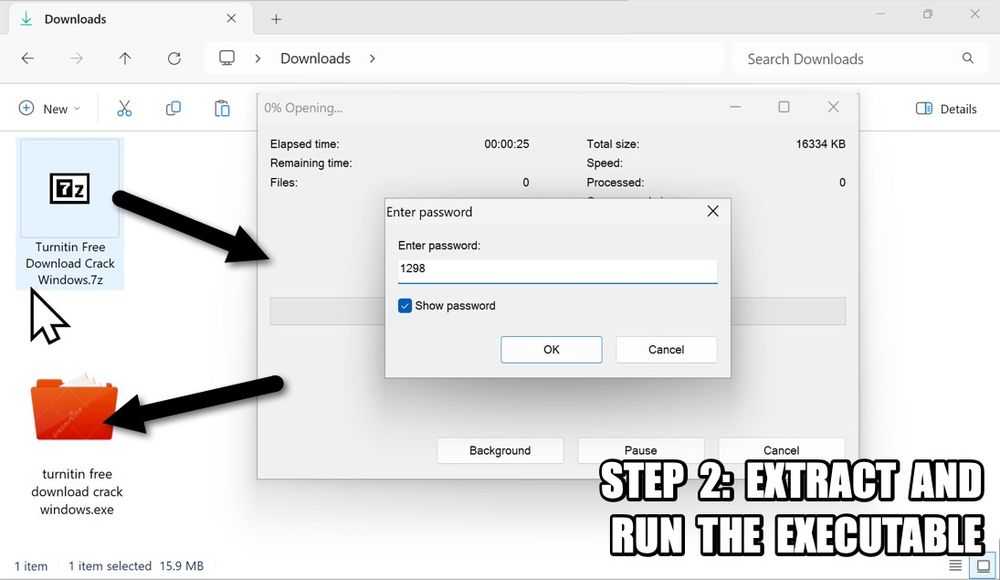
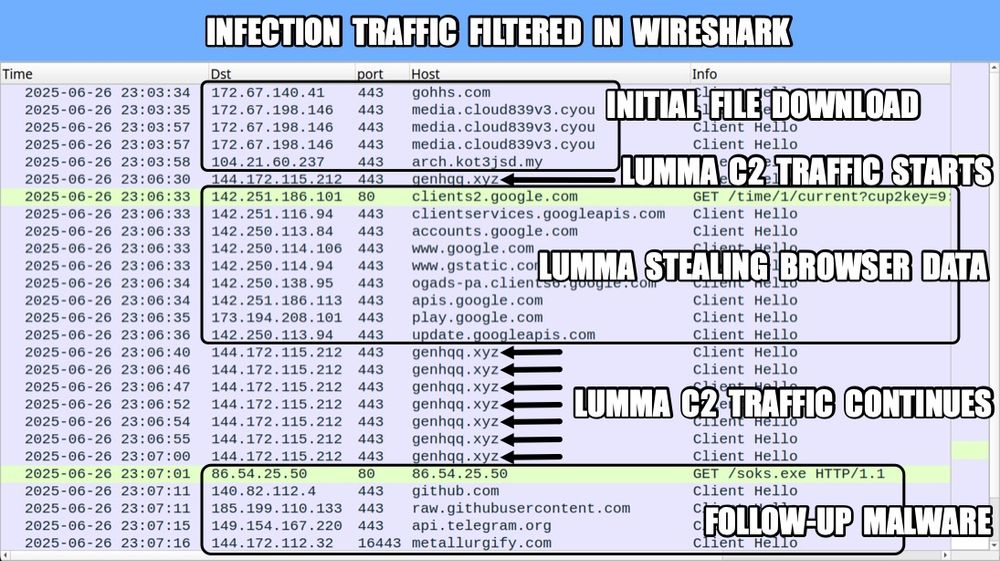
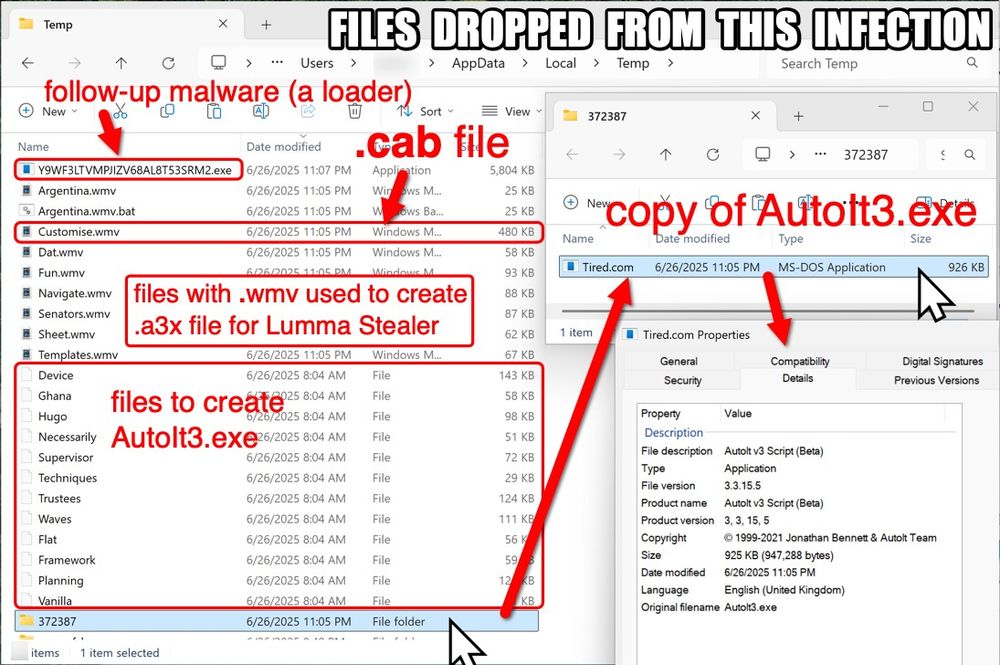

0 VT detections on any component of the malware loader.
Proofpoint rules detect the outbound C2 traffic.
My Yara rule detects the installer.

0 VT detections on any component of the malware loader.
Proofpoint rules detect the outbound C2 traffic.
My Yara rule detects the installer.

Example of downloaded zip available at:
- bazaar.abuse.ch/sample/35236...
- tria.ge/250510-a2fw5...
- app.any.run/tasks/3adefb...

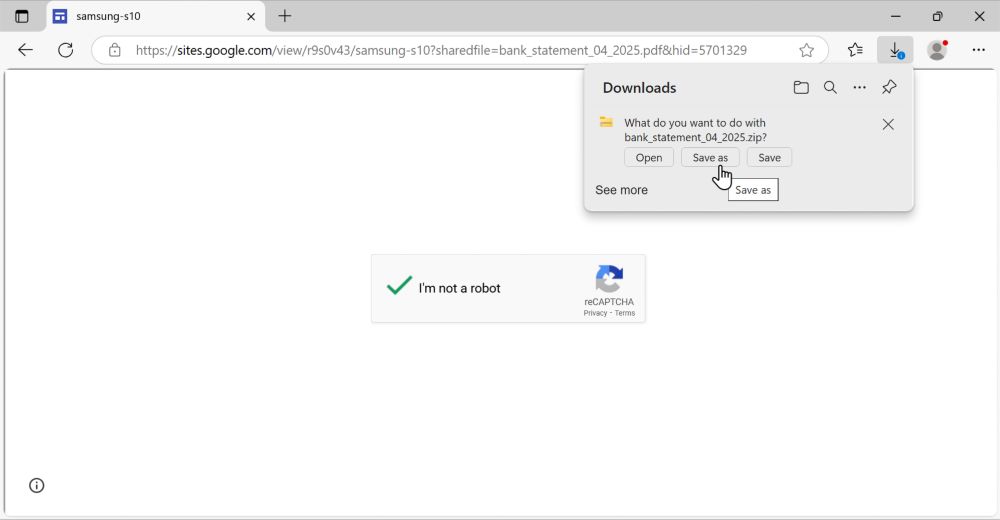

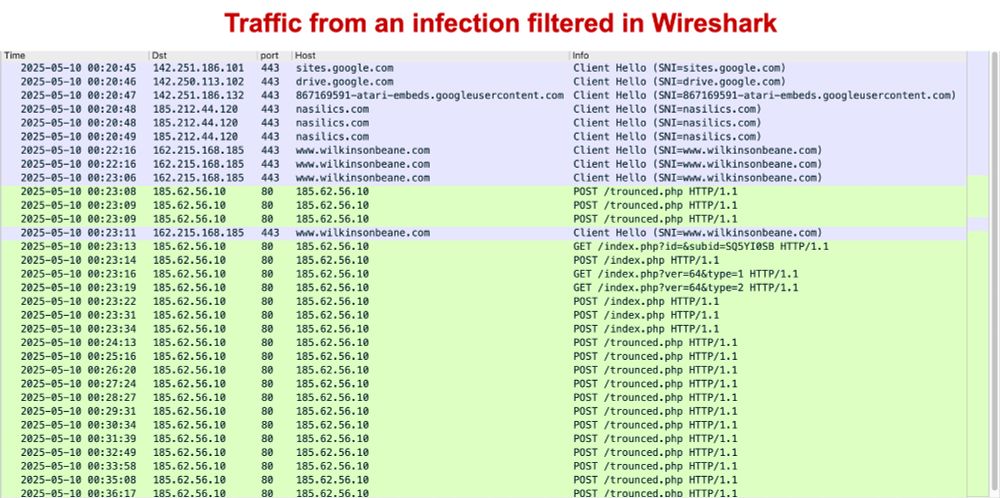
Example of downloaded zip available at:
- bazaar.abuse.ch/sample/35236...
- tria.ge/250510-a2fw5...
- app.any.run/tasks/3adefb...

